How to Troubleshoot Deny Policy Step by Step

For security or compliance, your subscription administrators might assign policies that limit how resources are deployed. Deny policy, as one policy type, is used to prevent a resource request that does not match defined standards through a policy definition and fails the request. For example, deny policies that prevent creating public IP addresses, network security groups, user-defined routes, or route tables.
Document Reference: https://learn.microsoft.com/en-us/azure/governance/policy/concepts/effects#deny
This blog will show you how to troubleshoot deny policy related issues and how to fix them.
Troubleshoot RequestDisallowedByPolicy errors and non-compliant resources
[Example built-in policy]
Policy Definition Name: Storage accounts should have the specified minimum TLS version
Policy Definition ID: fe83a0eb-a853-422d-aac2-1bffd182c5d0
Scenario 1:
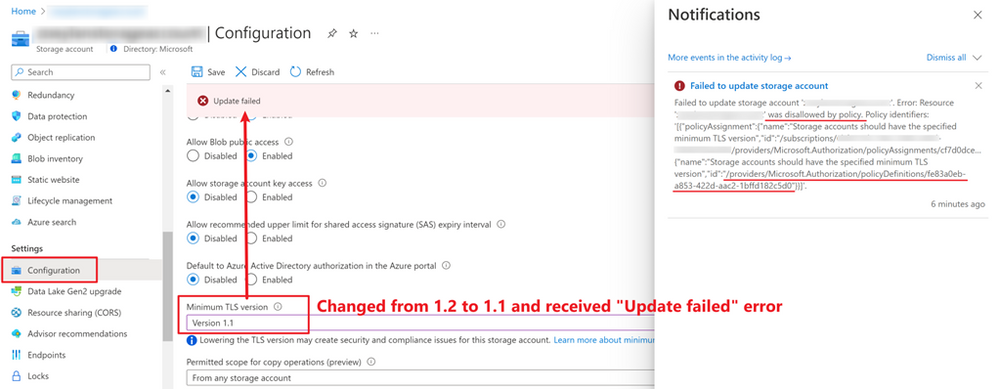
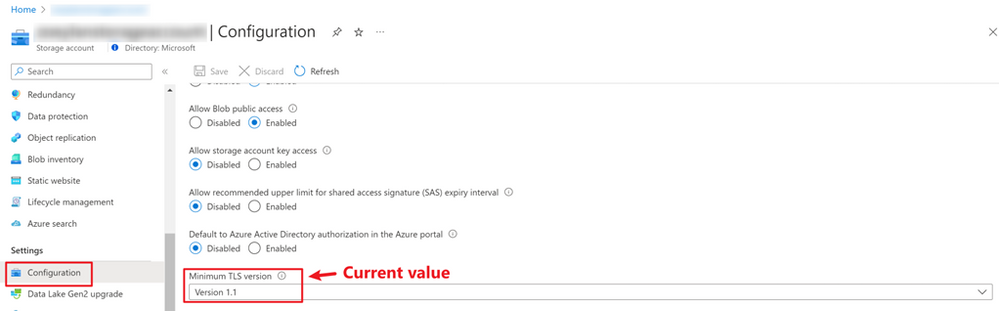
You tried to change the “Minimum TLS version” from “Version 1.2” to “Version 1.1”, but the operation failed.
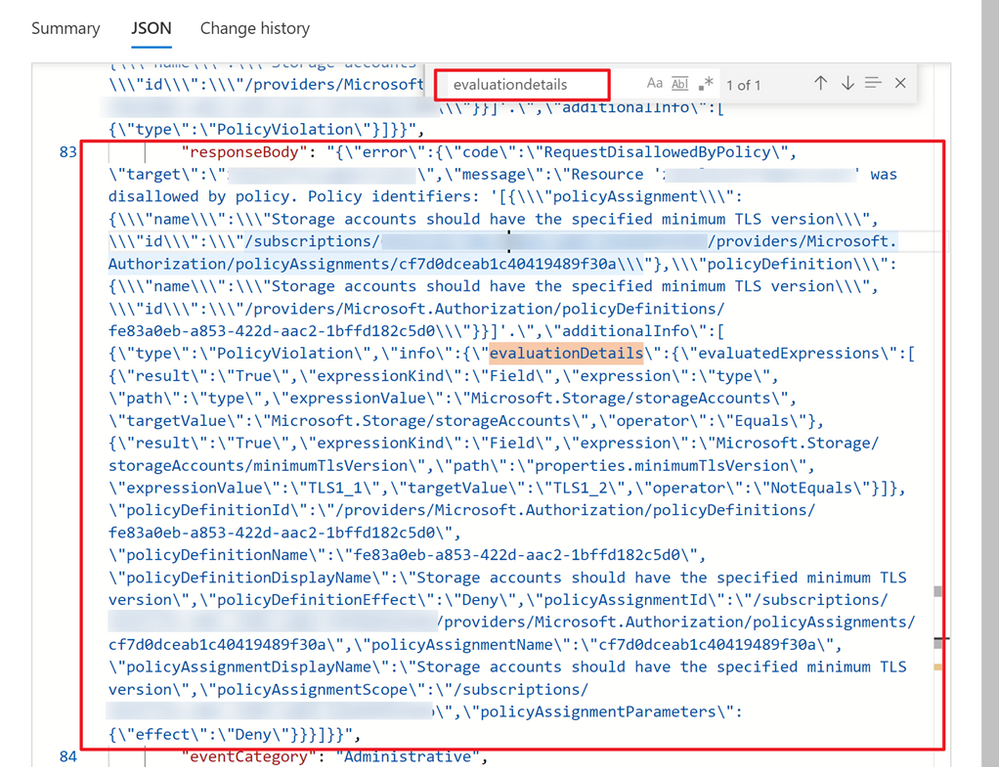
By checking the error message in the Notifications panel, it’s clear that the update operation failed because it was blocked by a policy (policy id: fe83a0eb-a853-422d-aac2-1bffd182c5d0).
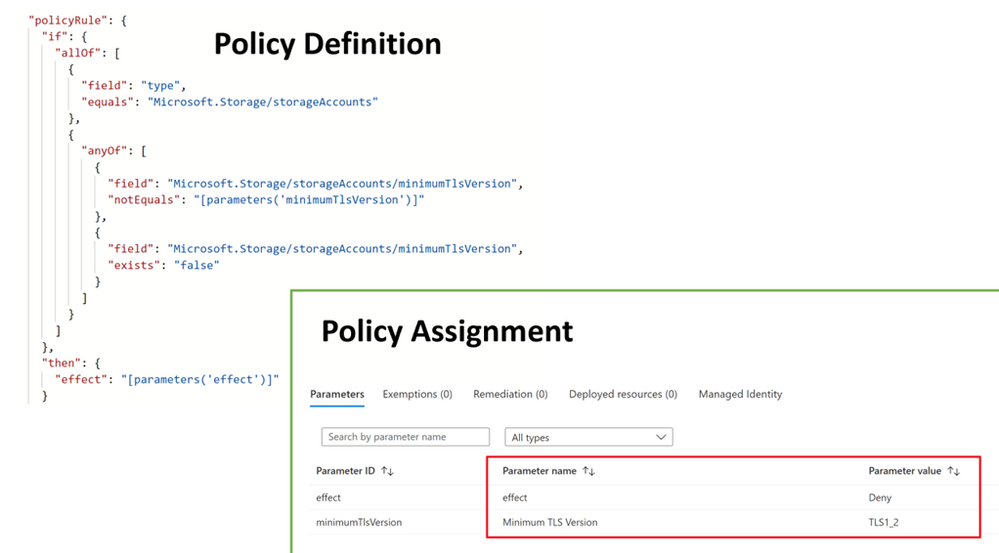
You can use the name of a policy assignment or policy definition to get more details about a policy that caused the error. Specifically, you can navigate to the policy page and find the policy definition and policy assignment based on the id shown in the error message.
By checking the “if” section in the policy definition and parameter values defined in the policy assignment, you can easily understand that the policy forces you to use the minimum TLS version ≥ 1.2. That’s why it does not allow you to change it to 1.1.
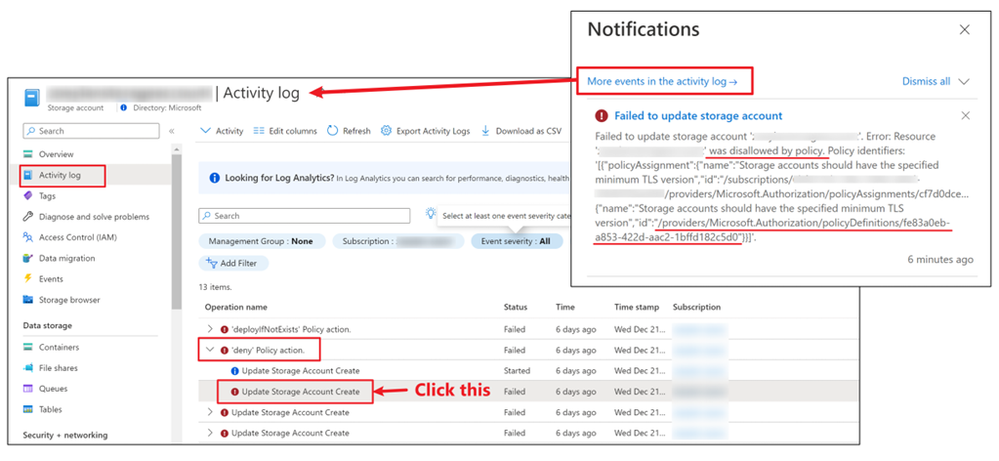
Besides, you can check similar information in the activity log.
Find the ‘deny’ Policy action and click in the failed sub record.
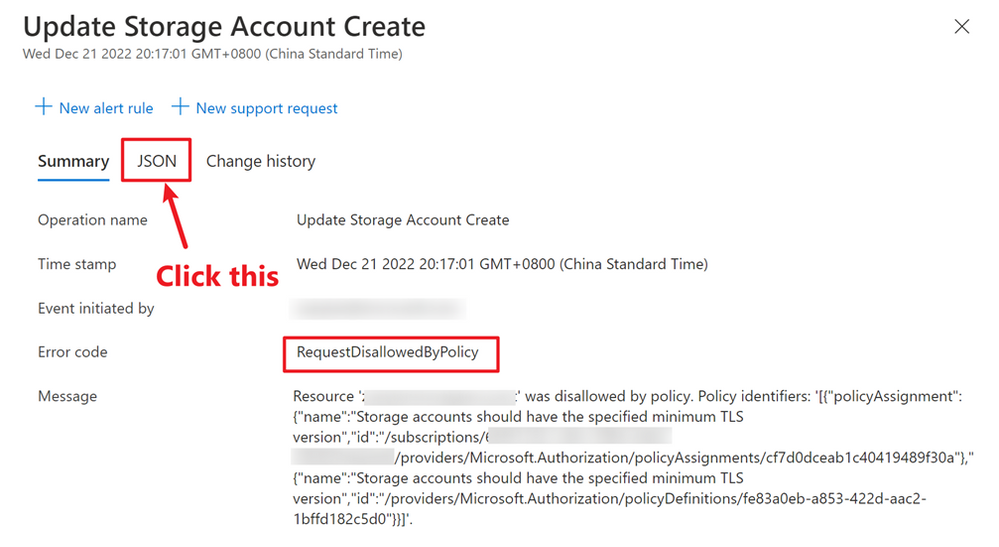
Double check the error code and make sure it’s “RequestDisallowedByPolicy”. Then, you can click the JSON to view more details of this failed operation. By searching “evaluationdetails”, you can navigate to the response body part.
By formatting the content, you can get a clear view like below, which helps you understand why the operation was blocked by the deny policy.
Solutions:
- You can keep the minimum TLS version unchanged (recommended in this example).
- Remove or disable the policy assignment (need to check with your policy admin).
- Create a policy exemption (need to check with your policy admin).
Scenario 2:
You want to figure out why some resources are shown as non-compliant on the “Compliance” page.
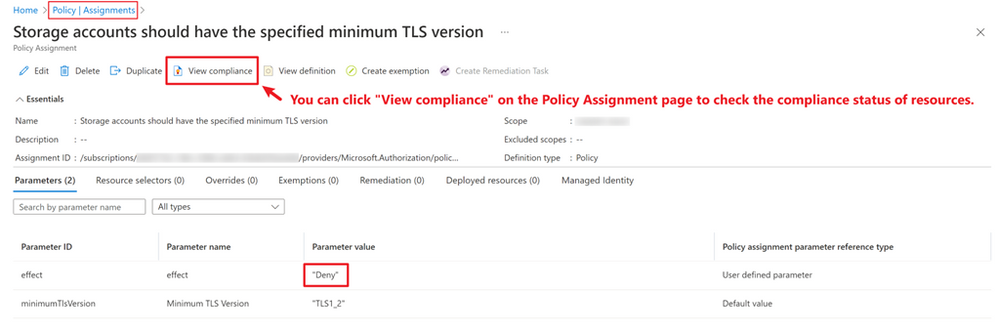
You can check compliance status for a specific policy by either finding it on the “Compliance” page or accessing through policy assignment page.
Please make sure you select the “Non-compliant” in the drop-down list to check the non-compliant resources.
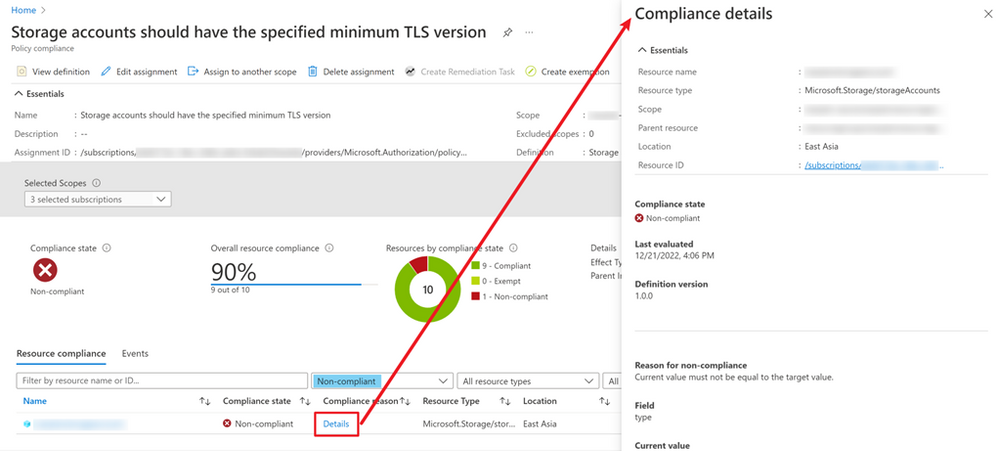
- Click the “Details” to check the compliance details
- Scroll down on the compliance details page.
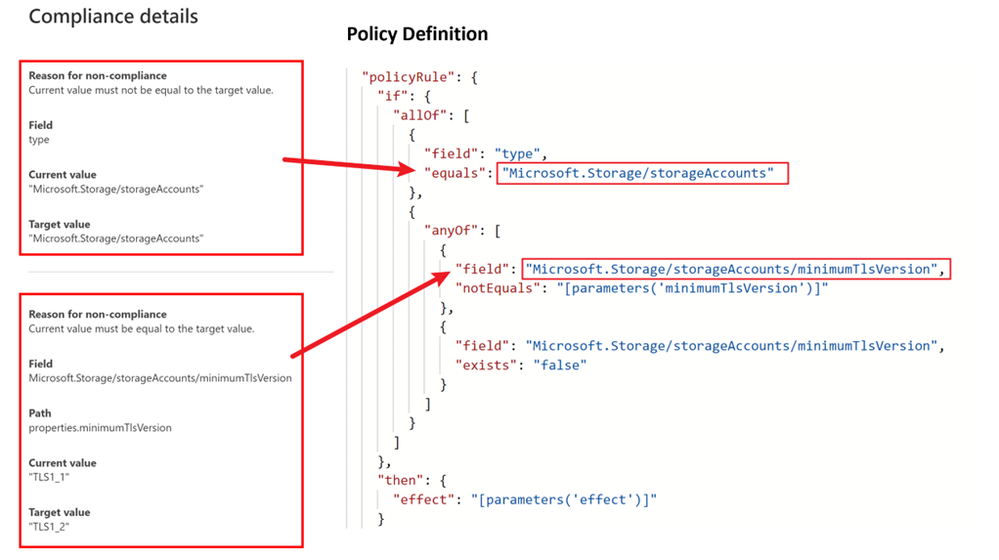
Under the “Compliance details”, there are one or more blocks for policy aliases defined in policy definition respectively. In this case shown above, the policy has to check the resource type (equals to storage account) and minimum TLS version. The first block checking the resource type shows that it’s compliant since the current value and target value matches. The second block checks minimum TLS version. The target value (defined in the policy assignment: 1.2) is different from the current value (the current storage account’s minimum TLS version allowed: 1.1).
By checking the configuration for this storage account, we can see that the current minimum TLS version value is 1.1. So, it’s expected that this storage account is shown as a non-compliant resource.
Solutions:
- Manually change the minimum TLS version to Version 1.2 from the Storage side.
- If you want to create a remediation task to manage non-compliant resources at once, you can change your policy effect from “deny” to “modify” if possible and then run a remediation task.
Published on:
Learn more