Taking Azure Firewall Premium IDPS Functionality

Written by Gopikrishna Kannan (Head of Products: Azure Firewall and Firewall Manager)
Intrusion detection and prevention (IDPS) is an advanced threat prevention mechanism supported by the Azure Firewall Premium SKU. Unlike simple network filtering, IDPS matches traffic patterns to a set of known malicious signatures. Azure Firewall supports more than 60,000 malicious signatures which are updated in real time. These signatures apply when malicious patterns are detected under the right conditions. The conditions include traffic direction (inbound or outbound) and network scope (private network or public network). Below are examples to validate IDPS configuration in your environment.
Test Setup
Client VM is running in AppSubnet and will connect to the Internet via Azure Firewall. TLS inspection is enabled to deeply inspect HTTPS traffic. IDPS is configured to Alert and Deny suspicious traffic.
For the demonstration, I have configured two rules to allow encrypted traffic to example.com and another rule to TLS inspect traffic to showmyip.com.
Validating HTTP Traffic
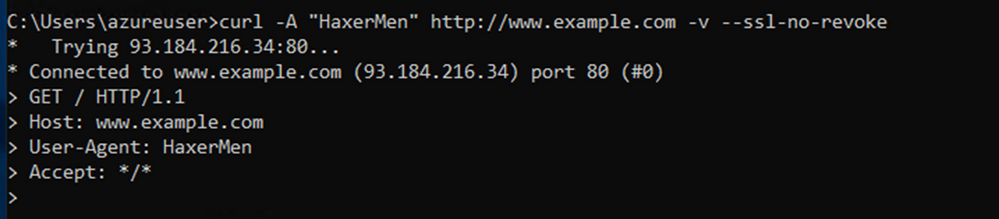
We will validate IDPS by injecting malicious User-Agent HaxerMen in the outbound curl request. Below is the output showing the connection is blocked.
Running the below command in AppSubnet shows no result.
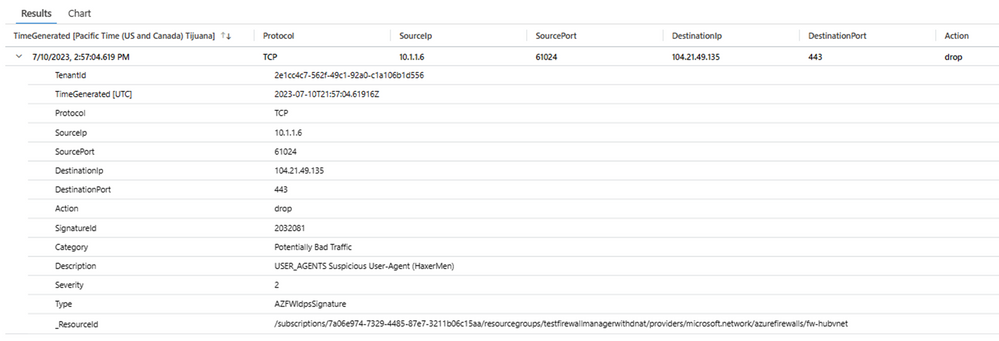
Reviewing the IDPS logs shows traffic is blocked by Signature ID 2032081.
Notice that the source IP is Firewall IP and not the actual client IP. This is a known gap with IDPS logging HTTP traffic.
Signature ID 2032081
A closer look at signature ID 2032081shows this signature applies to http traffic in ANY (both inbound & outbound) direction. It’s also configured as “Alert and Deny” by policy.
Validating HTTPs traffic
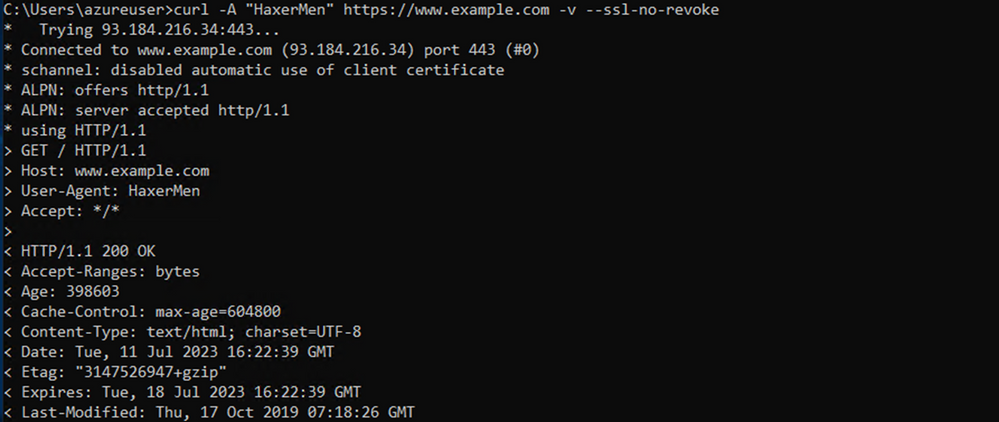
Next, we will test HTTPS connectivity to example.com while injecting user agent HaxerMen. Interestingly, the traffic was allowed and not blocked by IDPS. This is because the agent was undetected as the traffic was encrypted traffic.
So, let’s now run the https connection to showmyip.com which has been configured to be TLS inspected.
Now, let’s browse to www.showmyip.com website by injecting a new agent “HaxerMen”. Notice the traffic is blocked as expected thanks to TLS inspection and IDPS in action.
Inspecting the logs shows the matching malicious signature is 2032081. Note the SourceIp logged is the original client. Unlike the HTTP traffic scenario, IDPS logs the correct source IP.
Conclusion
That’s it! You just finished validating IDPS in a lab. To recap, it’s best practice to enable IDS/IPS with TLS inspection. Depending on your corporate security needs, you can configure IDS/IPS in either Alert mode or Alert & Deny mode. The IDS/IPS signatures are based on emerging threats and automatically pushed to the Firewall at regular intervals (multiple times/hour). It’s the best approach to keep your Azure environments secure. Happy validation!!
If you want to learn more about adopting Zero Trust with Azure Network Security ensuring that organizations’ digital assets are secured from attacks and there is visibility into the network traffic, check out this blog post.
Published on:
Learn moreRelated posts
Improved Python (PyPi/uvx) support in Azure MCP Server
Azure MCP Server now offers first-class Python support via PyPI and uvx, making it easier than ever for Python developers to integrate Azure i...
Microsoft Purview: Data Lifecycle Management- Azure PST Import
Azure PST Import is a migration method that enables PST files stored in Azure Blob Storage to be imported directly into Exchange Online mailbo...
How Snowflake scales with Azure IaaS
Microsoft Rewards: Retirement of Azure AD Account Linking
Microsoft is retiring the Azure AD Account Linking feature for Microsoft Rewards by March 19, 2026. Users can no longer link work accounts to ...
Azure Function to scrape Yahoo data and store it in SharePoint
A couple of weeks ago, I learned about an AI Agent from this Microsoft DevBlogs, which mainly talks about building an AI Agent on top of Copil...
Maximize Azure Cosmos DB Performance with Azure Advisor Recommendations
In the first post of this series, we introduced how Azure Advisor helps Azure Cosmos DB users uncover opportunities to optimize efficiency and...