Seamless Integration: Leveraging Managed Identities to Invoke API Management from Azure Logic App
Organizations are continuously looking for ways to streamline their processes, enhance security, and improve the overall efficiency of their operations. One common challenge faced by businesses is securely accessing and managing APIs while ensuring the confidentiality and integrity of data.
In this blog, we'll explore how organizations can leverage Azure Logic App and Managed Identities to achieve seamless integration with Azure API Management, simplifying authentication and enhancing security.
Managed Identities provide a secure way for Azure services and resources to authenticate themselves to other Azure services, eliminating the need for explicit credentials or secrets. They allow services like Azure Functions and Azure Logic Apps to access other resources securely without the complexities of managing credentials.
High level steps:
Step 1: Register an application in Azure AD to represent the logic app(client application)
Step 2: Create a managed identity for Logic App
Step 3: Associate the Managed Identity to the Application Role
Step 4: Configure Logic App to trigger HTTP Action to invoke the API
Step 5: Configure a JWT validation policy in the APIM to pre-authorize requests
Step 6: Testing - Trigger the logic app to run
Step 1: Register an application in Azure AD to represent the logic app(client application)
- In your Azure Portal, go to Azure Active Directory, select App Registrations
- Select New registration
- When the Register an application page appears, enter your application's registration information:
- In the Name section, enter a meaningful application name that will be displayed to users of the app, such as client-app.
- In the Supported account types section, select an option that suits your scenario.
- Leave the Redirect URI section empty
- Select Register to create the application.
- On the app Overview page, find the Application (client) ID value and record it for later.
- Under the Manage section of the side menu, select Expose an API and set the Application ID URI with the default value. Record this value for later.
- Under the Manage section of the side menu, select App roles then click Create app role:
- In the Display name, enter a meaningful role name for example: AddRole
- Allowed member types: select Applications
- Value: example: AddRole
- Description: <as necessary>
- Do you want to enable this app role? checked
- Click Apply
- Record the role ID for later
- Repeat the step 8 to add additional App roles (if any) supported by your API.
Step 2: Create a managed identity for Logic App
You can either use system assigned managed identity or user assigned managed identity.
System assigned managed identity is tied directly to the lifecycle of the Azure resource which its assigned. When you delete the resource, the managed identity is also removed. Each resource can have only one System Assigned Managed Identity, and it can't be shared with other resources.
User Assigned Managed Identities, as the name suggests, are created explicitly by users within Azure AD. You can create them independently of Azure resources. Unlike System Assigned Managed Identities, User Assigned Managed Identities are not tied to a specific Azure resource's lifecycle. They are created and deleted independently of any resource. It can be associated with one or more Azure resources, allowing you to share the identity across different resources.
To learn more about it refer this link.
I have used system assigned managed identity for Logic App.
- Go to the Azure Portal (https://portal.azure.com/).
- Navigate to the Logic App you want to configure with Managed Identity.
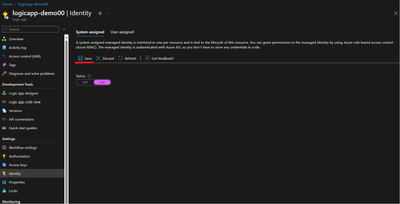
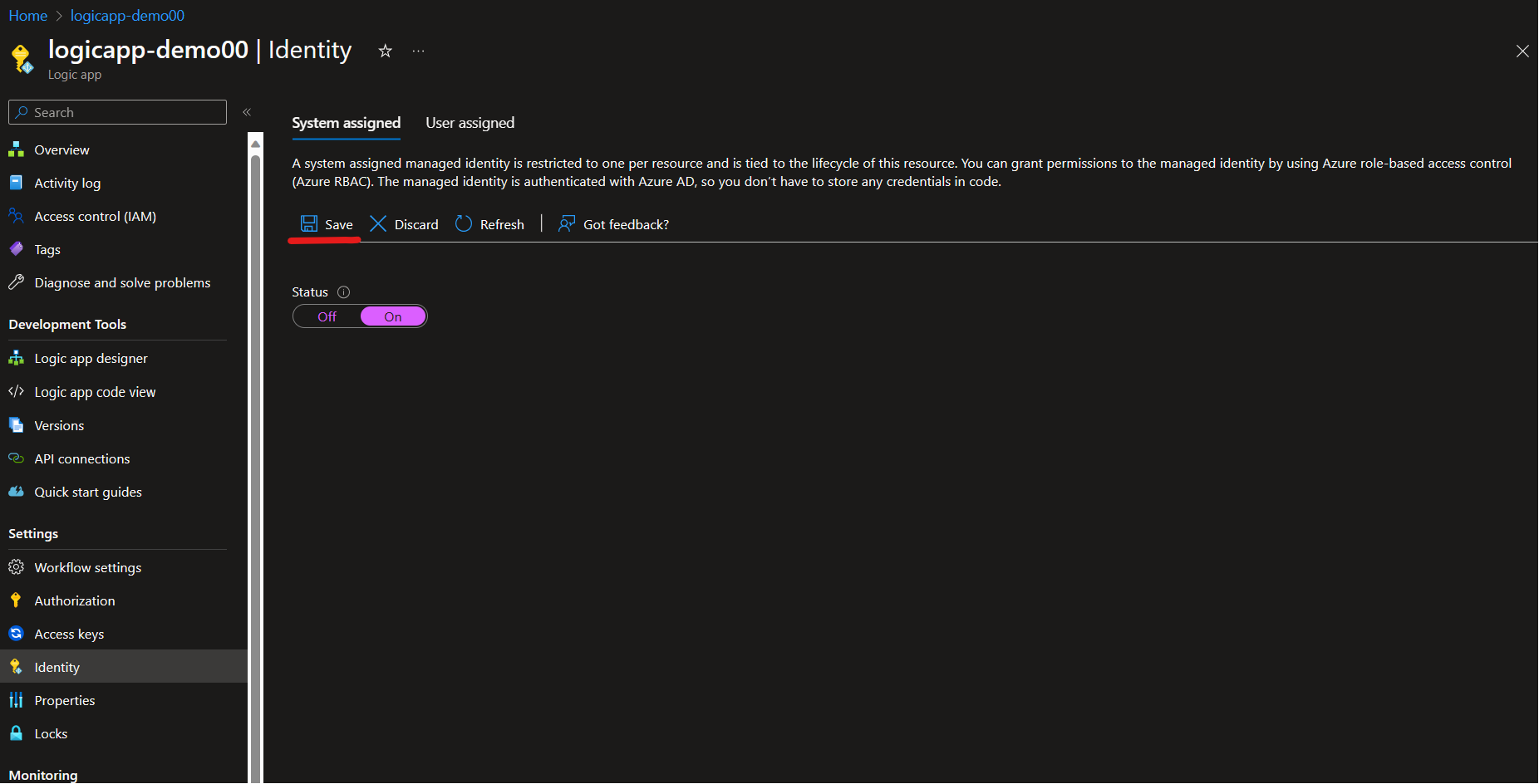
- Under the Logic App's "Settings," click on "Identity."
- In the "Identity" blade, enable the System-assigned Managed Identity for your Logic App. Click "Save."
Step 3: Assign Managed Identity access to the Application Role using powershell
Use the below script in azcli powershell to assign managed identity access to the application role
I have used the script from Microsoft docs link
Step 4: Configure Logic App to trigger HTTP Action to invoke the API
In your Logic App workflow:
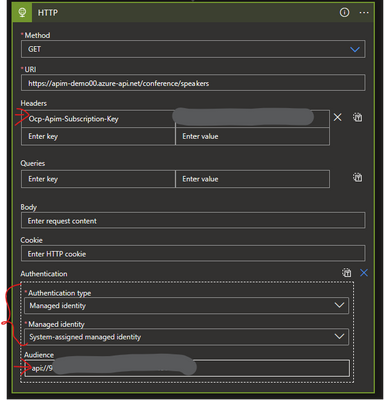
- Add an HTTP action to make requests to the APIM API endpoint
- Provide the API endpoint in the URI and select the method
-
Add the Ocp-Apim-Subscription-Key HTTP header to the request, passing the value of a valid subscription key. (you can fetch it from APIM)
-
Add authentication header and select the Authentication type as Managed Identity, select system-assigned managed identity and audience as the Application ID URI you recorded from the step 1.
Step 5: Configure a JWT validation policy in the APIM to pre-authorize requests
Add the following Validate JWT policy to <inbound> policy section of your API which checks the value of the audience claim in an access token obtained from Azure AD and checks the additional claims for the app role and returns an error message if the token is not valid. Refer this link for more information.
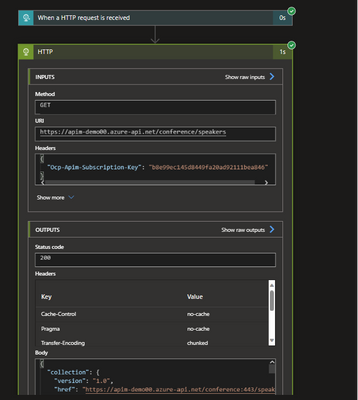
Step 6: Testing - Trigger the logic app to run
Trigger your Logic App to run, and it will use its Managed Identity to authenticate and make requests to the APIM resource.
That's it! Your Logic App is now configured to access the API Management resource using Managed Identity.
Conclusion:
The Managed Identity seamlessly handles authentication to Azure API Management, eliminating the need for managing credentials or tokens manually. Although the setup process might initially appear complex, the long-term benefits are invaluable.
With this approach, you've effectively established a password less solution for your internal API interactions. This is especially valuable for projects involving extensive system integrations, where simplicity, security, and streamlined workflows are paramount. Embracing Managed Identities paves the way for a future where secure, hassle-free API communication becomes the norm.
Published on:
Learn moreRelated posts
Azure Developer CLI (azd) – January 2026: Configuration & Performance
This post announces the January 2026 release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) – January 2026: Conf...
Azure SDK Release (January 2026)
Azure SDK releases every month. In this post, you'll find this month's highlights and release notes. The post Azure SDK Release (January 2026)...
Azure Cosmos DB TV Recap – From Burger to Bots – Agentic Apps with Cosmos DB and LangChain.js | Ep. 111
In Episode 111 of Azure Cosmos DB TV, host Mark Brown is joined by Yohan Lasorsa to explore how developers can build agent-powered application...
Accelerate Your Cosmos DB Infrastructure with GitHub Copilot CLI and Azure Cosmos DB Agent Kit
Modern infrastructure work is increasingly agent driven, but only if your AI actually understands the platform you’re deploying. This guide sh...
Accelerate Your Cosmos DB Infrastructure with GitHub Copilot CLI and Azure Cosmos DB Agent Kit
Modern infrastructure work is increasingly agent driven, but only if your AI actually understands the platform you’re deploying. This guide sh...
SharePoint: Migrate the Maps web part to Azure Maps
The SharePoint Maps web part will migrate from Bing Maps to Azure Maps starting March 2026, completing by mid-April. Key changes include renam...
Microsoft Azure Maia 200: Scott Guthrie EVP
Azure Cosmos DB TV Recap: Supercharging AI Agents with the Azure Cosmos DB MCP Toolkit (Ep. 110)
In Episode 110 of Azure Cosmos DB TV, host Mark Brown is joined by Sajeetharan Sinnathurai to explore how the Azure Cosmos DB MCP Toolkit is c...
Introducing the Azure Cosmos DB Agent Kit: Your AI Pair Programmer Just Got Smarter
The Azure Cosmos DB Agent Kit is an open-source collection of skills that teaches your AI coding assistant (GitHub Copilot, Claude Code, Gemin...