How Azure Backup Immutability help you protect against Ransomware threats
Ransomware attacks deliberately encrypt or erase data and systems to force your organization to pay money to attackers. These attacks target not just your data, but even your backups. The best way to prevent falling victim to ransomware is to implement preventive measures and have tools that protect your backup data - one such feature is Immutable Vault.
Immutable Vault (currently in preview) can help you protect your backup data by blocking any operations that could lead to loss of existing recovery points. Enabling this property helps you ensure that recovery points once created cannot be deleted before their intended expiry. While this helps prevent data loss, you would not be able to perform certain operations on this vault and its protected items.
How does it protect
The following table summarizes list the supported operations, behavior (i.e. what’s allowed and what’s blocked) and support for the Vault types.
|
Operation Type |
Blocked |
Allowed |
Backup Vault |
Recovery Services Vault |
|
Stop protection with delete data |
A protected item can't have its recovery points deleted before their respective expiry date. |
You can still stop protection of the instances while retaining data forever or until their expiry. |
Supported |
Supported |
|
Modify backup policy to reduce retention |
Any actions that reduce the retention period in a backup policy are disallowed on Immutable vault. |
You can make policy changes that result in the increase of retention. You can also make changes to the schedule of a backup policy. |
Not Supported |
Supported |
|
Change backup policy to reduce retention |
Any attempt to replace a backup policy associated with a backup item with another policy with retention lower than the existing one is blocked. |
You can replace a policy with the one that has higher retention. |
Not Supported |
Supported |
How does it work
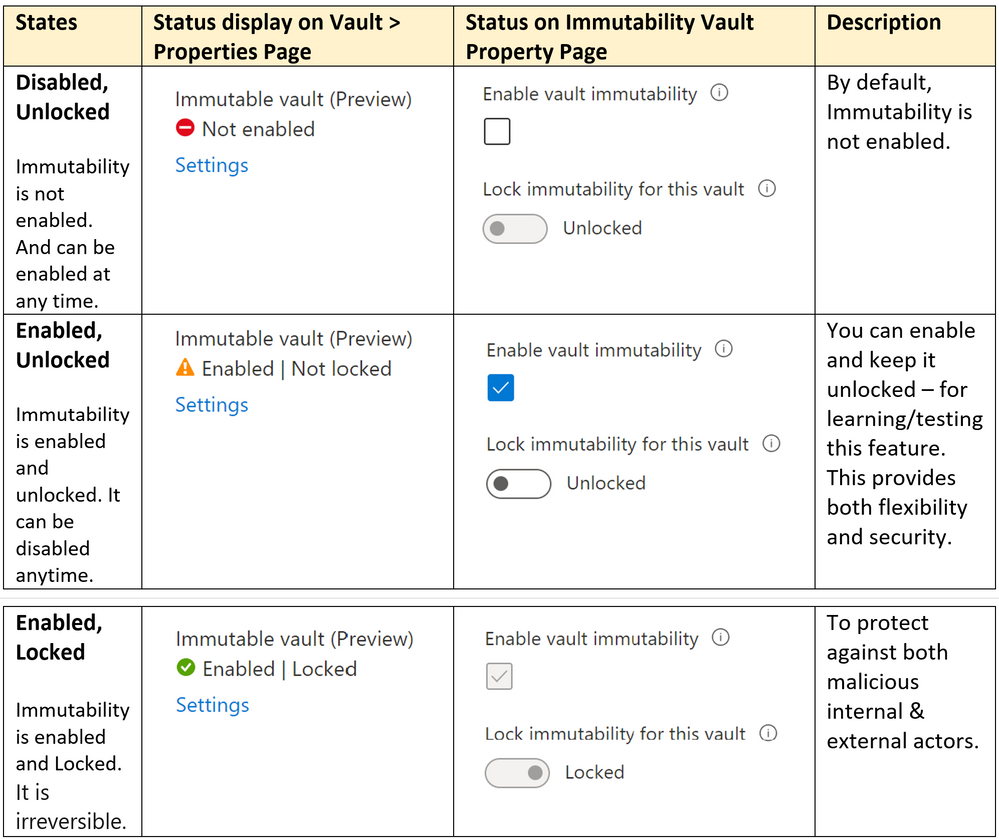
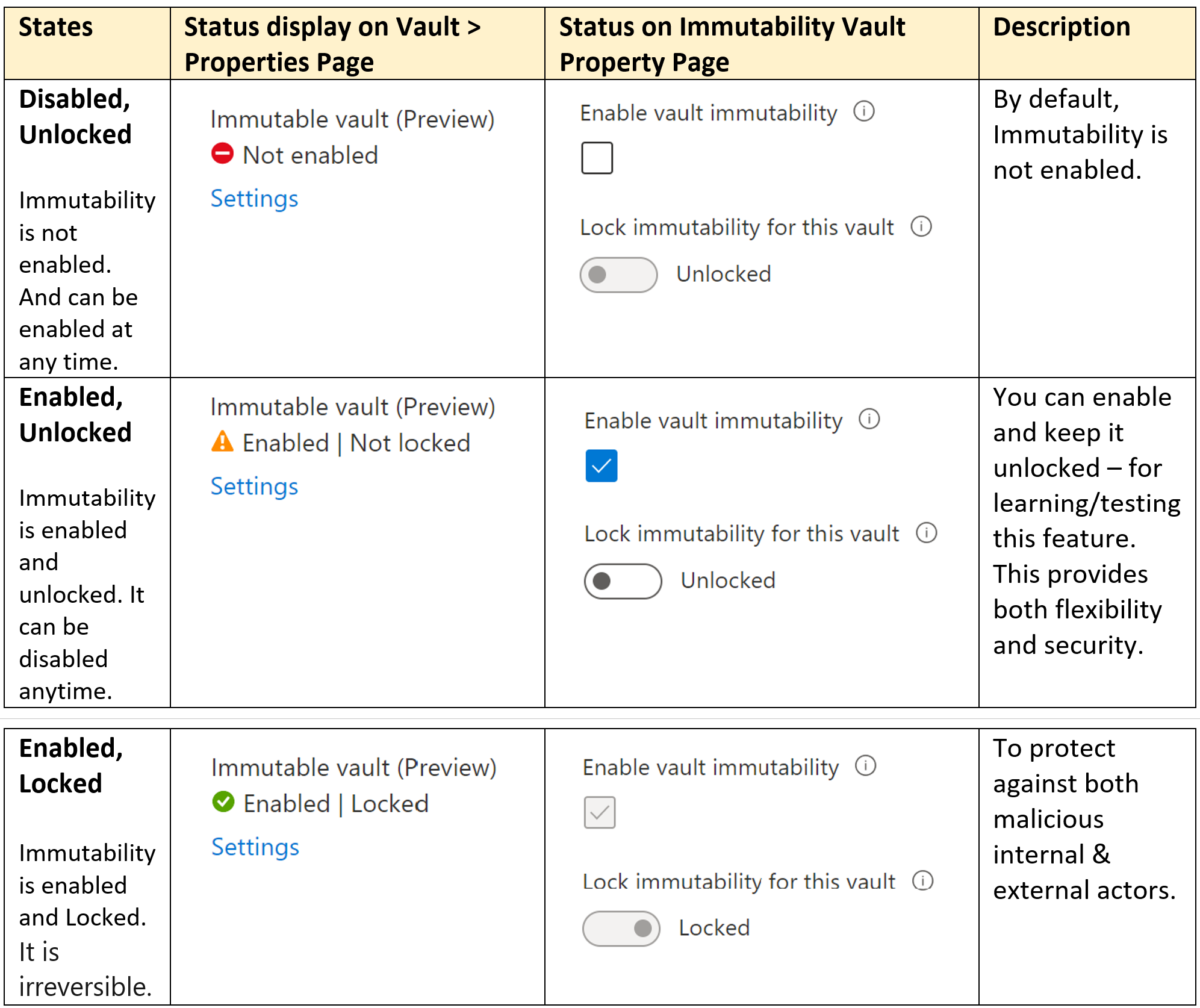
This is a Vault level Property. This is an opt-in capability, by default it is disabled. The following table summarizes the various states with screenshots:
Locking Immutability
Once you enable this lock, it makes immutability setting for the vault irreversible. This will prevent any malicious actors from disabling immutability and deleting backups. While this helps secure the backup data in the vault by preventing anyone , we recommend you make a well-informed decision when opting to lock. You can also test and validate how the current settings of the vault, backup policies, and so on, meet your requirements and can lock the immutability setting later.
Additional Resources:
- https://learn.microsoft.com/en-us/azure/backup/backup-azure-immutable-vault-concept
- https://learn.microsoft.com/en-us/azure/backup/backup-azure-immutable-vault-how-to-manage
Published on:
Learn moreRelated posts
Fabric Mirroring for Azure Cosmos DB: Public Preview Refresh Now Live with New Features
We’re thrilled to announce the latest refresh of Fabric Mirroring for Azure Cosmos DB, now available with several powerful new features that e...
Power Platform – Use Azure Key Vault secrets with environment variables
We are announcing the ability to use Azure Key Vault secrets with environment variables in Power Platform. This feature will reach general ava...
Validating Azure Key Vault Access Securely in Fabric Notebooks
Working with sensitive data in Microsoft Fabric requires careful handling of secrets, especially when collaborating externally. In a recent cu...
Azure Developer CLI (azd) – May 2025
This post announces the May release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) – May 2025 appeared first on ...
Azure Cosmos DB with DiskANN Part 4: Stable Vector Search Recall with Streaming Data
Vector Search with Azure Cosmos DB In Part 1 and Part 2 of this series, we explored vector search with Azure Cosmos DB and best practices for...