Azure WAF Protection for Third Party Cloud Applications (AWS)
There are differing reasons for cross cloud connectivity such as cost implications, ease of management, vendor lock in, regional availability etc. Azure Network Security tools may be applicable for resources domiciled in a non-Azure cloud environment.
Azure Application Gateway and WAF may be used to publish and secure non azure applications (on-prem or other third-party clouds). You can also do a redirection (HTTP to HTTPS) to ensure all communications between the application and its users occur over a secured path. In this blog, we'll show you how to do this with an app in AWS.
Leveraging Azure WAF for Applications in Amazon AWS
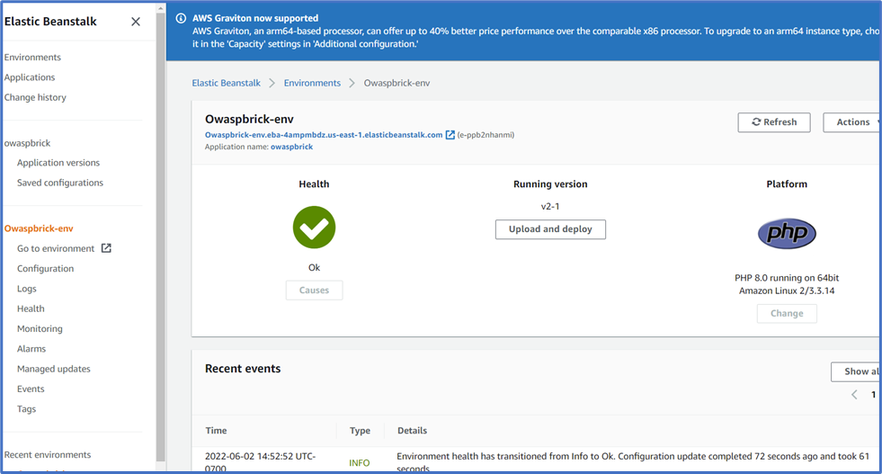
In the Elastic Beanstalk environment below, I have deployed an open-source application called Owaspbrick - a sample brick shop portal used to test OWASP vulnerabilities. This app in the AWS cloud would serve as the backend host. To access this app through our Application Gateway Public IP, connections and access will be secured and managed with WAF in our Application Gateway using the specified port in our listener.
(Note: You can use an application of your choice in AWS. In this test scenario, OWASP Bricks has been used as the test app).
- If you already have an AWS account (or you can obtain a trial account), you can go to Elastic Beanstalk in AWS and create an application. The app type platform in this example is PhP. We called it Owaspbrick.
- Once the app is created, download the sample application for Owaspbrick.
- Go back to the app just created and Click “Configuration” in the left plane. Under Software, you can specify the path to the index page of the application.
- Since a compressed file was uploaded for your application, you will need to specify the next layer as the root, so you can insert /owaspbrisk-master/ in this field. Or whatsoever is the name of the compressed directory.
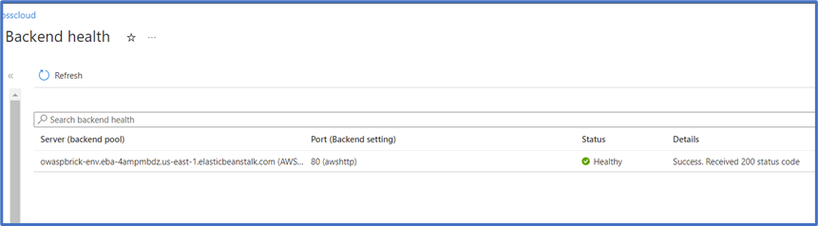
- Confirm the health is OK and then click “Go to environment” from the left plane to view the OWASP application directly. Copy the URL app as you will need this in setting up the backend pool of the application gateway.
Azure Application Gateway WAF Setup
In this example, we create a listener in our Application Gateway called AWSlistener. App Gateway WAF may be associated on 3 levels: App Gateway, HTTP listener and URI path). You may use an application on any of the specified scopes for this test. This application has been deployed on the App Gateway level.
Part A: Set Up App Gateway to access resource in AWS as a back-end host
- Create an APP Gateway with a HTTP listener AWSlistener. Assign Port 80.
-
Add back-end host: AWSbackendpool (Target type: insert AWS <appUrl>).
- Add a rule to route access from the HTTP listener AWSlistener to the AWS backend target AWSbackend.
- Confirm access to AWS app via App Gateway using App Gateway IP and Port e.g., “AppgatewayPublicIP:80”. 
If the app is not accessible due to backend health error 502 (make sure to set up a custom probe that references your app URL as it’s host)
Now that we have confirmed access via Application Gateway, we need to restrict all access to the Application Gateway IP address in AWS to prevent direct access to our application
Part B: Restrict access to AWS app to only AppGateway Public IP
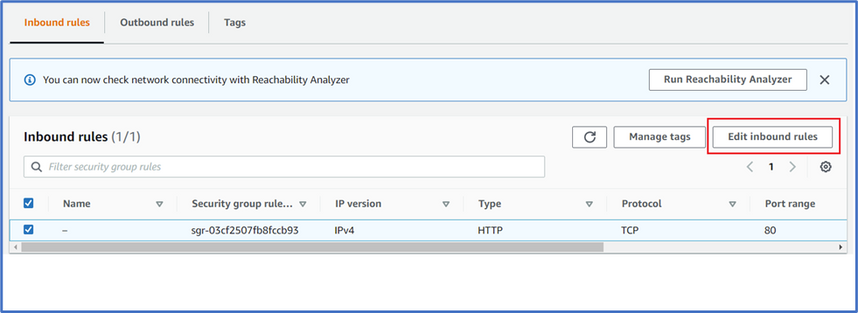
Go to Security Groups in AWS and Select the Security Group for the Web app. (You can type “Security Group” in the AWS portal search bar, then select the Security Group attached to your web app).
- Click Inbound rules and Select “Edit Inbound rules”.
- Insert Public IP of the App Gateway and use this to access the web. (You can try to initiate traffic from another IP Source) and even the original link should no longer grant access. Make sure to review port restricting as health probes for external endpoints like in this case will also use the App Gateway’s public IP as the source IP.
Part C: Create or update a WAF policy to use our listener to do different restrictions
You can configure the WAF policy to suit your needs. This includes custom rules, disabling rules/rule groups, exclusions, setting file upload limits etc. If you skip this step, all defaults will be selected.
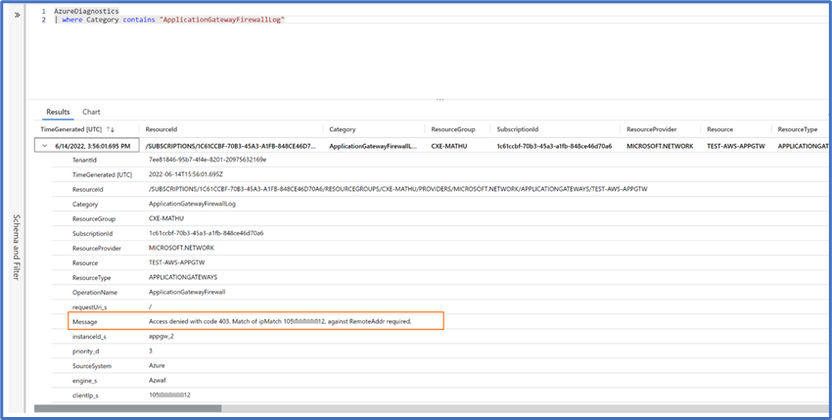
Custom rule: Create a rule to deny access from a Public IP in the Custom rules session of the WAF. Confirm Access denied.
# Create the rule
$variable4 = New-AzApplicationGatewayFirewallMatchVariable `
-VariableName RemoteAddr
$condition4 = New-AzApplicationGatewayFirewallCondition `
-MatchVariable $variable4 `
-Operator IPMatch `
-MatchValue "10X.XX.XX.12" `
-NegationCondition $False
$rule = New-AzApplicationGatewayFirewallCustomRule `
-Name myrule4 `
-Priority 3 `
-RuleType MatchRule `
-MatchCondition $condition4 `
-Action Block
# Get the existing policy
$awsapppolicy = Get-AzApplicationGatewayFirewallPolicy -Name awspolicy -ResourceGroupName Test_CXE_SEA
# Add the newly created rule
$awsapppolicy.CustomRules.Add($rule)
# Update the policy
Set-AzApplicationGatewayFirewallPolicy -InputObject $awsapppolicy
Confirm that access from the specified IP address has been restricted.
If access is not restricted, you should confirm that your Policy is in Prevention mode and check the logs for the action on the IP address.
(Note: Setting up the MySQL database was not covered in this scope, you can however set up mysql in AWS; go to the config folder to update the parameters in setup.php and head to <appgatewayIP>/ config to access the database. See readme file in the OWASP Bricks zipped folder).
Published on:
Learn moreRelated posts
Azure Developer CLI (azd) Dec 2025 – Extensions Enhancements, Foundry Rebranding, and Azure Pipelines Improvements
This post announces the December release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) Dec 2025 – Extensions En...
Unlock the power of distributed graph databases with JanusGraph and Azure Apache Cassandra
Connecting the Dots: How Graph Databases Drive Innovation In today’s data-rich world, organizations face challenges that go beyond simple tabl...
Azure Boards integration with GitHub Copilot
A few months ago we introduced the Azure Boards integration with GitHub Copilot in private preview. The goal was simple: allow teams to take a...
Microsoft Dataverse – Monitor batch workloads with Azure Monitor Application Insights
We are announcing the ability to monitor batch workload telemetry in Azure Monitor Application Insights for finance and operations apps in Mic...
Copilot Studio: Connect An Azure SQL Database As Knowledge
Copilot Studio can connect to an Azure SQL database and use its structured data as ... The post Copilot Studio: Connect An Azure SQL Database ...
Retirement of Global Personal Access Tokens in Azure DevOps
In the new year, we’ll be retiring the Global Personal Access Token (PAT) type in Azure DevOps. Global PATs allow users to authenticate across...
Azure Cosmos DB vNext Emulator: Query and Observability Enhancements
The Azure Cosmos DB Linux-based vNext emulator (preview) is a local version of the Azure Cosmos DB service that runs as a Docker container on ...
Azure Cosmos DB : Becoming a Search-Native Database
For years, “Database” and “Search systems” (think Elastic Search) lived in separate worlds. While both Databases and Search Systems oper...