Extending Operational Technology to Azure
Within the mining, oil and gas, utilities, and manufacturing industries you will find two distinct environments:
- Information Technology (IT) - this environment is the backbone of an organisation and is what we are most familiar with. This is the environment where an organisation’s collaboration, finance, human resources, and other business applications exist.
- Operational Technology (OT) – this is where an organisation’s industrial operations exist. In here you will find robots, Industrial Control Systems (ICS), Supervisory Control and Data Acquisition (SCADA) systems and Programmable Logic Controllers (PLCs)
When we talk about cloud enabling an organisation, most of the content has been focused on the IT environment, which we know and understand quite well. When we talk about cloud enabling OT or about delivering cloud services into the OT, the room tends to go very quiet and with good reason. The OT is the crown jewels of an organisation, and its operational performance is key to an organisation’s revenue. Anything that could impact the OT will have an increased level of scrutiny and unless all the check boxes have been ticked won’t happen.
In this post we are going to explore how does one cloud enable the OT environment and at the same time be true to the standards and controls that are in place to protect it. Throughout our journey we will be covering:
- An introduction to the Purdue enterprise reference architecture
- What problems are we looking to solve?
- Cloud enabling the Operational Technology environment
An Introduction to the Purdue Enterprise Reference Architecture
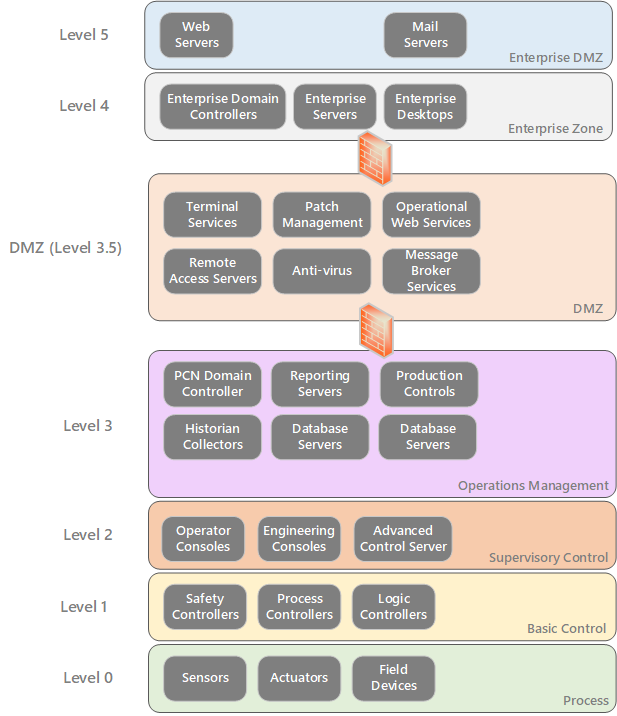
The Purdue Enterprise Reference Architecture (PERA) is a model that was established in the 1990s to protect identities, information, and assets within the OT environment. This model has come along way and has served the industry in many ways. The following diagram provides a high-level view of the Purdue Model.
The Purdue Model has six functional levels from 0 to 5. Each functional level is only allowed to communicate with the adjacent north and south layers:
- Level 5 (Enterprise DMZ Network) consists of a broad set of external-facing enterprise IT systems.
- Level 4 (Enterprise Zone) comprises enterprise IT systems such as enterprise AD servers, database servers, application servers, and file servers.
- Level 3 (Operations Management) consists of systems that support plant-wide control, OT Applications and OT monitoring functions. Example systems include Historians, Analytic systems, OT Management Servers.
- Level 2 (Supervisory Control) includes monitoring and supervisory control logic for analysing and acting on Level 1 data. Systems include Human-Machine Interface (HMI), Engineering Consoles and Advanced control (SCADA) systems.
- Level 1 (Basic Control) includes control devices such as Programmable Logic Controllers (PLCs), control processors, and safety controllers that monitor and provide automatic control for Level 0 equipment.
- Level 0 (Process) includes physical equipment such as sensors, actuators, valves, pumps, compressors, etc.
With the advent of Industry 4.0 and the Internet of Things (IoT), there have been a lot of challenges to the continuation of the Purdue Model in the industry. One of the main gaps in the model is the lack of cloud integration. In fairness, the cloud didn’t exist when the model was founded as the technology was a lot different those days. Industry 4.0 has resulted in an exponential transformation of the process control network.
What problems are we looking to solve?
We recently worked with an organisation that was looking to gain a competitive edge within its industry by enabling its OT environment to leverage the benefits that could be realised by extending it into Azure. Some of the potential benefits included:
- Being able to make data-driven decisions;
- Predictive maintenance for the physical machinery;
- Advanced analytics for AI and Machine Learning to optimise business throughput.
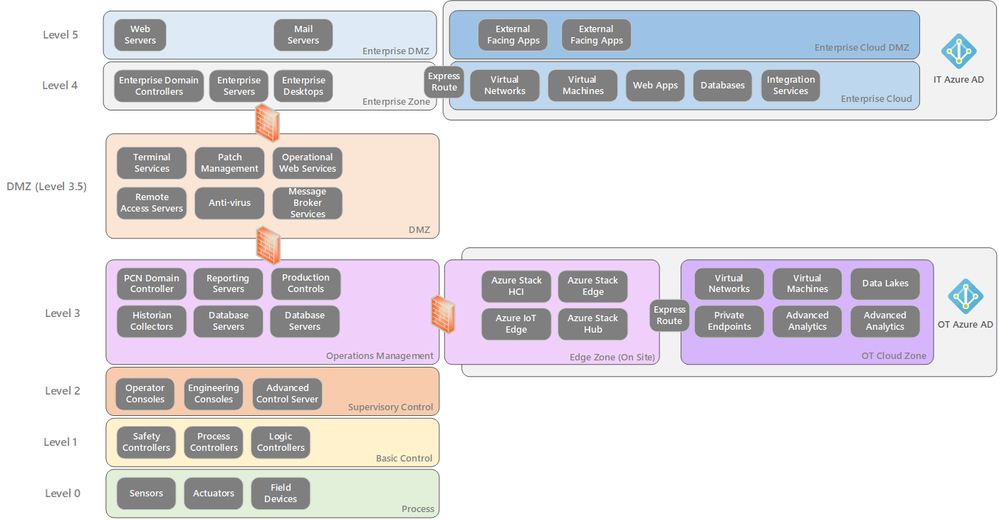
The organisation was particularly interested in being able leverage Azure IoT, Azure IoT Edge, Azure Machine Learning, Azure Stack Edge and Azure Stack Hub within the OT environment. However, it was unsure of how this would be achieved under the Purdue Model, which it wanted to continue to utilise for the security aspects offered. In order to reduce risk, the organisation was willing to accept the additional complexities and costs incurred by this model. In the following segment we will cover the elements that were introduced to the Purdue Model to extend the OT environment into Azure.
Cloud Enabling the Operational Technology Environment
Through a series of workshops with the organisation, the following high-level changes were implemented to extend the Purdue Model to the Azure:
- A new Azure AD tenant was established for the OT environment to enable hybrid identity management. This was a requirement from the OT organisations security standards, which is based on the ISA99 /IEC 62443 Standards.
- Separate Azure subscriptions and Azure landing zones were provisioned for the OT environment to extend the Operational Management to Azure.
- External access into the Azure landing zones was prohibited.
- A separate OT network to host the edge devices and solutions was created to provide low latency compute that would be necessary for quick decision making.
- An ExpressRoute circuit was deployed to provide hybrid networking connectivity to Azure with access to Azure PaaS Services via Private Endpoints.
To accelerate the enablement of the OT environment for Azure, the Microsoft Cloud Adoption Framework for Azure and Azure Well Architected Framework were utilised. These were the same frameworks that were utilised to enable Azure in the organisation’s IT environment. This resulted in the revised Purdue Model.
Some of the key benefits the revised model provided included:
- Leveraging cloud capabilities. By extending OT to the cloud, the organisation was now able to leverage powerful Compute, Analytics, Machine Learning and AI in the cloud.
- Organisational alignment. The revised model aligns with how organisations within this industry operate today.
- Identity separation between IT and OT: As IT and OT would have their own Azure AD Tenants, the management of OT resources could be limited to OT identities.
- Resource separation between IT and OT. OT cloud resources would fall under their own Azure subscription and Azure AD Tenant making it easier to identify OT resources from IT.
- Simplifying the demerging of assets. The demerging of assets from organisations within this industry occurs frequently. As the identities and cloud resources are independent of IT, OT resources can now be decoupled easily.
- Improved network security. By utilising private network extensions, via Private Endpoint and VNET integrations, PaaS Services could be accessed securely via the organisation’s network. There would be no public exposure of OT cloud resources.
- Hybrid edge services. The ability to extend cloud services to the edge for latency sensitive applications.
Summary
Since the initial introduction of the Purdue Model in the early 1990s, Information Technology and Operational Technology environments have changed significantly. A common industry trend is to now see IT and OT environments converge, however, not all organisations are embracing this. Security, safety, and uptime are important factors in the OT world, therefore, some organisations prefer to continue with the traditional segregation between IT and OT as part of their risk-mitigation approach. For these organisations we can cloud enable their OT environment so that they can leverage the benefits that Azure has to offer. The high-level approach that was discussed is applicable to most organisations, however, each organisations journey to the cloud will be unique due to their varied requirements.
Published on:
Learn moreRelated posts
Power Pages + Azure AD B2C: “The Provided Application Is Not Valid” Error
If you are new to configuring Azure AD B2C as Identity Provider in Power Pages, refer Power Pages : Set up Azure AD B2C After completing the s...
Semantic Reranking with Azure SQL, SQL Server 2025 and Cohere Rerank models
Supporting re‑ranking has been one of the most common requests lately. While not always essential, it can be a valuable addition to a solution...
How Azure Cosmos DB Powers ARM’s Federated Future: Scaling for the Next Billion Requests
The Cloud at Hyperscale: ARM’s Mission and Growth Azure Resource Manager (ARM) is the backbone of Azure’s resource provisioning and management...
Automating Business PDFs Using Azure Document Intelligence and Power Automate
In today’s data-driven enterprises, critical business information often arrives in the form of PDFs—bank statements, invoices, policy document...
Azure Developer CLI (azd) Dec 2025 – Extensions Enhancements, Foundry Rebranding, and Azure Pipelines Improvements
This post announces the December release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) Dec 2025 – Extensions En...
Unlock the power of distributed graph databases with JanusGraph and Azure Apache Cassandra
Connecting the Dots: How Graph Databases Drive Innovation In today’s data-rich world, organizations face challenges that go beyond simple tabl...
Azure Boards integration with GitHub Copilot
A few months ago we introduced the Azure Boards integration with GitHub Copilot in private preview. The goal was simple: allow teams to take a...