Troubleshooting the 403 error for User Delegation SAS in Azure Storage

It is recommended to use the Azure AD credentials to authorize your request while performing Azure Storage operations. Using the account key to access Storage account will be at the risk of getting security compromised.
If you have a requirement to access the Storage Account from your application using SAS then you can use Azure AD credentials to create a user delegation SAS for better security.
To create a user delegation SAS, you must first request a user delegation key, which is then used to sign the SAS.
The user delegation key is like the account key used to sign a service SAS or an account SAS, except that it relies on your Azure AD credentials. To request the user delegation key, call the Get User Delegation Key operation. You can then use the user delegation key to create the SAS. Refer this article.
This blog covers the steps that should be followed to isolate the issue related to the User Delegation SAS failure and outlines the various causes for 403 error while accessing the Azure Blob Storage account using User Delegation SAS.
Pre-requisites:
- Azure Subscription
- Azure CLI
- Azure Storage Account
- Azure AD Service Principal
- A sample application that creates the User Delegation SAS to perform the Blob Operation. In this blog we are using .NET sample code which is explained here.
Steps to create user-delegation SAS:
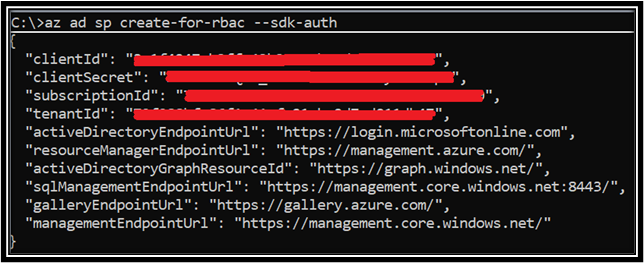
1. Create the Azure AD Service Principal using the below command:
az ad sp create-for-rbac --sdk-auth
You can also use the below command:
az ad sp create-for-rbac -n "MyApp" --role Contributor --scopes /subscriptions/{SubID}/resourceGroups/{ResourceGroup1}
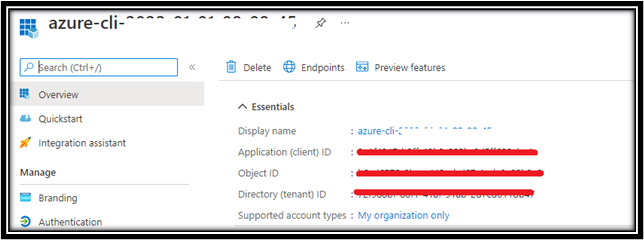
2. Save the Client ID, Tenant ID and the Client Secret safely. You can gather these details from the Azure AD portal but the secret will be hidden:
3. You can then use the above details like TenantID, ClientID and Client secret in your application to generate the User Delegation key.
Using this key you can generate any number of SAS. This is how a sample user delegation SAS looks like:
skoid=******&sktid=*****&skt=2022-01-01T08%3A49%3A01Z&ske=2022-01-08T08%3A49%3A01Z&sks=b&skv=2019-02-
02&sv=2019-02-02&st=2022-01-01T08%3A49%3A16Z&se=2022-01-01T09%3A49%3A16Z&sr=b&sp=r&sig=******
You can see that this has additional fields when compared to a normal SAS. Each of these fields is explained in detail in this article.
4. You can append this User delegation SAS token to your request URL and perform your blob operations.
Troubleshooting User Delegation SAS failure issues:
You can rely on the diagnostics logs to see the failing status code and the User Delegation SAS used by the application. This article talks about how to enable the diagnostic logs in Azure Storage account.
Let’s investigate the various causes of 403 error while using the user delegation SAS to access the Storage Account.
Error #1: AuthorizationPermissionMismatch
<Code>AuthorizationPermissionMismatch</Code>
<Message>This request is not authorized to perform this operation using this permission.
Requestld : 9cc207d7-****-****-714e-42f5c1000eeo
Time : 2022-01-01T18:34:25.6931134Z
Cause: Users will receive AuthorizationPermissionMismatch error in these scenarios.
- Insufficient SAS permissions. For Example, trying to do a write operation with a SAS which only permits read.
- Insufficient RBAC permissions. For example, trying to do a write operation while user does not have necessary RBAC permissions on the object.
Error #2– AuthenticationFailed
<Code>AuthenticationFailed</Code><Message>Server failed to authenticate the request. Make sure the value of Authorization header is formed correctly including the signature.
RequestId: dce2850b-****-****-27e6-d55ac3000000
Time:2022-01-01T00:53:08.8695267Z</Message><AuthenticationErrorDetail>Signature not valid in the specified time frame: Start [Wed, 29 Dec 2021 22:30:08 GMT] – Expiry [Wed, 29 Dec 2021 22:35:08 GMT] – Current [Wed, 29 Dec 2021 22:35:10 GMT]</AuthenticationErrorDetail>
Cause: Users will receive AuthenticationFailed error in these scenarios.
- If the request is made after the SAS token has expired or if the SAS token expires while the request is still active.
- If the request is made after the delegation key has expired.
- If the request is made after the User delegation key has been revoked.
Error #3: AuthorizationFailure
<Code>AuthorizationFailure</Code>
<Message>This request is not authorized to perform this operation using this permission.
Requestld : 9bb327a7-****-****-824e-24f6a2000000
Time : 2022-01-01T18:54:26.2548765Z
Cause: Users will receive this error in case the request is coming from an IP which is not authorized through the SAS they are using. Verify the "sip" field and match it with the IP that the customer is making the request from.
Follow the Isolation steps for troubleshooting the UserDelegation SAS auth failures:
|
Step |
Details |
|
1 |
These are new fields specific to User Delegation SAS. If those are not present, troubleshoot this as if it is normal SAS |
|
2 |
Api version used for Rest request. Only versions > “2018-11-09” are supported |
|
3 |
skoid, sktid, skt and ske – All of these fields are mandatory. Fail if any of these fields are missing |
|
4 |
Token start and end time should be within delegation key start time/end time. |
|
5 |
Request start time should be within start and end time of the SAS Token. |
|
6 |
Make sure customer’s signature matches with the signature storage service creates. An example of when this will fail is if SAS was created for container X but request was made for container Y |
|
7 |
Make sure SAS authorization passes. If token permits “Read” but request is for “Write”, it should fail. Field to check “sp” |
|
8 |
Make sure OAuth (RBAC Auth) passes. If it’s a write operation but user only has “Read” RBAC permissions. The request should fail. |
Reference articles:
https://docs.microsoft.com/en-us/rest/api/storageservices/create-user-delegation-sas
https://docs.microsoft.com/en-us/azure/storage/blobs/storage-blob-user-delegation-sas-create-cli
Hope this helps.
Published on:
Learn moreRelated posts
Automating Business PDFs Using Azure Document Intelligence and Power Automate
In today’s data-driven enterprises, critical business information often arrives in the form of PDFs—bank statements, invoices, policy document...
Azure Developer CLI (azd) Dec 2025 – Extensions Enhancements, Foundry Rebranding, and Azure Pipelines Improvements
This post announces the December release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) Dec 2025 – Extensions En...
Unlock the power of distributed graph databases with JanusGraph and Azure Apache Cassandra
Connecting the Dots: How Graph Databases Drive Innovation In today’s data-rich world, organizations face challenges that go beyond simple tabl...
Azure Boards integration with GitHub Copilot
A few months ago we introduced the Azure Boards integration with GitHub Copilot in private preview. The goal was simple: allow teams to take a...
Microsoft Dataverse – Monitor batch workloads with Azure Monitor Application Insights
We are announcing the ability to monitor batch workload telemetry in Azure Monitor Application Insights for finance and operations apps in Mic...
Copilot Studio: Connect An Azure SQL Database As Knowledge
Copilot Studio can connect to an Azure SQL database and use its structured data as ... The post Copilot Studio: Connect An Azure SQL Database ...
Retirement of Global Personal Access Tokens in Azure DevOps
In the new year, we’ll be retiring the Global Personal Access Token (PAT) type in Azure DevOps. Global PATs allow users to authenticate across...
Azure Cosmos DB vNext Emulator: Query and Observability Enhancements
The Azure Cosmos DB Linux-based vNext emulator (preview) is a local version of the Azure Cosmos DB service that runs as a Docker container on ...