Configure rate limits for different API operations in Azure API Management
Azure API Management (APIM) is one of the PaaS products offered by Azure which allows you to publish, manage, secure and monitor APIs. One of the features of APIM is the ability to control the traffic to your APIs using policies such as rate limits and quotas.
Rate limits are policies that prevent API usage spikes on a per subscription or per key basis by limiting the call rate to a specified number per a specified time period. Quotas are policies that enforce a hard limit on the number of calls that can be made to an API within a billing period.
In this blog post, we will focus on how to configure rate limits for different operations in APIM using the `rate-limit-by-key` policy. This policy allows you to define expressions to identify the keys that are used to track traffic usage. You can use any arbitrary string value as a key, such as IP address, subscription ID, etc.
Scenario
Let's say you have two operations in your API: Operation A and Operation B. You want to apply different rate limits for each operation based on your business requirements. For example:
- Operation A has a rate limit of 5 calls per minute
- Operation B has a rate limit of 5 calls per 30 seconds
You also want to make sure that the rate limits are independent by operation, meaning that calling one operation does not affect the counter for another operation.
Solution
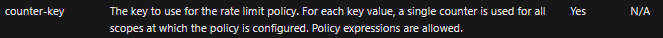
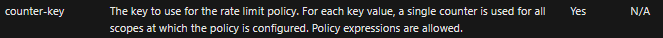
As per our official document, operations in APIM (regardless API) use a single counter for all scopes at which the policy is configured. Say, if you make 2 calls to one operation, these calls will be counted towards the single counter used by all of the operations.
To achieve this scenario, you need to use the `rate-limit-by-key` policy with an expression that produces unique values for different operations. One way to ensure that is to add `context.Operation.Id` to the expression.
The `context.Operation.Id` property returns a unique identifier for each operation in your API. By concatenating it with another value such as IP address or subscription ID, you can create a key that is specific for each operation and each caller.
Here is an example of how you can apply this policy at the inbound section of your API:
To test this solution, you can use any tool that can send HTTP requests such as Postman or curl. You can also use Azure Portal's Test console feature.
Note: Due to the distributed nature of throttling architecture, rate limiting is never completely accurate. The difference between the configured and the actual number of allowed requests varies based on request volume and rate, backend latency, and other factors.
You can also customize this policy by adding optional attributes such as increment-condition or quota-exceeded-response-code. For more details on how this policy works and what options are available, see: https://learn.microsoft.com/en-us/azure/api-management/rate-limit-by-key-policy
In this blog post, we have seen how to configure rate limits for different operations of an API in Azure API Management using the `rate-limit-by-key` policy.
This policy allows us to define expressions to identify the keys that are used to track traffic usage.
We have also seen how to use `context.Operation.Id` as part of the key expression to ensure that the rate limits are independent by operation.
We hope this blog helps you!
Published on:
Learn moreRelated posts
Azure Developer CLI (azd): One command to swap Azure App Service slots
The new azd appservice swap command makes deployment slot swaps fast and intuitive. The post Azure Developer CLI (azd): One command to swap Az...
9 hours ago
Azure IaaS: Build, run, and optimize infrastructure
11 hours ago