Automatic disruption of Ransomware and BEC attacks with Microsoft 365 Defender

The ever-growing volume of advanced cybersecurity attacks challenges even the most advanced Security Operations (SOC) teams. Image 1 shows a timeline of a typical human-operated ransomware attack where the attacker encrypted hundreds of devices in just minutes. It demonstrates how quickly threat actors spread and execute attacks and highlights the criticality to quickly identify and contain high-impact attacks to limit the impact to organizations.
To help SOC teams address these challenges, we announced automatic attack disruption in Microsoft 365 Defender last year at Microsoft Ignite. This capability uses high-confidence Extended Detection and Response (XDR) signals across endpoints, identities, email, and SaaS apps, to contain active cybersecurity attacks quickly and effectively, to stop progression and limit the impact to your organization.
Today, we are excited to announce the expansion of the public preview to cover business email compromise (BEC) campaigns, in addition to human-operated ransomware (HumOR) attacks.

The impact of automatic attack disruption
Automatic attack disruption is designed to contain attacks in progress by automatically disabling or restricting devices and user accounts used in an attack. Disabling credentials available to the attacker, as well as their ability to use devices that communicate over the network, limits the ability to impact additional assets and gives SOC teams more time to remediate attacks.
Unlike known protection methods such as prevention and blocking based on a single indicator of compromise, attack disruption in Microsoft 365 Defender leverages the breadth of our XDR signal to act at the incident level and takes the entire attack into account.
This game-changing capability comes built-in with Microsoft 365 Defender and limits a threat actor’s progress early on - reducing the overall impact of an attack, from associated costs to loss of productivity.
Tackling advanced attacks
Business email compromise and human-operated ransomware attacks are two common attack scenarios that are now supported by Microsoft 365 Defender’s automatic attack disruption capabilities to reduce their impact on an organization:
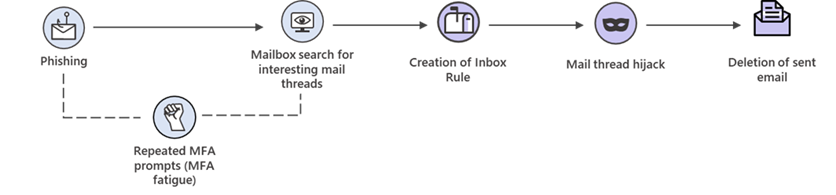
Business email compromise – BEC attacks commonly involve cybercriminals impersonating a company's executives or vendors to trick employees into transferring money or sensitive information - causing financial losses and reputational damage. Automatic attack disruption can help detect these attacks and remove the attacker’s access to the environment by disabling the compromised account, limiting their ability to send fraudulent email, and preventing money transfers and financial losses.
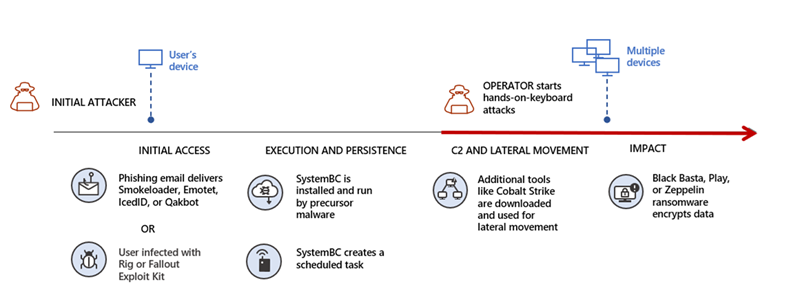
Human-operated ransomware – Our analysis of dozens of ransomware cases shows that once a Threat Actor moves to deploy ransomware in a network, a SOC analyst has less than 20 minutes from deployment to effectively mitigate the attack. This narrow time frame, coupled with the high technical skills and time required to perform the analysis, makes manually responding near impossible. The attack shown in image 3 used elevation of privileges and deployed ransomware to critical data. Here, automatic attack disruption will contain the spreader device and disable the compromised user account.
How we establish high confidence in Microsoft 365 Defender when taking automatic action
We understand that taking automatic action can come with hesitation, given the potential impact it can have on an organization. That’s why automatic attack disruption in Microsoft 365 Defender is designed to rely on high-fidelity XDR signals, coupled with insights from the continuous investigation of thousands of incidents by Microsoft’s research teams.
Automatic attack disruption operates in 3 key stages:
- Detect malicious activity and establish high confidence
- Classification of scenarios and identification of assets controlled by the attacker
- Trigger automatic response actions using the Microsoft 365 Defender protection stack to contain the active attack
Detection is achieved by using our research-informed, AI-driven detection capabilities and refining them with specific signals, e.g. human operated ransomware, to establish a high level of confidence in accurately detecting ransomware spread and encryption activity. The XDR-level capability correlates insights across endpoints, identities, email and SaaS apps to establish high-fidelity alerts.
The second stage consists of further aggregation and automatic analysis of the malicious activities, such as product tampering, backup deletion, credential theft, mass lateral movement, and many more. The intent is to flag the assets that are responsible for the malicious activity. Microsoft 365 Defender unravels the chain of attacks by retracing the malicious activity on a device to its remote execution TTP.
Lastly, automatic response actions are triggered against entities identified as compromised. In the current public preview, the automatic attack disruption capabilities use two key response actions to stop in-progress attacks:
- Disable user: If onboarded to Microsoft Defender for Identity, we will automatically trigger a Suspend Account action on the user(s) delivering the attack. The action suspends the compromised user account in Active Directory and syncs this information to Azure AD.
- Device containment: For environments using Defender for Endpoint, devices will be automatically contained to prevent any onboarded device from communicating with the compromised machine.
To ensure that automatic actions don’t negatively impact the health of a network, Microsoft 365 Defender automatically tracks and refrains from containing network-critical assets and built client-side fail safe mechanisms into the containment lifecycle. In addition, any automatic actions can be easily undone to ensure the SOC stays in full control.
Work with automatic attack disruption
When automatic disruption takes effect, we want to ensure visibility of these automatic actions, that's why the Microsoft 365 Defender user experience now includes additional visual cues across the following experiences:
Incident queue
- A tag titled “Attack Disruption” next to affected incidents
Incident page
- A tag titled “Attack Disruption”.
- A yellow banner at the top of the page that highlights the automatic action taken.
- The current asset status is shown in the incident graph if an action is done on an asset, e.g., account disabled or device contained.
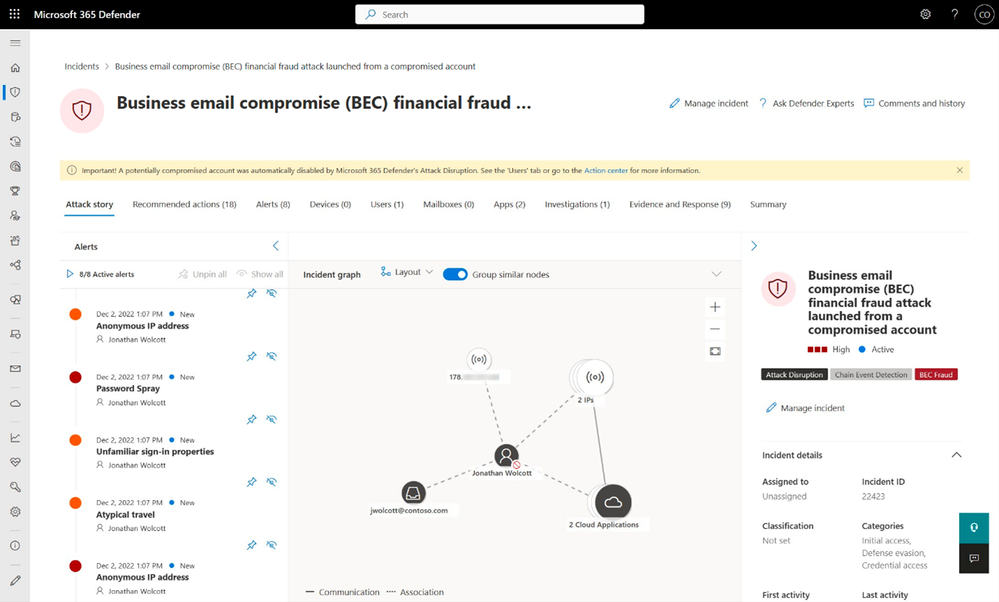
In addition, security teams can customize the configuration for automatic attack disruption and can easily revert any action from the Microsoft 365 Defender Portal, to ensure SOC teams have full control. Check out our documentation for more detail.
Microsoft 365 Defender is uniquely positioned to empower SOC teams to match the powerful techniques of adversaries and provide protection with the full context of an attack as the leading XDR natively spanning endpoint, identity, email and collaboration, and SaaS app security. Automatic attack disruption will change the game for SOC teams by limiting the impact of advanced attacks like BEC and human-operated ransomware through disruption at machine speed.
Get started
- Make sure your organization fulfills the Microsoft 365 Defender pre-requisites
- Connect Microsoft Defender for Cloud Apps to Microsoft 365.
- Deploy Microsoft Defender for Identity. You can start a free trial here.
Learn more
- Check out our documentation to learn more about Microsoft 365 Defender attack disruption prerequisites, available controls, and indications. to learn more about Microsoft 365 Defender attack disruption prerequisites, available controls, and indications.
- Watch the video from our announcement at Microsoft Ignite.
- From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud - Microsoft Security Blog
Published on:
Learn moreRelated posts
Microsoft Teams: Changes to Teams Events licensing
Starting early April 2026, advanced Teams events features will be included with Teams Enterprise licenses, supporting up to 3,000 attendees. N...
Microsoft 365 Copilot: Updates to PowerPoint on‑canvas features with Agent mode
PowerPoint will update Microsoft 365 Copilot with Agent mode for rewrite, translate, and speaker notes features, enabling chat-based interacti...
Retirement of SharePoint One-Time Passcode (SPO OTP) and transition to Microsoft Entra B2B guest accounts
SharePoint One-Time Passcode (SPO OTP) authentication will retire by August 2026, transitioning external sharing and authentication in OneDriv...
Microsoft 365 Copilot: Retirement of the Skills agent from Frontier
The Skills agent in Microsoft 365 Copilot will retire by the end of March 2026, with removal from new installations by March 16, 2026. Skills ...
Microsoft Teams: Channel Agent feature updates
Microsoft Teams is updating Channel Agent with customized welcome messages, user control over agent creation, improved scheduling, member addi...
Updates available for Microsoft 365 Apps for Current Channel
We’ve released updates to the following update channel for Microsoft 365 Apps: Current Channel When this will happen: We’ll be gra...
Microsoft Teams: delete meeting generated content in recap
Meeting organizers can now easily delete meeting generated content including recording, transcript, AI summary, and notes through the new dele...
SharePoint: Create SharePoint News Post from Copilot Pages
Once a Copilot Chat user has finished researching, creating, and collecting content in Copilot Pages, they can take it to a SharePoint News Po...
Microsoft Viva: Glint: AI-generated survey insights with Copilot Highlights
Copilot in Viva Glint now generates AI-powered summaries of employee survey results directly within Team Summary and Executive Summary reports...
Microsoft Teams: One-time email passcodes for external presenters in Teams events
One-time email passcodes provide an easy way for tenant administrators and event organizers to verify anonymous, external presenters invited t...