New Azure DDoS Solution for Microsoft Sentinel
Written in collaboration with Amir Dahan
Introduction
Cybercriminals demonstrate increasingly sophisticated tactics using DDoS attacks as multi-purpose tool. While DDoS attacks are commonly used to take down critical systems, applications, and infrastructure, they also serve adversaries for extortion and political or ideological motives. The crown jewel is using DDoS attacks as a smokescreen to conceal data breaches while the attention is directed to the attack. By overwhelming the targeted website or application with a large amount of traffic, the attackers can exploit vulnerabilities and steal sensitive information.
Customers use Azure DDoS Protection services to safeguard their applications hosted in Azure against DDoS attacks. Microsoft Sentinel and Azure DDoS Protection services offer rich integration to easily ingest DDoS Protection logs and view and analyze this data in Sentinel to create custom alerts and improve their security posture, investigation, and response processes. Specifically, customers can correlate DDoS smokescreen attacks with events from different sources to detect advanced attacks, such as data theft, and to automatically block them.
We always look for better ways for our customers to achieve more from Azure DDoS Protection and Microsoft Sentinel. In this announcement, we introduce the new Azure DDoS solution for Microsoft Sentinel. The new solution uses Azure DDoS Protection logs to pinpoint offending DDoS sources and to block them from launching other, sophisticated attacks, such as data theft.
We will provide an example use case covered by this solution. Then, we’ll describe the solution components, the new alert rules we’ve created to pinpoint adversaries, and how to leverage Azure Firewall as an example of remediation. Azure Firewall offers remediation by preventing bad actors from accessing and stealing sensitive data in the protected application. The solution also supports third party firewalls that offer a Sentinel Playbook for IP remediation. In future, we plan to extend the solution to remediate attackers in Azure WAF for organizations that wish to protect their web applications.
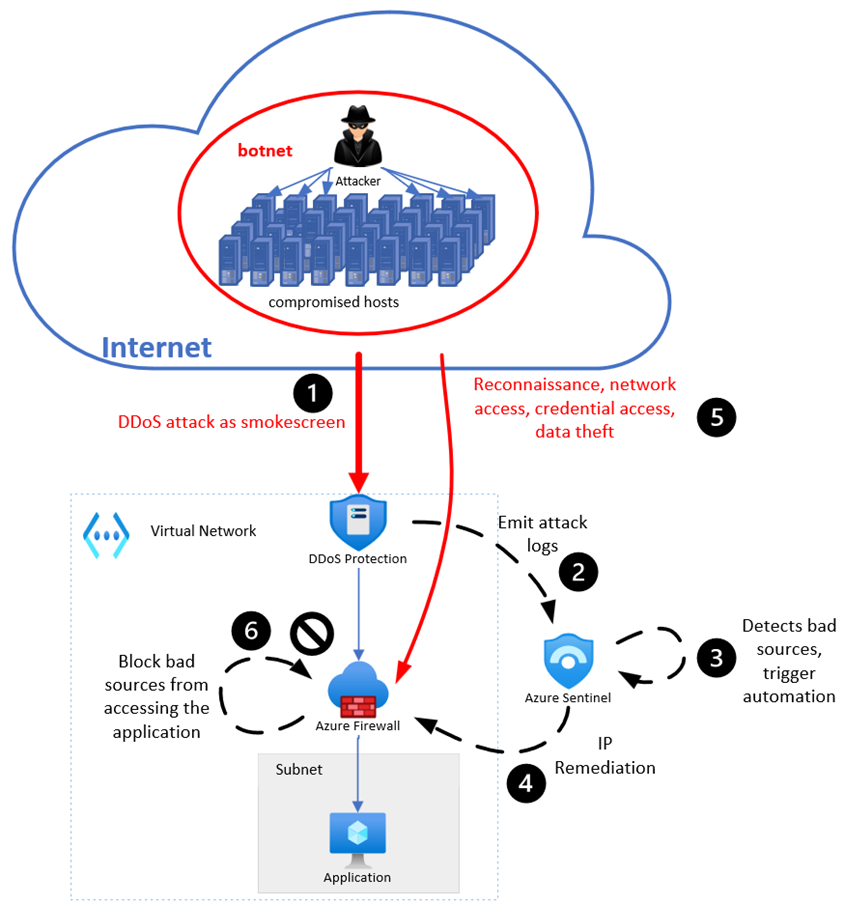
Remediation of adversaries in Azure Firewall
Below figure describes how the solution works and what steps are taken from attack detection to remediation.
- An adversary uses a bad bot to launch a multi-vector attack campaign. He starts by flooding the customer application with a DDoS attack to create havoc, using DDoS as a smokescreen for the next attack vector.
- Azure DDoS Protection always monitors attacks on the protected resources. When it detects the attack, it emits log signals to Microsoft Sentinel.
- Microsoft Sentinel derives the attacking source IP addresses from the logs, and triggers Azure Firewall Remediation-IP Playbook.
- Azure Firewall is ready to remediate next phases of adversary lifecycle.
- The adversary, who created a smokescreen with DDoS attack, tries to access resources in the virtual network to still sensitive data.
- Azure Firewall blocks the attacking source IP addresses from accessing the data.
Azure DDoS Protection solution
You can deploy the Azure DDoS Protection solution using the following Azure marketplace link:
The solution will install a data connector for ingesting Azure DDoS Protection diagnostics logs into Microsoft Sentinel, and two analytic rules which are the main part of this new solution:
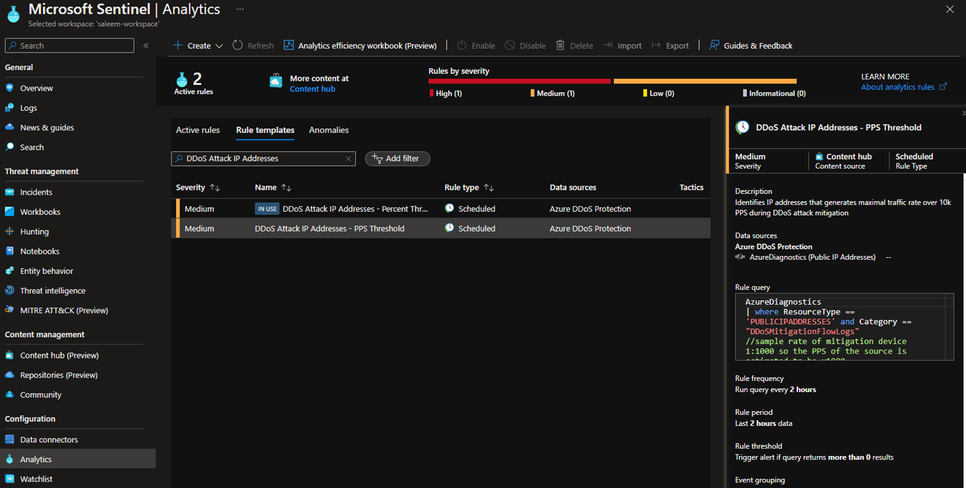
DDoS Attack IP Addresses - Percent Threshold
Identifies IP addresses that generate over 5% of traffic during DDoS attack.
DDoS Attack IP Addresses - PPS Threshold
Identifies IP addresses that generates maximal traffic rate over 10k PPS during DDoS attack.
Configuring analytic rules
Provide the required information such as subscription, resource group and workspace. Review the deployment and click on create.
After successfully deploying the solution, navigate to your Microsoft Sentinel workspace and click on Analytics. Under Rule templates, search for DDoS Attack IP Addresses and you will find the 2 new analytic rules.
Note: The analytic rules analyze Azure diagnostic logs for public IPs. To ensure that the logs are being collected, make sure that diagnostic logging is enabled on your IP resource. For more information, please refer to the tutorial on Tutorial: View and configure Azure DDoS Protection diagnostic logging | Microsoft Learn
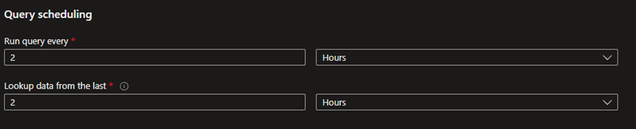
let’s create a rule using the rule template. After you click on “Create rule” navigate to Set rule logic and make sure the query scheduling is convenient for you. The default setting is to run the query every 2 hours and lookup data from the last 2 hours. You can change this setting as you see appropriate.
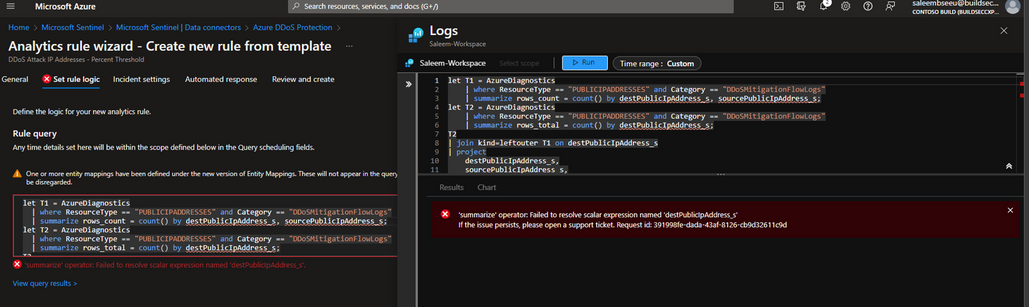
Next, we'll verify that the rule query is suitable for your environment. As we have two analytic rules, each one focuses on a different sample rate. You have the option to adjust the thresholds for both analytic rules, bearing in mind that one uses a percent threshold (default value: more than 5% of all source IPs) and the other uses a PPS (packet per second) threshold (default value: 10k PPS during DDoS attack mitigation).
If you click on “View query results” and get the following error:
The lack of logs from the "DDoSMitigationFlowLogs" category in your workspace is normal if you have not experienced a DDoS attack or performed a DDoS simulation attack. In other words, the absence of these logs indicates that there has been no DDoS attack.
Next, ensure that you keep the "Create incidents from alerts triggered by this analytics rule" option enabled. Then, review the deployment and proceed with creation.
Master Playbook Block IP Remediation
With the analytic rules configured, we can now act on any identified malicious source IPs. Microsoft Sentinel offers a Master Playbook for IP remediation, which can add these IPs to your firewall. In this example, we will use the IP group for Azure Firewall as the location to block these IPs. The Master playbook requires at least one of the playbooks mentioned here:
Azure-Sentinel/MasterPlaybooks/Remediation-IP at master · Azure/Azure-Sentinel · GitHub
Since we will use Azure Firewall in this example, refer to the AzureFirewall Block IP Nested Remediation Playbook:
Once completed, follow the instructions on the Master Playbook page (https://github.com/Azure/Azure-Sentinel/tree/master/MasterPlaybooks/Remediation-IP) to deploy the playbook
Note: The Azure DDoS solution in Microsoft Sentinel can be utilized beyond just firewall protection and the specific IP remediation playbook. The output from the analytic rules is the source IPs, which can be used by other playbooks to proactively block cyber-attacks, regardless of the technology you choose to implement.
Create an automation rule
We've successfully deployed and configured both DDoS analytics rules and IP blocking remediation. The final step is to connect these two parts through an automation rule.
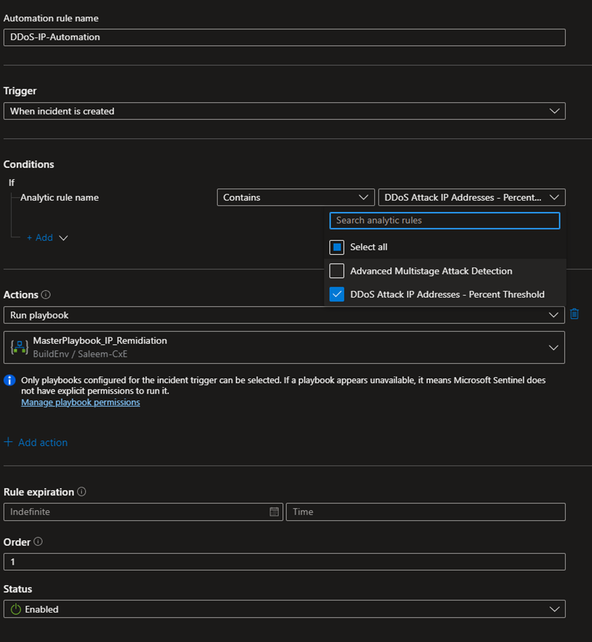
Navigate again to your Microsoft Sentinel workspace and click on “Automation”. Create a new automation rule and give it a name.
In the "Conditions" section, select "Contains" and choose the analytic rule we previously configured. Under "Actions", select "Run Playbook" and select the Master playbook for IP remediation. Finally, click "Apply" to create the automation rule.
Simulating a DDoS attack
With the setup configured and ready. Next step is testing the solution. You can simulate a DDoS attack using our approved testing partners. To find more information see Azure DDoS Protection simulation testing | Microsoft Learn
Make sure the public IP you’re using for this test is under Azure DDoS Protection before starting the simulation attack. Refer to this link for step-by-step DDoS Network Protection configuration Quickstart: Create and configure Azure DDoS Network Protection using the Azure portal | Microsoft Learn
Summary
The combination of Azure DDoS protection and Azure Firewall provides a comprehensive solution to protect against cyber-attacks. This integration enables you to quickly identify and respond to potential attacks, ensuring maximum protection against L3 and L4 types of threats. By using Azure DDoS protection, Azure Firewall and Microsoft Sentinel together, you get a unified and automated solution for defending against network and DDoS attacks, making it easier to manage and monitor your network security.
Additional resources
Azure DDoS Protection Overview | Microsoft Learn
Published on:
Learn moreRelated posts
Microsoft Dataverse – Monitor batch workloads with Azure Monitor Application Insights
We are announcing the ability to monitor batch workload telemetry in Azure Monitor Application Insights for finance and operations apps in Mic...
Copilot Studio: Connect An Azure SQL Database As Knowledge
Copilot Studio can connect to an Azure SQL database and use its structured data as ... The post Copilot Studio: Connect An Azure SQL Database ...
Retirement of Global Personal Access Tokens in Azure DevOps
In the new year, we’ll be retiring the Global Personal Access Token (PAT) type in Azure DevOps. Global PATs allow users to authenticate across...
Azure Cosmos DB vNext Emulator: Query and Observability Enhancements
The Azure Cosmos DB Linux-based vNext emulator (preview) is a local version of the Azure Cosmos DB service that runs as a Docker container on ...
Azure Cosmos DB : Becoming a Search-Native Database
For years, “Database” and “Search systems” (think Elastic Search) lived in separate worlds. While both Databases and Search Systems oper...