Simplify and Centrally Manage Virtual Networks Using Azure Virtual Network Manager
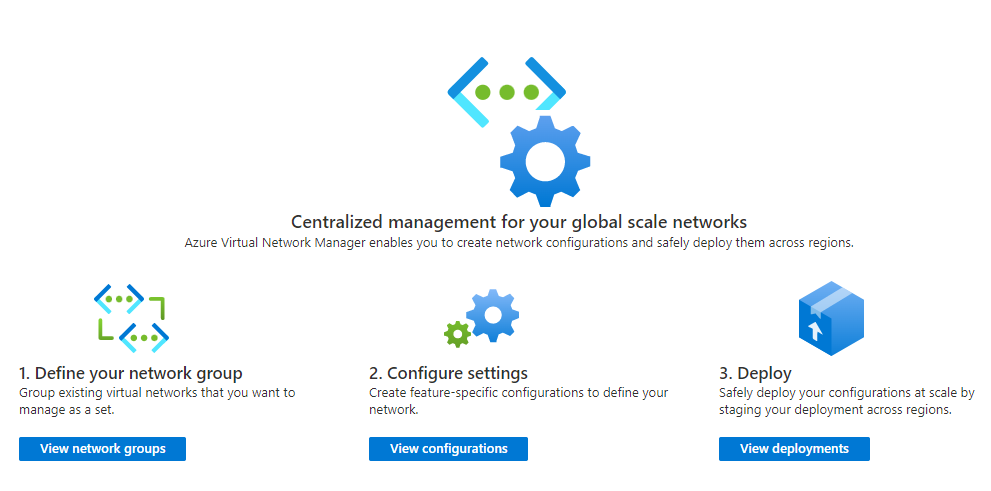
Today, we are excited to announce the public preview of Azure Virtual Network Manager (AVNM)! AVNM is a highly scalable and available network management solution that enables customers to simplify and scale their virtual networks in Azure. Customers have sought enterprise-scale network resource configuration and management in Azure. With the ability to define and apply connectivity and security configurations to their entire network in Azure, AVNM is their one-stop shop to centralized network management across regions and subscriptions.

AVNM allows users to create logical groups of virtual networks, define and apply connectivity configurations that build their desired topology of virtual networks, define and apply security configurations to protect their network environments with admin rules that precede NSG rules, and deploy these configurations safely in desired regions.
Let’s dive into how AVNM can help customers build out entire network topologies, apply security rules consistently across their deployment, and manage network configurations at scale with confidence and simplicity.
Network Groups & Dynamic Membership
Network groups allow you to apply configurations at scale for your virtual networks by categorizing your virtual networks into logical groups. You can group your virtual networks by environment, department, functionality, or other business needs. Using the network group, you can apply the AVNM configurations to the virtual networks at scale. For example, you can have all your production virtual networks in a network group and test environment virtual networks in another network group. Then, you simply apply different configuration settings (e.g., the production network group to have a strict security one) to the network groups.
A network group can have static and dynamic membership. In static membership, you explicitly define the virtual networks to be in the network group. Using dynamic membership, you can specify the virtual networks with criteria using name, ID, resource group, tags, subscriptions, etc. For instance, you can easily select virtual network groups whose names contain “production.”
AVNM will automatically react to the changes in your dynamic membership, so you don’t need to configure your virtual networks manually. For instance, when there is a new virtual network that meets the criteria of the production network group appearing in your environment, AVNM will automatically apply the configuration you defined for this virtual network.
Connectivity Configurations
With a connectivity configuration, customers can create connections between a multitude of virtual networks at once. Connectivity configurations consist of either a mesh or hub and spoke topology.
In a mesh topology, a connection is established between each virtual network within the network groups that this configuration is applied to.
A hub and spoke topology creates peerings between a selected hub virtual network and each spoke network group’s virtual networks. Direct connectivity is also available for hub and spoke to create additional peerings between each virtual network within a spoke network group. For example, if a customer wants to connect all their production and test virtual networks to a hub virtual network, they can create a connectivity configuration with a hub and spoke topology with their production and test network groups as the spokes. Then, if the customer wants each virtual network inside their production network group to be peered, they can select direct connectivity as an option for that network group.
Security Admin Configurations
Using the security admin configuration, you can create high-priority security rules (security admin rules) to protect your virtual networks. Security admin rules are evaluated prior to NSG rules, and NSG owners cannot modify, so you can make sure these rules are followed. The use cases can include enforcing organizational security policies and creating guardrail rules for your company. For example, you can allow application owners to use NSGs for their network security demands, and, as a network administrator, you use the security admin rules to enforce your company’s security policies.
In addition, you can ensure all of your resources are always protected by the rules. For example, you can apply the security admin configuration blocking the traffic from high-risk ports to your production network group, and all of the existing virtual machines and newly created ones will be protected.
The security admin configuration feature is integrated with various products. For example, you can see the effective security rules in Virtual Machine and Network Watcher. Network Watcher’s IP flow verify feature also supports security admin rules.
Resources to Get You Started
Published on:
Learn moreRelated posts
Azure SDK Release (January 2026)
Azure SDK releases every month. In this post, you'll find this month's highlights and release notes. The post Azure SDK Release (January 2026)...
Azure Cosmos DB TV Recap – From Burger to Bots – Agentic Apps with Cosmos DB and LangChain.js | Ep. 111
In Episode 111 of Azure Cosmos DB TV, host Mark Brown is joined by Yohan Lasorsa to explore how developers can build agent-powered application...
Accelerate Your Cosmos DB Infrastructure with GitHub Copilot CLI and Azure Cosmos DB Agent Kit
Modern infrastructure work is increasingly agent driven, but only if your AI actually understands the platform you’re deploying. This guide sh...
Accelerate Your Cosmos DB Infrastructure with GitHub Copilot CLI and Azure Cosmos DB Agent Kit
Modern infrastructure work is increasingly agent driven, but only if your AI actually understands the platform you’re deploying. This guide sh...
SharePoint: Migrate the Maps web part to Azure Maps
The SharePoint Maps web part will migrate from Bing Maps to Azure Maps starting March 2026, completing by mid-April. Key changes include renam...
Microsoft Azure Maia 200: Scott Guthrie EVP
Azure Cosmos DB TV Recap: Supercharging AI Agents with the Azure Cosmos DB MCP Toolkit (Ep. 110)
In Episode 110 of Azure Cosmos DB TV, host Mark Brown is joined by Sajeetharan Sinnathurai to explore how the Azure Cosmos DB MCP Toolkit is c...
Introducing the Azure Cosmos DB Agent Kit: Your AI Pair Programmer Just Got Smarter
The Azure Cosmos DB Agent Kit is an open-source collection of skills that teaches your AI coding assistant (GitHub Copilot, Claude Code, Gemin...