Maximizing Effectiveness: Best Practices for Azure DDoS Protection and Application Resilience

Azure DDoS Protection is constantly innovating to protect customers from ever-changing DDoS attacks. As attacks become more sophisticated, it is important to keep your applications up to date with industry best practices to ensure maximum effectiveness when using Azure DDoS Protection. Below are architectural and design decisions you can make to ensure your resources are resilient to DDoS attacks.
Minimizing Vulnerabilities and Enabling Relevant Protections
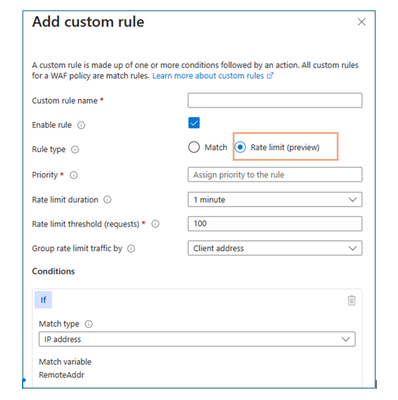
It is important to launch the relevant protection services for your application. If you have any applications deployed to the internet, enabling DDoS Protection is vital. Any application that is open to the internet is vulnerable to Layer 3 and Layer 4 attacks. If your application is deployed to the web, enabling Web Application Firewall will protect you from Layer 7, application attacks. A WAF solution can react to security threats faster by centrally patching vulnerabilities instead of securing each individual web application. WAF can be attached to Azure’s Application Gateway and Azure Front Door. WAF now offers rate-limiting, meaning customers can create rules that restrict source IP addresses to a maximum limit of requests per minute. Both work in tandem to ensure protection on all fronts.
While these services will protect you if deployed during an attack, it is beneficial to deploy them during peace times to get to know what normal traffic looks like. Knowing these normal patterns will allow you to set up relevant metrics and alerts and help us tailor the experience to your application. As part of Azure DDoS Protection each customer has unique auto-tuned DDoS mitigation policies. Customers can view their policies and filter by IP or traffic type in the Azure Portal metrics, see more here.
It is useful to set up metrics and notifications for your applications. You can use the logs in Azure portal to view traffic patterns during an attack. You can see how much traffic is being dropped and why, along with many other useful insights, see more here.
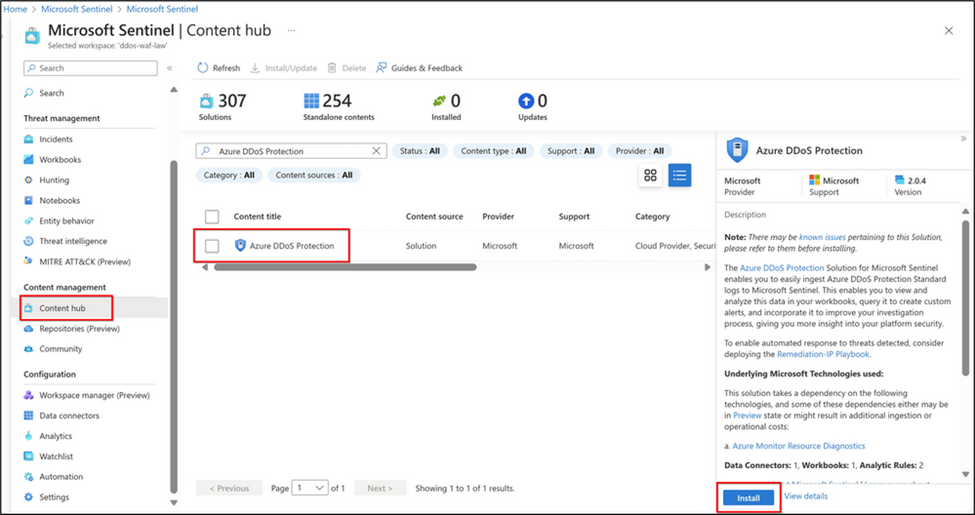
Azure DDoS can be integrated with Microsoft Sentinel to ingest DDoS protection logs for analysis and monitoring. From Sentinel, custom alerts can be created and organized for analysis. Sentinel can also be used with Azure Firewall to automate responses to DDoS attacks. For more information on Microsoft Sentinel integrations, see more here.
While in peacetime, it is a good idea to simulate a DDoS attack to see how your systems react. You can use one of our attack simulation partners, see more info here.
While our protection services handle attacks, there are things you can do to make sure your applications see minimal impact while we are mitigating attacks. These practices also strength your application’s overall security.
Design for Security and Defense In-Depth
It is essential to consider security at every level of development. To make sure your applications are secure it is important to layer defensive strategies.
Minimizing your surface area helps lower the risk of attacks. One way this can be done is by using approval lists to close any unnecessary IPs or listening ports. With fewer entry points, attacks are less likely to be successful and it is easier to monitor what you have. Customers can utilize Azure Firewall and Bastion to access Azure resources. Firewall adds filtering and real time alerts to applications. Customers can filter out new and emerging bad domains and IPs to keep applications safe from the most recent threats. Azure Firewall Premium also has IDPS, which provides information on bad sources based on intel from the Microsoft Threat Intelligence Center. Bastion enables customers to securely connect to virtual machines from Azure Portal or a native client. When you connect via Azure Bastion, your virtual machines don't need a public IP address, agent, or special client software.
Network security groups can also be used to simplify configuring network security and creating security rules.
It is recommended to deploy virtual networks when possible. While Azure Virtual Networks default to using public IPs as their source IPs, using service endpoints switches service traffic to virtual network private address as the source IP address when accessing Azure from a virtual network.
Lastly, many customers maintain on-prem resources for various reasons, however keeping well known public entities in Azure allows the Azure platform and services to provide added protection. Customers can leverage Azure’s global scale DDoS Mitigation. Azure mitigated what is believed to be the largest DDoS network attack at 3.47 Tbps. Azure has a DDoS capacity to mitigate around 50 Tbps of attack traffic, allowing us to handle attacks without customers seeing an impact much better than most on-prem resources can. If you need to have on-prem resources, it is a good idea to keep them private.
Building for Scalability
Scalability is an application's ability to grow or shrink appropriately to usage. If you see an influx of legitimate traffic, you want your application to be able to handle all those users. However, once this influx is over, you do not want to be paying for unnecessary resources.
Many Azure services and products have auto-scaling features which should be enabled to dynamically allocate resources. Azure DDoS Network Protection also offers cost protection for resources added during an attack.
Instance stickiness, or session affinity is when a client’s requests are always routed to the same servers. This can overwhelm the servers. It is important to make sure any instance can handle any request. Avoid storing session states in memory or using machine specific keys for encryption. To learn more about stickiness see here.
To ensure effective scalability, it is vital to identify and avoid bottlenecks. No amount of scaling out will be able to compensate for a bottlenecked backend.
Scaling in is an equally important part of scalability. Build your applications with resilient retry logic against transient network failures or connection resets. While Azure DDoS Protection and Azure WAF can provide mitigation from attack traffic, your application needs retry logic that can withstand. One way to test if your application has sufficient retry logic, is by launching a simulated DDoS attack. This will let you see how your application acts under the stresses of a DDoS attack. Doing various simulated attacks helps ensure your design is working with Azure Security services to mitigate impact. See this blog post for more on resilient retry logic.
As DDoS attacks become more frequent and easier for malicious actors to utilize, it is prudent to keep up to date with comprehensive protections for your applications. By following the tips above, you can have confidence that your applications are protected on all levels.
Resources:
2022 in Review: DDoS Attack Trends and Insights
Azure DDoS Protection Documentation
Microsoft Digital Defense Report 2022
Azure Web Application Firewall Documentation
New Azure DDoS Solution for Microsoft Sentinel Blog
Using the Retry Pattern to Make Your Cloud Applications More Resilient
Published on:
Learn moreRelated posts
Azure Boards integration with GitHub Copilot
A few months ago we introduced the Azure Boards integration with GitHub Copilot in private preview. The goal was simple: allow teams to take a...
Microsoft Dataverse – Monitor batch workloads with Azure Monitor Application Insights
We are announcing the ability to monitor batch workload telemetry in Azure Monitor Application Insights for finance and operations apps in Mic...
Copilot Studio: Connect An Azure SQL Database As Knowledge
Copilot Studio can connect to an Azure SQL database and use its structured data as ... The post Copilot Studio: Connect An Azure SQL Database ...
Retirement of Global Personal Access Tokens in Azure DevOps
In the new year, we’ll be retiring the Global Personal Access Token (PAT) type in Azure DevOps. Global PATs allow users to authenticate across...
Azure Cosmos DB vNext Emulator: Query and Observability Enhancements
The Azure Cosmos DB Linux-based vNext emulator (preview) is a local version of the Azure Cosmos DB service that runs as a Docker container on ...
Azure Cosmos DB : Becoming a Search-Native Database
For years, “Database” and “Search systems” (think Elastic Search) lived in separate worlds. While both Databases and Search Systems oper...