Simplified management of Listeners TLS certificates
To address these operational pain points for our customers, Azure Application Gateway now has an essential Listeners TLS certificate management GUI capability. It enables our Application Gateway V2 users to list and manage the listener TLS certificates through the portal experience.
The key features of this portal capability are
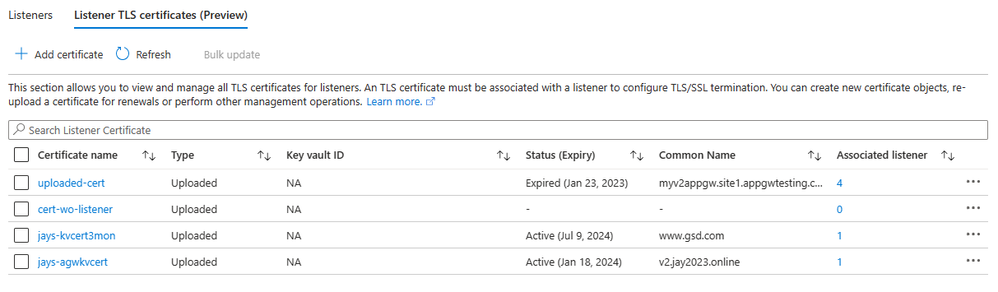
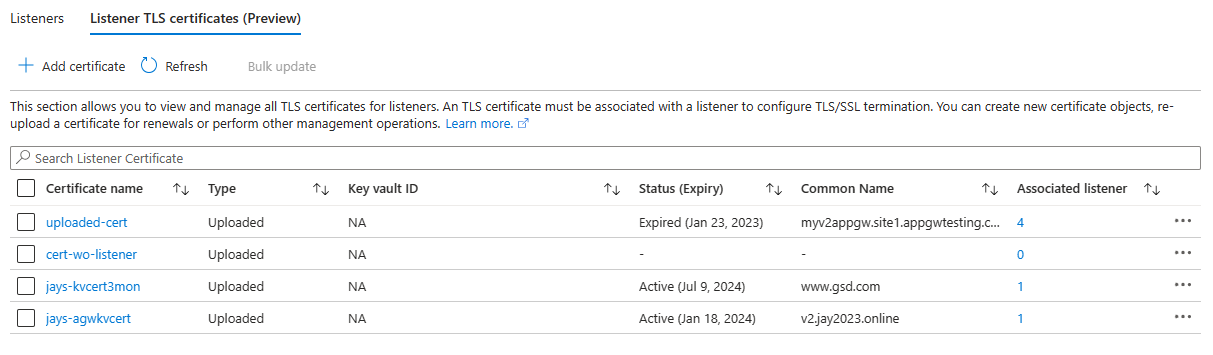
- Quick listing: This dedicated certificate section lists all the listener TLS listener certificates, their types, and their association with the listeners.
- Certificate information: The list shows required certificate details such as Expiry, Common Name, Thumbprint, and Issuer Name that help with easy identification during the various operational activities. Such information can also be helpful when troubleshooting data path issues.
- Bulk operations: The "Bulk update" menu option lets you edit the certificates in one go or recover a gateway from a failed provisioning state when facing simultaneous misconfigurations for multiple certificate objects.
(Learn more). - Hassle-free operations: You can manage the certificates without worrying about the sub-resource dependencies or missing a command before saving the gateway. The guided experience in the portal takes care of these on your behalf.
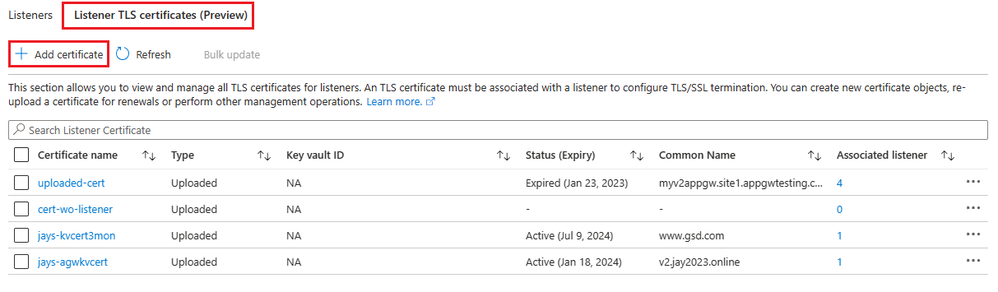
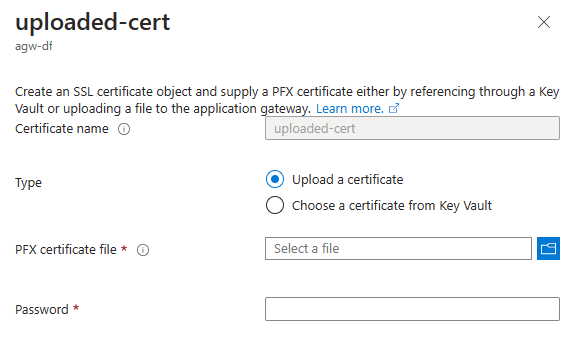
Case 1: Uploading a new certificate – The Application Gateway portal traditionally allowed you to create a new certificate (uploaded or referenced through Key Vault) during a listener add operation. To provide flexibility for our users, we now allow you to create a certificate separately.
-
Go to your Application Gateway resource in the Azure portal.
-
Go to the Listeners blade.
-
Open the "Listener TLS certificates (preview)" tab.
-
Select "Add a certificate".
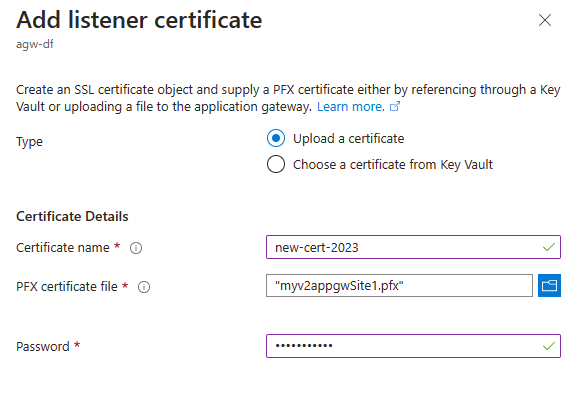
Case 2: Renewing a certificate – For the certificates that are directly uploaded (Type: Uploaded) to your application gateway, the renewal process is as simple as re-uploading a PFX file. The certificate names you see on your application gateway resource are the objects or containers for the certificate data. By uploading an updated PFX file to an existing certificate, you are updating that certificate's contents.
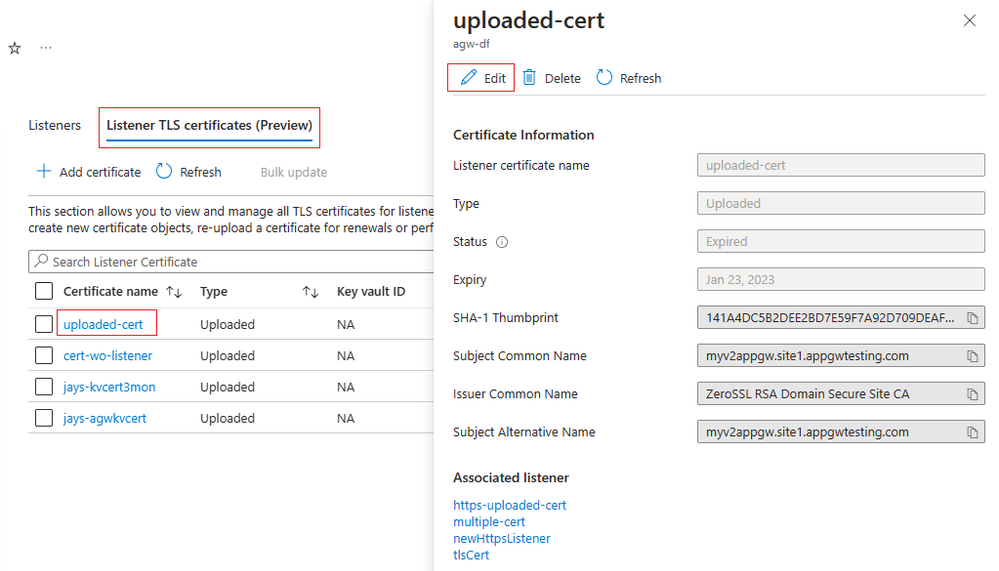
Tip: Before you renew/update a certificate, verify if you have chosen the proper certificate by checking its expiration date, common name, or thumbprint. Note that a certificate not associated with a listener will not show these certificate details.
To renew an uploaded type certificate,
- Go to your Application Gateway resource in the Azure portal.
- Go to the Listeners blade.
- Open the "Listener TLS certificates (preview)" tab.
- Select the certificate name that you want to renew.
- Select Edit.
- Keep the Type as "Upload a certificate," choose the new PFX file from your local system and specify the PFX file password.
- Select Save.
(Note the certificate name is greyed out since this is an existing certificate object in which you can upload a new certificate file.)
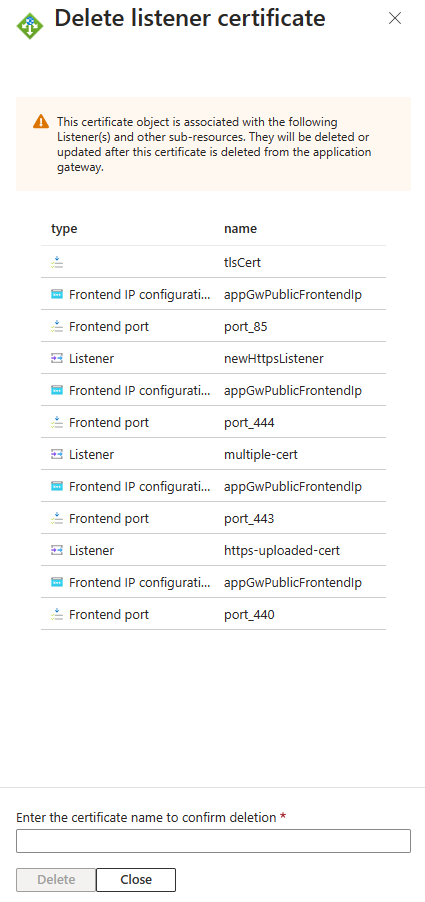
Case 3: Deleting a certificate that is associated with multiple listeners - Consider a scenario where you want to remove a certificate used by numerous HTTPS listeners, which in turn are associated with their respective rules. Earlier, in such cases, your PowerShell operation would look something like this to delete each rule, its listener, and the certificate.
With this new portal functionality, you can delete such certificates with just a few clicks and clean up your application gateway resource.
- Go to your Application Gateway resource in the Azure portal.
- Go to the Listeners blade.
- Open the "Listener TLS certificates (preview)" tab.
- Select the certificate name that you want to delete.
- Select the Delete option (or you can use the three-dot menu option on the right of the certificate listing).
A confirmation message will show the list of affected sub-resources as shown below.
Visit our documentation to understand the available controls. The listener certificate management in the portal is still in the preview. We would love to hear your feedback and experiences.
Published on:
Learn more