Authenticating to an Azure CycleCloud Slurm cluster with Azure Active Directory
Overview:
Azure CycleCloud is an enterprise-friendly tool for orchestrating and managing High Performance Computing (HPC) environments on Azure. With CycleCloud, users can provision infrastructure for HPC systems, deploy familiar HPC schedulers, and automatically scale the infrastructure to run jobs efficiently at any scale.
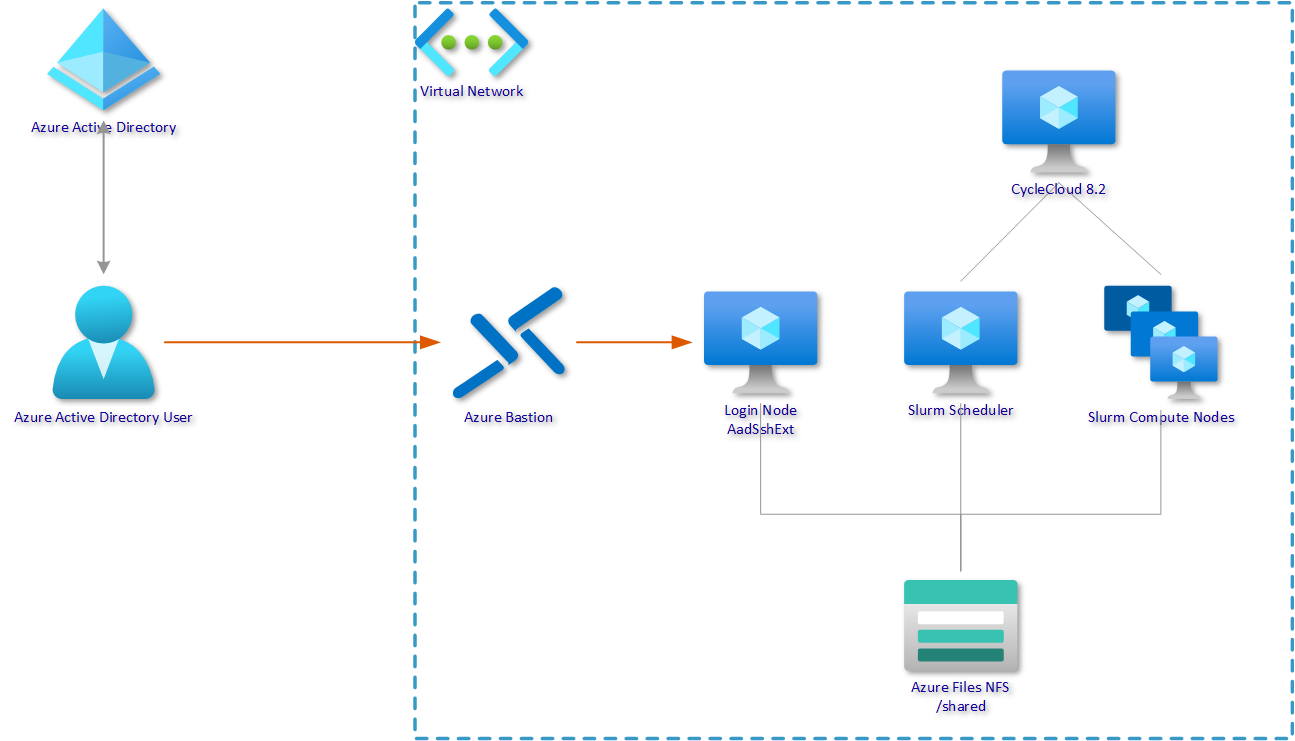
As enterprises increasingly move to using Azure Active Directory for their authentication needs this blog explores how Azure AD and OpenSSH certificate-based authentication may be used to provide authentication to a Slurm cluster. We also utilise the recent Azure Bastion native client support feature to provide remote access to the Login Node over the public internet.
Summarising, we will use the native Azure AD Linux authentication to access the Login Node through the Azure Bastion host, using a temporal, provisioned ssh key. Once logged into the Login Node, the CycleCloud provisioned user account and ssh keys will guarantee authentications to the scheduler and compute nodes. AAD authentication can improve the security to access our environment by enabling the possibility to use conditional access enabling for example multi-factor authentication before being able to use SSH.
Components:
This solution uses an existing Azure AD Tenant and very standard deployments of CycleCloud 8.2, Azure Files NFS (to provide a persistent /shared folder), a Login Node (more details later) and Azure Bastion (Standard SKU). I prefer to deploy these using Bicep. The OS used for all VMs is the AlmaLinux 8.5 HPC image.
Solution:
1) Azure Bastion, this is a typical deployment of Azure Bastion with the only additional considerations being to ensure it is the Standard SKU and that enableTunneling is set to true.
2) Login Node, again a standard virtual machine deployment. To interact with the Slurm cluster it should have Slurm and Munge installed with configurations matching your Slurm cluster. The /shared folder is also mounted to provide access to the shared home folders. Typically to enable AAD auth for Linux we would ensure the VM has a System Assigned Managed Identity and add the AADSSHLoginForLinux extension. As the extension does not currently support AlmaLinux it has been installed using Cloud Init referencing the RHEL 8 RPMs. Additionally note how the default home directory for new users has been changed to /shared/home and use of NFS for home directories enabled.
To be able to access the VM, the last thing to do is to assign an RBAC role to allow the user to login. This could be the Vitual Machine User Login role, for normal users, or the Virtual Machine Administrator Login, for system administrators. Here an example to assign the role to a standard user:
More details about the necessary steps to enable the SSH login on the VM can be found here.
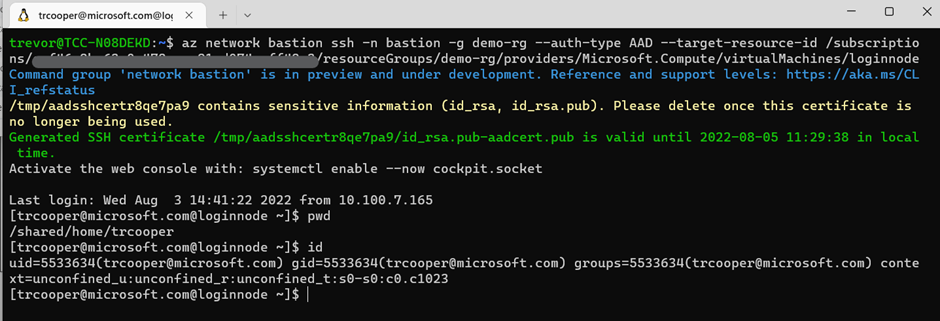
With this in place we now configure Azure role assignments authorizing our user to log in to the VM and use the Azure CLI to connect to the Login Node via Azure Bastion.
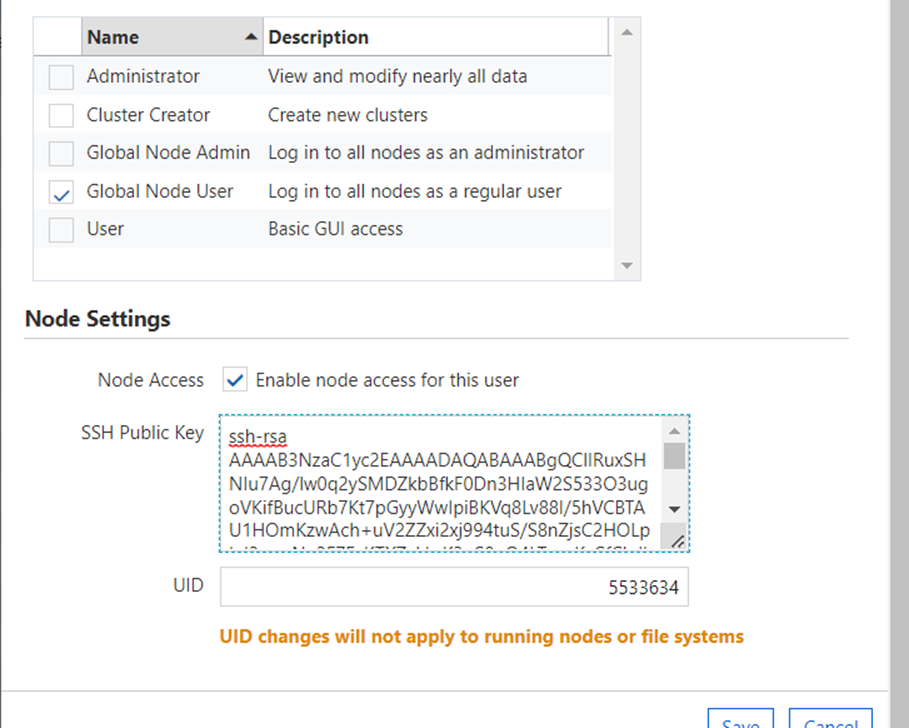
Note the user’s home directory name, uid/gid and create an ssh pubkey pair for use with the cluster. This will be used to create a matching ‘local’ user in the CycleCloud user management system.
3) CycleCloud, with the user access to the Login Node now established we must grant the user access to the Compute Nodes. For this the built-in CycleCloud user management system is used and we will create a matching ‘local’ user to our AAD principal.
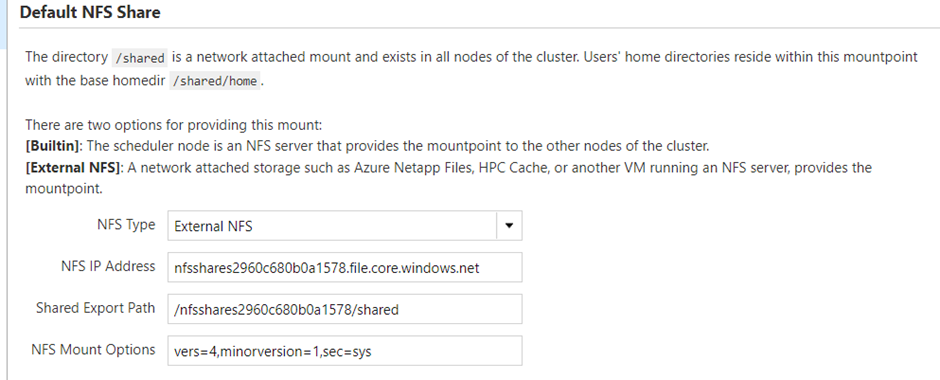
The default CycleCloud Slurm template is used to create the cluster with the default NFS share mounted from the Azure Files NFS share.
Conclusion:
With the cluster started and ‘local’ user assigned we can update the Login Node to ensure it has the correct munge key and the slum.conf is pointing to the scheduler. From the Login Node our AAD Authenticated user can now submit and run jobs on the cluster.
Reference:
Published on:
Learn moreRelated posts
Microsoft Power BI: Tenant setting changes for Microsoft Azure Maps in Power BI
Admins will have updated tenant settings for Azure Maps in Power BI, split into three controls. The update requires Power BI Desktop April 202...
Build 2025 Preview: Transform Your AI Apps and Agents with Azure Cosmos DB
Microsoft Build is less than a week away, and the Azure Cosmos DB team will be out in force to showcase the newest features and capabilities f...
Fabric Mirroring for Azure Cosmos DB: Public Preview Refresh Now Live with New Features
We’re thrilled to announce the latest refresh of Fabric Mirroring for Azure Cosmos DB, now available with several powerful new features that e...
Power Platform – Use Azure Key Vault secrets with environment variables
We are announcing the ability to use Azure Key Vault secrets with environment variables in Power Platform. This feature will reach general ava...
Validating Azure Key Vault Access Securely in Fabric Notebooks
Working with sensitive data in Microsoft Fabric requires careful handling of secrets, especially when collaborating externally. In a recent cu...