Generally Available: Azure Arc-enabled servers support for private endpoints
The Azure Arc team is excited to announce that Azure Arc-enabled servers’ support for private endpoints is now generally available! With private endpoints, you can send traffic from the Azure Connected Machine Agent to Azure over a site-to-site VPN or Express Route circuit instead of the public internet or proxy server. This can help you reduce network exposure and improve security while still allowing you to use Azure Arc to secure, monitor and govern your servers running outside of Azure.
How does it work?
Private endpoints allow you to connect an Azure service to an Azure virtual network using private IP addresses. Servers and other resources in that virtual network can then communicate with the Azure service using the private IP address and instead of sending data over the internet.
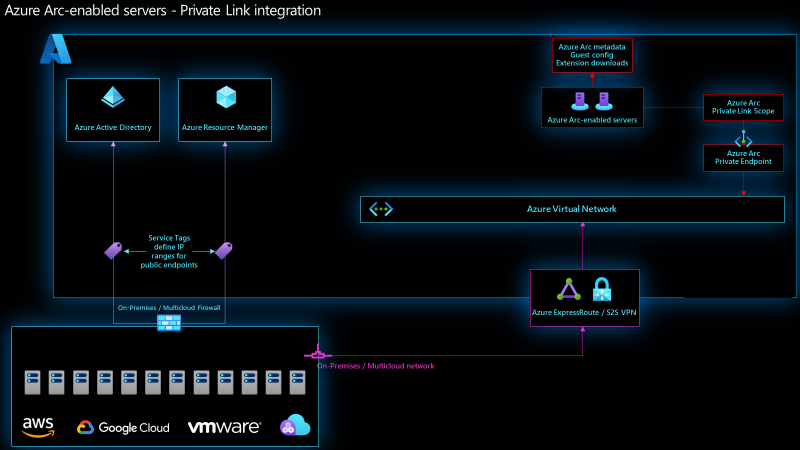
Azure Arc uses a Private Link Scope resource to associate a private endpoint with the non-Azure servers that will use the private endpoint. You’ll also need to set up a site-to-site VPN or Express Route circuit to connect your Azure virtual network with the network where your non-Azure servers are connected.
Once configured, the Connected Machine agent on your Arc-enabled servers will send all metadata updates, extension operations, and guest configuration package downloads over the private endpoint. Network traffic between extensions you’ve installed and the Azure services that support them will also route through the internet unless you’ve configured private endpoints for each of those services. Additionally, the Connected Machine agent will still require access to Azure Active Directory and Azure Resource Manager over the internet.
 Network architecture diagram of Azure Arc-enabled servers private endpoints
Network architecture diagram of Azure Arc-enabled servers private endpoints
Learn more and get started
You can learn more about private endpoints for Azure Arc-enabled servers in our documentation, which covers the concepts, prerequisites, and setup instructions for new and existing servers. There is also an Azure Arc Jumpstart scenario for private endpoints where you can set up a sandbox environment in Azure to learn more about private endpoints and practice working with them without affecting any of your production infrastructure. And lastly, our Azure Arc landing zone accelerator covers network topology and connectivity best practices, as you scale from testing to production workloads
Published on:
Learn moreRelated posts
Microsoft Purview: Data Lifecycle Management- Azure PST Import
Azure PST Import is a migration method that enables PST files stored in Azure Blob Storage to be imported directly into Exchange Online mailbo...
How Snowflake scales with Azure IaaS
Microsoft Rewards: Retirement of Azure AD Account Linking
Microsoft is retiring the Azure AD Account Linking feature for Microsoft Rewards by March 19, 2026. Users can no longer link work accounts to ...
Azure Function to scrape Yahoo data and store it in SharePoint
A couple of weeks ago, I learned about an AI Agent from this Microsoft DevBlogs, which mainly talks about building an AI Agent on top of Copil...
Maximize Azure Cosmos DB Performance with Azure Advisor Recommendations
In the first post of this series, we introduced how Azure Advisor helps Azure Cosmos DB users uncover opportunities to optimize efficiency and...
February Patches for Azure DevOps Server
We are releasing patches for our self‑hosted product, Azure DevOps Server. We strongly recommend that all customers stay on the latest, most s...
Building AI-Powered Apps with Azure Cosmos DB and the Vercel AI SDK
The Vercel AI SDK is an open-source TypeScript toolkit that provides the core building blocks for integrating AI into any JavaScript applicati...
Time Travel in Azure SQL with Temporal Tables
Applications often need to know what data looked like before. Who changed it, when it changed, and what the previous values were. Rebuilding t...