Traffic Manager Integration with Azure API Management - 404 resource not found error
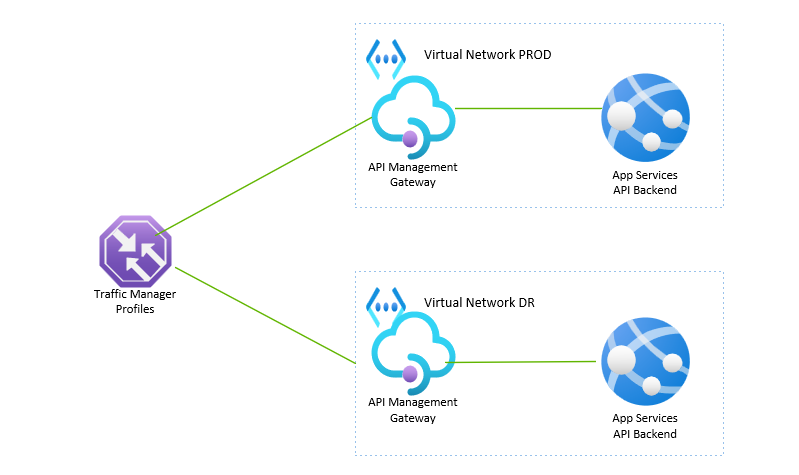
To implement disaster recovery and high availability for API backends we can either place traffic manager or front door services in front of APIM.
Traffic Manager is a DNS based global load balancing solution. It is accessed via the http://<domain>.trafficmanager.net URL.
Most often users comes across the following issue during Traffic Manager implementation
{
"statusCode": 404,
"message": "Resource not found"
}
The above is because Traffic Manager is not able to handle layer 7 traffic correctly.
This article provides step by step guidance on Traffic manager for managing disaster recovery of APIs across two regions.
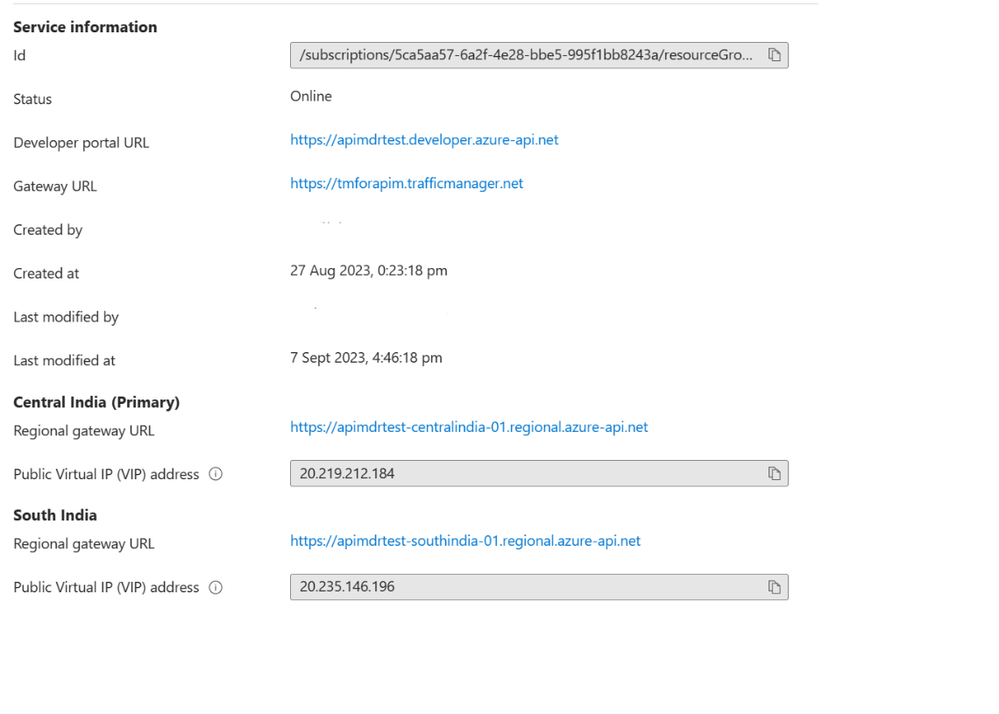
We have used APIM premium SKU with gateway deployed in Central India and South India regions as shown in the screenshot below
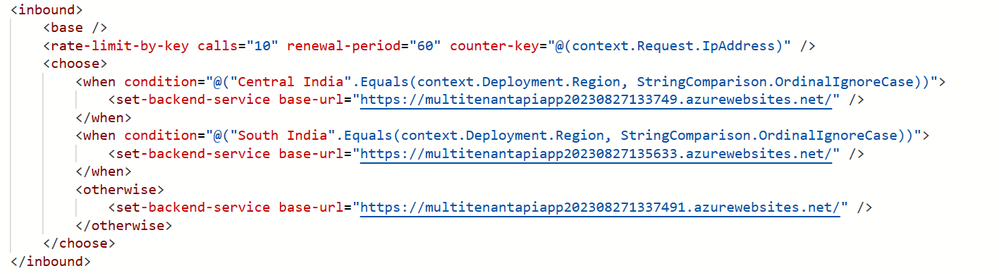
Configure Inbound Routing Policy in the API definition created inside APIM and specify the regional backend URLs of your APIs. This is required for APIM to internally manage the routing.
As a next step create a Traffic Manager profile and configure the Central India and South India APIM gateway URLs as backend endpoints .
Configure the APIM healthcheck URLs in Traffic Manager configuration navigation to ensure the endpoints are running healthy.
For Traffic Manager to effectively route traffic to APIM endpoints you need to first create a certificate for the complete Traffic Manager domain name "<domain>.trafficmanager.net"
You can use utility such as “mkcert” to generate a certificate file. Use the versions appropriate to your operating system.
Rename the .p12 certificate file .pfx and save it in a secured location. Note the password generated in the above process.
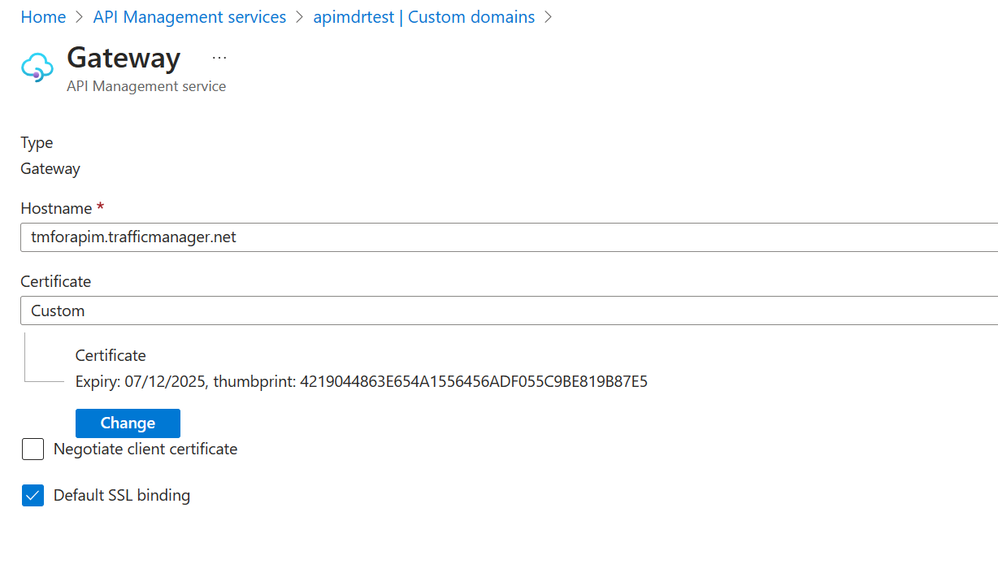
Now associate this certificate with APIM custom domains.
Navigate to APIM->Custom domain and click the add button. Type the traffic manager DNS name in the hostname section and chose certificate type as custom. Select the certificate from the saved location and provide the certificate password (generated at the time of creating the certificate). Select “Default SSL Binding” checkbox and save the settings.
Now open a new browser session and type in the traffic manager URL of your API application and it will get routed by the API management to the correct regional endpoint.
Successful routing to primary region as shown below
Successful routing to secondary region as shown below
Published on:
Learn moreRelated posts
Microsoft Purview: Data Lifecycle Management- Azure PST Import
Azure PST Import is a migration method that enables PST files stored in Azure Blob Storage to be imported directly into Exchange Online mailbo...
How Snowflake scales with Azure IaaS
Microsoft Rewards: Retirement of Azure AD Account Linking
Microsoft is retiring the Azure AD Account Linking feature for Microsoft Rewards by March 19, 2026. Users can no longer link work accounts to ...
Azure Function to scrape Yahoo data and store it in SharePoint
A couple of weeks ago, I learned about an AI Agent from this Microsoft DevBlogs, which mainly talks about building an AI Agent on top of Copil...
Maximize Azure Cosmos DB Performance with Azure Advisor Recommendations
In the first post of this series, we introduced how Azure Advisor helps Azure Cosmos DB users uncover opportunities to optimize efficiency and...
February Patches for Azure DevOps Server
We are releasing patches for our self‑hosted product, Azure DevOps Server. We strongly recommend that all customers stay on the latest, most s...
Building AI-Powered Apps with Azure Cosmos DB and the Vercel AI SDK
The Vercel AI SDK is an open-source TypeScript toolkit that provides the core building blocks for integrating AI into any JavaScript applicati...
Time Travel in Azure SQL with Temporal Tables
Applications often need to know what data looked like before. Who changed it, when it changed, and what the previous values were. Rebuilding t...