Receive Email Notification when new IDPS rules get Created via Logic Apps
Written in collaboration with
Introduction:
Azure Firewall Premium provides advanced threat protection capabilities to meet the needs of highly sensitive and regulated environments. One of these capabilities is IDPS, a network intrusion detection and prevention system that allows you to monitor network activities for malicious activity, and optionally block the activity from occurring. This capability is signature-based and detects attacks by looking for specific patterns, such as byte sequences in network traffic, or known malicious intrusion sequences used by malware for both application and network level traffic (Layers 3-7) in inbound, spoke-spoke, and outbound traffic. Currently, there are over 58,000 rules in over 50 categories, including malware command and control, phishing, trojan, botnets, SCADA network protocols, and more. The signatures are fully managed and continuously updated by Microsoft, with around 20-40+ new rules being released each day. A common request from customers is to receive notifications when there are new updates or additions to the signatures, which can now be automated through a Logic App using the Firewall Policy IDPS signatures REST API. The remainder of this blog will guide you on how to deploy the Logic App to receive notifications about any signature updates daily.
Deployment:
The automation has been published to the Azure Network Security GitHub repository, from where it can be deployed directly to your environment through the provided ARM template, found below. To deploy the automation, your account needs to have Contributor rights on the target resource group that will contain the Logic App resource (see here for more information). When you are ready, you can click the Deploy to Azure button from our GitHub Azure Firewall IDPS page.
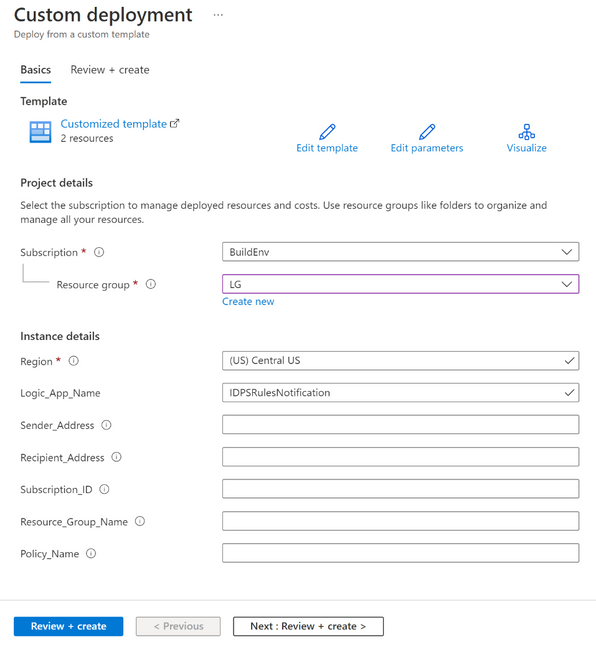
During the deployment, you must specify some details, including the subscription, resource group, name, and region of this automation. You must also configure the following:
- Sender_Address: email address from which the automation will send the IDPS updates information to (this address is also used to form the connection to Office 365 Outlook, meaning the user deploying the automation must have access to the email account).
- Recipient_Address: email address to which the automation will send the IDPS updates information to (i.e., Security Team distribution list)
- Subscription_ID: name of the subscription that hosts the Firewall Policy with IDPS rules that you would like to receive updates about.
- Resource_Group_Name: name of the resource group that hosts the Firewall Policy with the IDPS rules that you would like to receive updates about.
- Policy_Name: name of the Firewall Policy with the IDPS rules you would like to receive updates about.
As shown in the picture above, the ARM template will create the Logic App Playbook. Additionally, the template will create the API connection to Office 365. You must authorize this Office 365 API connection for the sender’s mailbox, from which the IDPS updates email will be sent.
To authorize the API connection:
- Go to the Resource Group you used to deploy the template resources.
- Select the Office365 API connection and press Edit API connection.
- Press the Authorize button.
- Make sure to authenticate against Azure AD.
- Press save.
Lastly, the Logic App must have the necessary permissions to query the IDPS rules on the Firewall Policy via the REST API. This can be obtained via assigning the Logic App a system-assigned Managed Identity with Contributor permissions on the Firewall Policy resource or the Resource Group hosting the Firewall Policy resource. Note that you can assign permissions only if your account has been assigned Owner or User Access Administrator roles to the underlying resource.
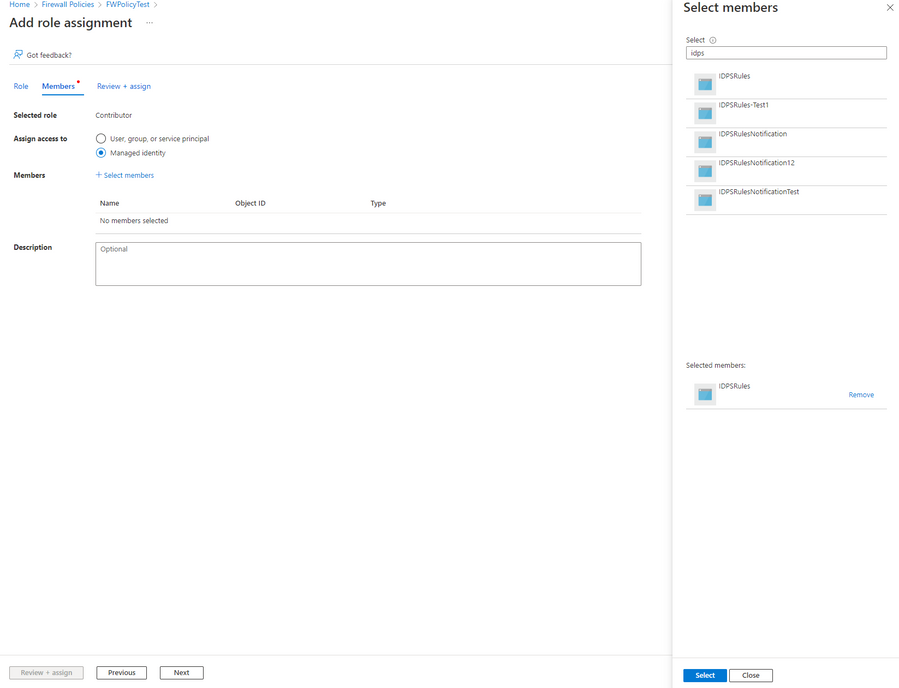
To assign Managed Identity to specific scope:
- Make sure you have User Access Administrator or Owner permissions for this scope (Firewall Policy resource or Resource Group hosting Firewall Policy resource).
- Go to the Firewall Policy resource/Resource Group page.
- Press Access Control (IAM) on the navigation bar.
- Press +Add and Add role assignment.
- Select the Contributor role.
- Assign access to Managed identity.
- Select the subscription where the Logic App was deployed.
- Select IDPSRulesNotification Logic App.
- Press save.
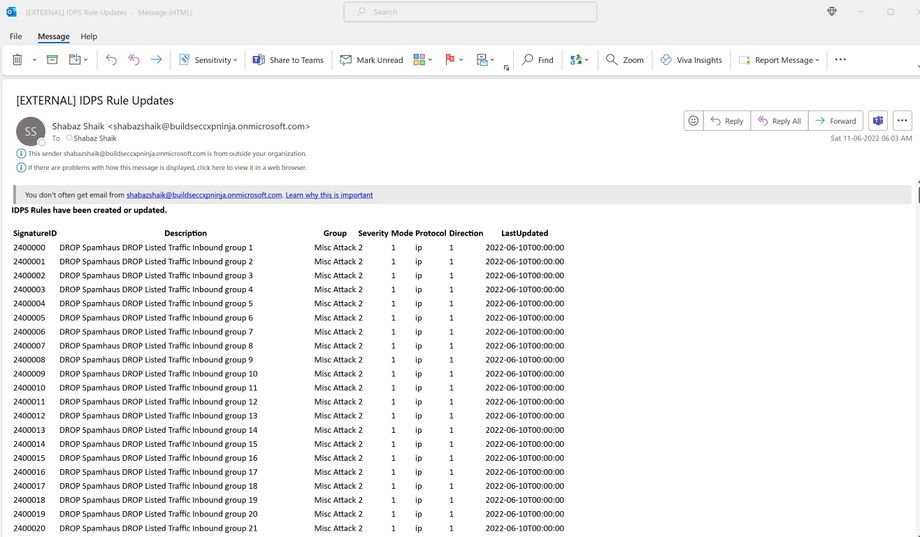
Once you have deployed and authorized the Logic App, you will receive a daily notification all the updated and newly added IDPS signatures.
Logic Implemented:
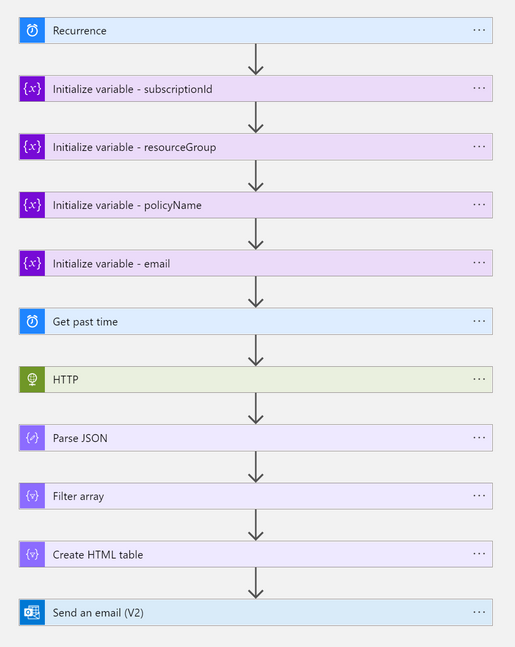
The automation is configured to run daily by using a scheduler (frequency of which can be adjusted to meet your organization’s need). The automation sets the variables provided when the Logic App was deployed (i.e., subscription ID, Resource Group, Firewall policy Name), retrieves the time from which you would look to receive updates from, queries the IDPS signatures REST API for the Firewall Policy you defined earlier, parses the results returned in JSON format, filters based on time updated, creates an HTML table, and then sends an email with that table.
In some cases, you may require certain modifications to the Logic App. Examples of how to make these modifications can be found below:
- In the Logic App designer, you can select the ‘Get past time’ step and enter the number of past days in which these changes have occurred, for example if we want to see what signatures were updated in the last five days, you can enter the interval as five as shown below. The default value should be two as the logic app gets triggered daily at 0 AM (UTC) and it will check for updates from the previous day since the API is updated with the additional results at 0 AM each day.
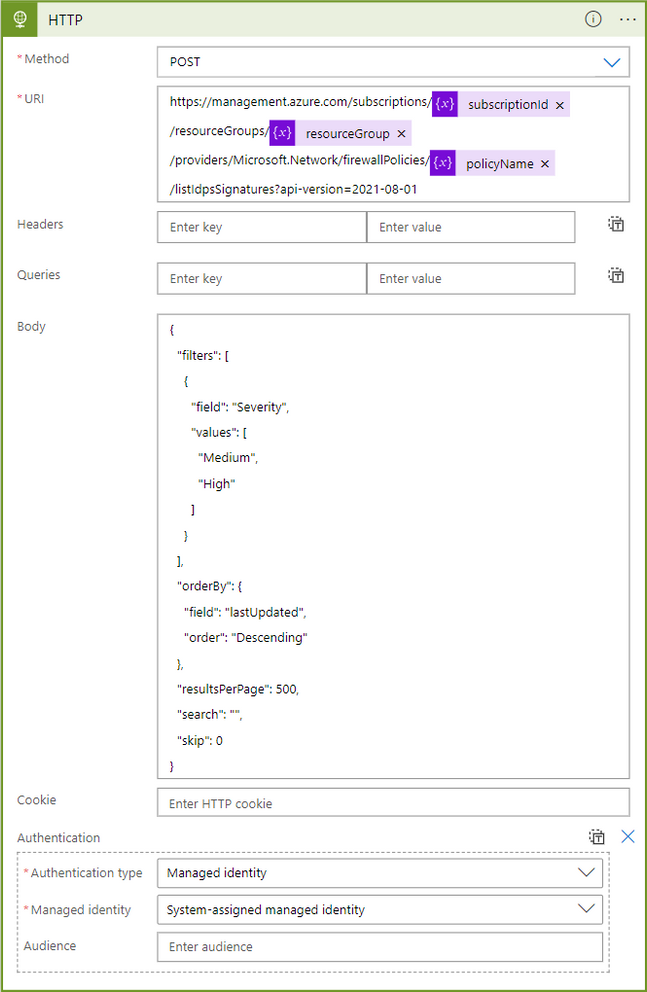
- You can also finetune the signatures you want to receive updates regarding by using the filters defined in this document by adding a filter field to the REST API request in the HTTP step. By default, the Logic App is receiving any signatures with severity of Medium or High, but you may also want to receive Low severity signatures. Alternatively, you may want to filter for signatures that are in Deny mode only. To accomplish this, you would use the following request in the Body field:
{
"filters": [
{
"field": "Mode",
"values": [
"Deny"
]
}
],
"search": "",
"orderBy": {
"field": "lastUpdated",
"order": "Descending"
},
"resultsPerPage": 500,
"skip": 0
}
Note: It is possible that the email sent went to your Spam folder. In this case, we recommend moving it to your Inbox folder so you do not miss any signature updates.
Conclusion:
This automation can be leveraged by organizations to automatically receive notifications for the newly released and updated IDPS signatures. To ensure this automation meets the needs of your organization, you can fine-tune it by modifying how often the Logic App should run, how many days it should collect signatures for, and what severity and/or mode of signatures should be included in the email.
Published on:
Learn more