Unlocking the Power of Serverless Confidential Computing in the Cloud
Serverless confidential containers on Azure Container Instances (ACI) combine the advantages of serverless computing with the enhanced protection offered by confidential computing. Today, we are excited to announce the general availability of this solution. The release blog is available here.
This blogpost offers a discussion on key benefits, and suitability for key industries such as healthcare technology, fintech, and regulation technology (RegTech). It further discusses the motivations for adopting confidential computing in these sectors, along with relevant use cases.
The capabilities and potential applications of serverless confidential containers on ACI can help organizations make informed decisions about solutions that protect sensitive data and help maintain compliance with industry regulations.
Healthcare Technology
Healthcare technology, often referred to as Healthtech, aims to improve healthcare delivery, patient outcomes, and management using medical expertise, information technology, and innovative digital solutions.
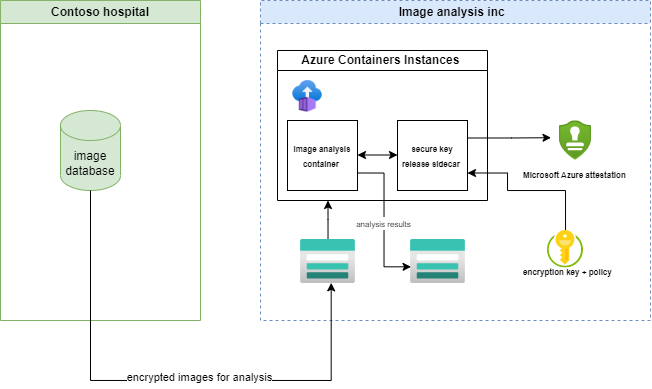
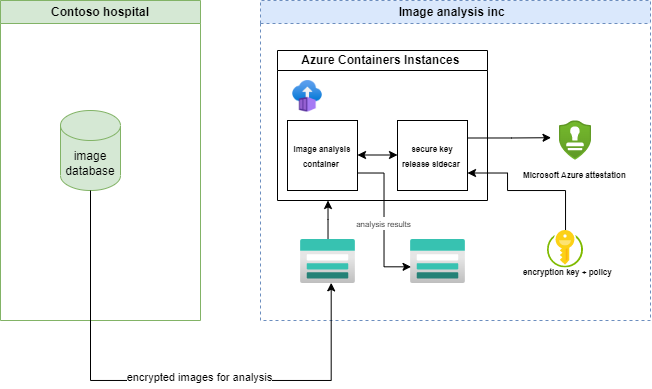
Sample Scenario: AI-powered Medical Image Analysis with Confidential Computing
In healthcare, accurate diagnosis is paramount for effective treatment. Advanced technologies, specifically AI and machine learning, have the ability to revolutionize the way medical images are analyzed, leading to improved diagnostic accuracy and enhanced patient care. However, these processes often involve handling and analyzing sensitive patient data, a critical aspect that requires stringent security measures.
Benefits of Confidential Computing for healthcare technology
Data Privacy and Security
Medical image data, such as X-rays, MRIs, and CT scans, often contain sensitive patient information, which are critical for healthcare providers to maintain strict data privacy and security measures. Confidential computing allows healthcare providers to analyze and process medical images while aiming to keep the data protected and secure.
Regulatory compliance
Healthcare organizations are subject to strict data protection regulations such as HIPAA in the United States and GDPR in Europe. By using confidential computing, healthcare providers can aim to maintain compliance with these regulations, with the goal of protecting sensitive medical image data during processing and reducing the risk of penalties and reputational damage associated with non-compliance.
Collaboration and Innovation
Medical image analysis often requires collaboration between healthcare professionals, researchers, and AI specialists. Confidential computing can enable secure data collaboration by attempting to keep medical image data encrypted and protected during processing by multiple parties. This facilitates innovation in medical imaging technology and improves patient care without compromising data privacy.
Improved Patient Outcomes
By securely processing medical image data, healthcare organizations can leverage advanced AI algorithms and machine learning models to generate more accurate diagnoses and treatment plans. This can help result in better patient outcomes and more efficient healthcare delivery.
Fintech
Fintech is a term that combines "financial" and "technology" to describe any technology that delivers financial services through software or hardware. Fintech can help individuals and businesses manage their finances, transactions, investments, and more. Fintech can also create new markets and opportunities for financial inclusion and innovation. Some examples of fintech products and companies are online banking, mobile payment apps, robo-advisors, cryptocurrency platforms, and peer-to-peer lending apps.
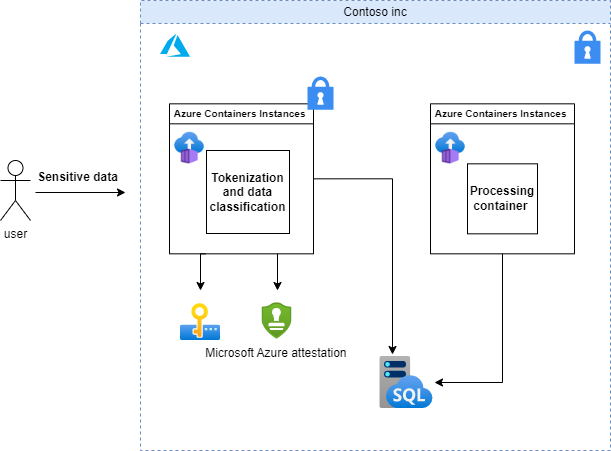
Sample scenario: Secure data ingestion with Tokenization and classification
Benefits of Confidential Computing for Fintech
Data classification and tokenization are vital processes in the fintech industry as they help manage and secure sensitive data, providing regulatory compliance, and mitigating risks associated with data breaches.
Managing Sensitive Data
Fintech companies deal with a vast amount of sensitive information, such as financial records, transaction details, and personal identification data. Data classification helps categorize and organize this data based on sensitivity and access levels, allowing companies to implement the appropriate security measures.
Regulatory compliance
Regulations such as GDPR, CCPA, and PCI-DSS recommend companies to classify, manage, and protect personal and financial data.
Mitigating Data Breach Risks
Data breaches are a significant concern in the fintech industry. Tokenization reduces the risk of breaches by substituting sensitive data with tokens that have no intrinsic value. This limits the damage in case of unauthorized access or theft.
Collaboration and Innovation
Data breaches are a significant concern in the fintech industry. Tokenization reduces the risk of breaches by substituting sensitive data with tokens that have no intrinsic value. This limits the damage in case of unauthorized access or theft, as attackers cannot exploit tokenized data.
A classification and tokenization solution built on confidential computing can provide the following properties:
Enhanced Security
Confidential computing can help design a data classification and tokenization solution that provides an additional layer of security. It aims to keep sensitive data encrypted while being processed, with the intent of reducing the risk of data leaks or breaches.
Establishing Trust
Attestation enables fintech companies to establish trust with the confidential containers and the data classification and tokenization processes running within it. This assurance is vital for managing sensitive data and maintaining regulatory compliance.
Auditing and Compliance
Attestation reports can be used as evidence of secure data processing and compliance with data protection regulations. These reports demonstrate that the fintech company has taken the necessary steps to protect sensitive data, helping to maintain customer trust and avoid potential penalties.
Regulation tech
Regulation tech, or RegTech for short, is a way of using technology to make regulatory and compliance processes easier and more efficient. RegTech can help regulated industries, such as banking and healthcare. For example, RegTech can use big data analytics to detect fraud, artificial intelligence to automate reporting, or blockchain to verify transactions. RegTech can benefit both businesses and regulators by saving time and money, reducing risks, and improving transparency.
Digital onboarding and KYC (Know Your Customer) are essential processes for any business that wants to establish trust and compliance with its customers. Digital onboarding allows customers to sign up for products or services online, without the need for physical paperwork or visits. This saves time and money for both the business and the customer and enhances customer satisfaction and loyalty. KYC is a process of verifying the identity and background of customers, to prevent fraud, money laundering, terrorism financing, or other illegal activities. By conducting KYC digitally, businesses can reduce the risk of human error, speed up the verification process, and comply with regulatory requirements.
In recent years, digital onboarding has become increasingly popular among consumers, allowing them to open accounts with banks and fintech companies without visiting a physical branch. However, despite the convenience it offers, these checks and processes are difficult to implement and can be subject to regulatory fines if not implemented correctly. To address these issues, some service providers have emerged that specialize in digital onboarding checks. However, using these services requires banks and other organizations to share sensitive customer data with the service providers, which raises data security and privacy concerns.
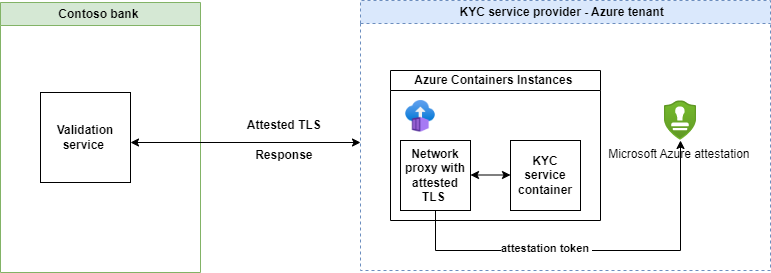
Sample Scenario: Encrypted data processing for Digital Onboarding and Know Your Customer (KYC)
Benefits of Confidential Computing for regulation technology
Enhanced Data Security
Confidential computing enables service providers to perform necessary data validations while aiming to keep users' data secure and private. By utilizing this technology, service providers can protect sensitive data, thereby improving digital onboarding processes and safeguarding customers' information.
Trust and Transparency
Confidential computing can foster trust among businesses, service providers, and customers by ensuring data is handled securely. The encryption of data during processing means businesses can trust that their sensitive data is protected, even when working with third-party providers. Customers, on the other hand, can trust that their personal data is secure and used appropriately. This transparency in data handling also supports regulatory compliance.
Regulatory Compliance
Utilizing confidential computing technology, service providers can aim to maintain compliance with regulatory standards, reducing the risk of penalties and reputational damage associated with non-compliance.
Improved Customer Experience
With confidence of enhanced data security, businesses are empowered to offer seamless digital onboarding and KYC processes. This not only improves customer satisfaction but also fosters customer loyalty.
Wrapping Up
In today's digital landscape, the need for robust data security and privacy solutions is increasingly critical. Serverless confidential containers on Azure Container Instances (ACI) offer a secure, and efficient approach to these challenges, seamlessly merging the advantages of serverless computing with the added protection of confidential computing.
This technology provides distinct advantages, including:
- Protection of Data In Use: ACI utilizes the latest AMD chipsets with confidential computing capabilities. These are designed to prevent unauthorized access to data being processed in the cloud - whether from the cloud operator or from any unauthorized source.
- Full Remote Attestation: Confidential containers on ACI provide support for remote guest attestation which is used to verify the trustworthiness of a container group. A client can review the attestation report to ensure they trust the application running in a container group before sending any sensitive data. Container groups generate an AMD SEV-SNP attestation quote which is signed by the AMD hardware and includes information about the hardware it is running on, and all the software components including container configurations. Optionally, this generated hardware attestation quote can then be verified by the Microsoft Azure Attestation service via an open sourced sidecar application before any sensitive data is processed in the container group.
- Ease of Deployment: Deploying serverless confidential containers on ACI is straightforward, minimizing the complexity and overhead associated with the implementation of secure computing solutions. This simplicity is evident in this fun example of deploying a Minecraft server on confidential containers using ACI, as illustrated in this blogpost.
By adopting confidential computing solutions like serverless confidential containers on ACI, organizations across sectors can work towards enhancing confidentiality and fostering trust among their customers and partners. As organizations continue to adopt cloud-based solutions and manage sensitive data, the implementation of confidential computing technologies will play an increasingly significant role in safeguarding information, promoting innovation, and driving business success.
Useful Resources
Published on:
Learn more