New Threat Detections for Azure WAF
Introduction:
Web applications face frequent malicious attacks that exploit well-known vulnerabilities, such as Code Injection and Path Traversal Attacks. These attacks are hard to prevent in the application code, as they require constant maintenance, patching, and monitoring at multiple levels of the application architecture. A WAF solution can provide faster and centralized security by patching a known vulnerability for all web applications, rather than securing each one individually. Azure Web Application Firewall (WAF) is a cloud-native service that protects web apps from common web-hacking techniques. It can be deployed quickly to gain full visibility into the web application traffic and block malicious web attacks.
By integrating Azure WAF with Microsoft Sentinel (Cloud Native SIEM solution), you can automate the detection and response to threats/incidents/alerts and save time, and effort, on updating the WAF policy. This blog will show you how to build Analytic rules/detections in Sentinel for attacks such as Code Injection.
Azure WAF Detection Queries for Web Application Attacks:
The Azure-Network-Security GitHub Repository now contains the following pre-built queries that can be used for creating Analytic rules in Sentinel. These Analytic Rules will help with automated detection and response for attacks like Code Injection, Path Traversal and scanner-based attacks.
- Detection query for Code Injection Attacks (App GW and AFD WAF): A code injection attack is a type of cyberattack that involves injecting malicious code into an application. The application then interprets or executes the code, affecting the performance and function of the application.
- Detection query for Path Traversal Attacks (APP GW and AFD WAF): A path traversal attack is a type of cyberattack that involves manipulating the file paths of an application to access files and directories that are stored outside the web root folder. The attacker can use special character sequences, such as …/ or …\, to move up the directory hierarchy and access sensitive or confidential data, such as configuration files, source code, or system files.
- Detection query for Scanner-based Attacks (APP GW WAF): A scanner-based web attack is a type of cyberattack that involves using a web vulnerability scanner to find and exploit security weaknesses in web applications. A web vulnerability scanner is a tool that automatically scans web applications for common vulnerabilities, such as SQL injection, XSS, CSRF, and path traversal. The attacker can use the scanner to identify the vulnerable targets and launch attacks to compromise them.
Setting up Analytic Rules in Sentinel for Web Application Attacks:
The prerequisites for setting up Analytic Rules are:
- A working WAF and a Log Analytic Workspace that is configured to receive logs from the respective APP GW or AFD. This page provides the necessary steps for this configuration.
- Additionally, Microsoft Sentinel should be enabled for the Log Analytic Workspace that is being used here.
The following steps need to be implemented to successfully configure an Analytic Rule in Sentinel
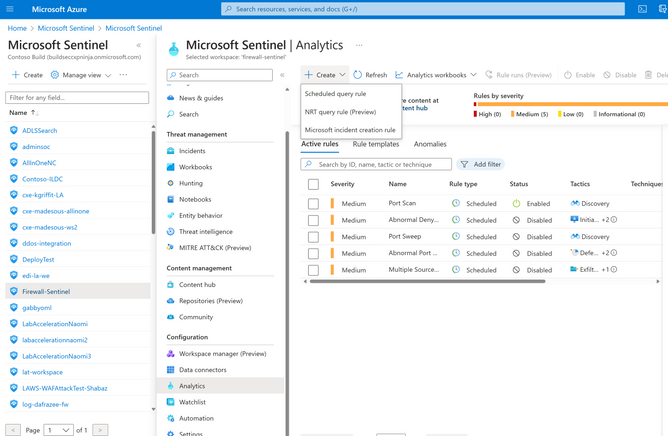
- Navigate to Microsoft Sentinel and Select the Analytics tab. Click on Create and select “Scheduled query rule”.
- The tactics and techniques provided here are informational only and are sourced from MITRE Attack Knowledgebase (A knowledge base of adversary tactics and techniques based on real-world observations).
- The severity information given below is to set a severity level for the incident created because of this rule. Since these are major attacks, we are choosing High Severity here.
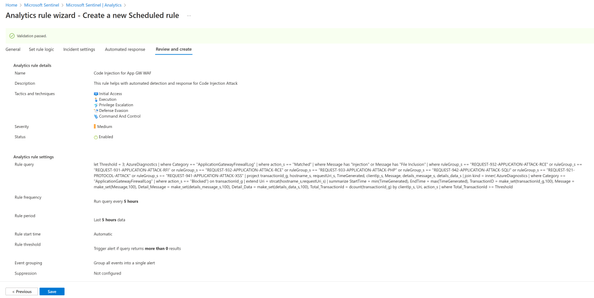
- On the Set rule logic page, enter the below prebuilt Code Injection query: This query can be found in Azure-Network-Security GitHub Repository. Likewise, you can use any other query that is available in the repository to create Analytic rules and detect respective attack patterns.
let Threshold = 3;
AzureDiagnostics
| where Category == "ApplicationGatewayFirewallLog"
| where action_s == "Matched"
| where Message has "Injection" or Message has "File Inclusion"
| where ruleGroup_s == "REQUEST-932-APPLICATION-ATTACK-RCE" or ruleGroup_s == "REQUEST-931-APPLICATION-ATTACK-RFI" or ruleGroup_s == "REQUEST-932-APPLICATION-ATTACK-RCE" or ruleGroup_s == "REQUEST-933-APPLICATION-ATTACK-PHP" or ruleGroup_s == "REQUEST-942-APPLICATION-ATTACK-SQLI" or ruleGroup_s == "REQUEST-921-PROTOCOL-ATTACK" or ruleGroup_s == "REQUEST-941-APPLICATION-ATTACK-XSS"
| project transactionId_g, hostname_s, requestUri_s, TimeGenerated, clientIp_s, Message, details_message_s, details_data_s
| join kind = inner(
AzureDiagnostics
| where Category == "ApplicationGatewayFirewallLog"
| where action_s == "Blocked") on transactionId_g
| extend Uri = strcat(hostname_s,requestUri_s)
| summarize StartTime = min(TimeGenerated), EndTime = max(TimeGenerated), TransactionID = make_set(transactionId_g,100), Message = make_set(Message,100), Detail_Message = make_set(details_message_s,100), Detail_Data = make_set(details_data_s,100), Total_TransactionId = dcount(transactionId_g) by clientIp_s, Uri, action_s
| where Total_TransactionId >= Threshold
Note: It is important to make sure that the WAF logs are already in the Log Analytic Workspace before you create this Analytical rule. Otherwise, Sentinel will not recognize some of the columns in the query and you will have to add extra input like “| extend action_s = column_ifexists(“action_s”, “”), transactionId_g = column_ifexists(“transactionId_g”, “”)” for each column that gives an error. This input will create the column names manually and assign them null values. To skip this step, send the WAF logs to the workspace first.
- On the Incident Settings Page, Enable the “Create incidents from alerts triggered by this analytics rule.” The Alert grouping can be configured as required.
- Optionally, you can also add any automated response to the incident if needed. The detailed information on automated response configuration can be found in this blog here.
- Finally, Click Save on the Review and Create tab.
This analytic rule enables Sentinel to create an incident based on the WAF logs that record any Code Injection attacks. The Azure WAF blocks these attacks by default, but the incident creation provides additional support for the security analyst to respond to future threats.
Conclusion:
In this way, we can configure Analytic Rules in Sentinel for various web application attacks using the pre-built detection queries available in the Net Sec GitHub Repository. We are also working on adding these queries directly to Sentinel Detection Templates, once added, these queries will be directly available in the Analytic Rule Templates section of Sentinel.
Published on:
Learn moreRelated posts
Azure Cosmos DB TV Recap: Supercharging AI Agents with the Azure Cosmos DB MCP Toolkit (Ep. 110)
In Episode 110 of Azure Cosmos DB TV, host Mark Brown is joined by Sajeetharan Sinnathurai to explore how the Azure Cosmos DB MCP Toolkit is c...
Introducing the Azure Cosmos DB Agent Kit: Your AI Pair Programmer Just Got Smarter
The Azure Cosmos DB Agent Kit is an open-source collection of skills that teaches your AI coding assistant (GitHub Copilot, Claude Code, Gemin...
Introducing Markers in Azure Maps for Power BI
We’re announcing a powerful new capability in the Azure Maps Visual for Power BI: Markers. This feature makes it easier than ever for organiza...
Azure Boards additional field filters (private preview)
We’re introducing a limited private preview that allows you to add additional fields as filters on backlog and Kanban boards. This long-reques...
What’s new with Azure Repos?
We thought it was a good time to check in and highlight some of the work happening in Azure Repos. In this post, we’ve covered several recent ...