Investigate incidents more effectively with the new attack story view in Microsoft 365 Defender

One of the biggest efficiency drains for security operations center teams (SOC) is the constant switching of context – between different security tools or even between the various views within one solution when they’re looking for different types of information. These disconnected solutions and views cause SOC teams to lose valuable time while trying to manually piece together related signals.
Microsoft 365 Defender on the other hand correlates billions of signals across endpoints, cloud and on-prem identities, email, documents, and cloud apps and groups them into incidents – giving security teams a more effective way to investigate and remediate threats in a unified experience.
Today we’re excited to announce that we made the investigation experience even better with the introduction of attack story view in Microsoft 365 Defender - to help analysts stop breaches faster. In the new incident investigation experience in Microsoft 365 Defender, analysts can now easily navigate between affected assets or drill deep into the details of individual alerts, while always retaining the full context of the incident.
When you select an incident from the incident queue in Microsoft 365 Defender, the new attack story view is now the centerpiece of the investigation experience. It is a visual and interactive view of all affected resources, and it enables security analysts to understand the incident context at any point during their investigation. In addition, analysts can interact with the attack story view to determine next steps or take action from a dropdown with options.
Image 1 shows the new attack story view – it allows you to easily identify that in this case several users, files, an endpoint, an email account, as well as external domains are affected.
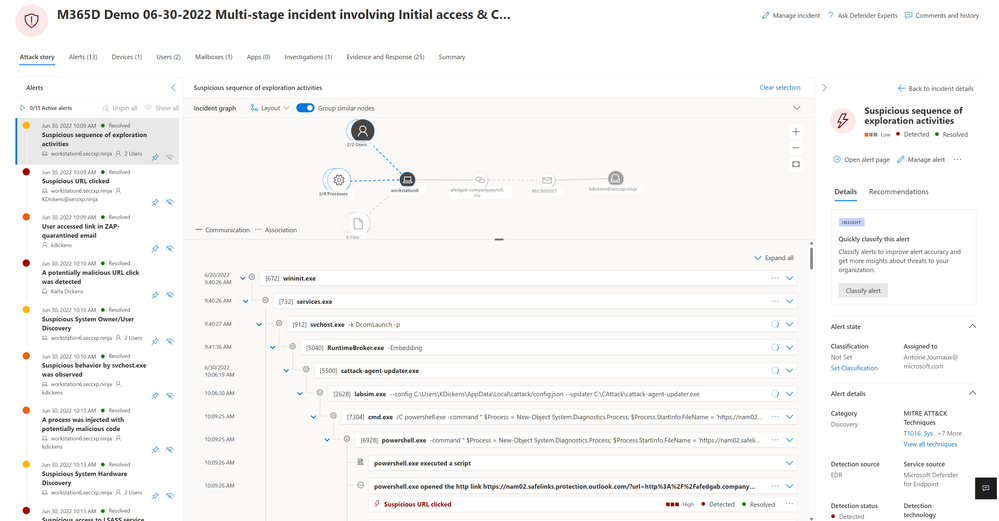
Image 2 shows you what interacting with the new incident page looks like and how the views dynamically adjust to your actions. On the left-hand side of image 2 you can see the list of alerts tied to this incident – as analysts select the different alerts, the attack story view automatically adjusts to zoom in on the relevant alert and the incident page adjusts to provide all relevant details tied to this alert.
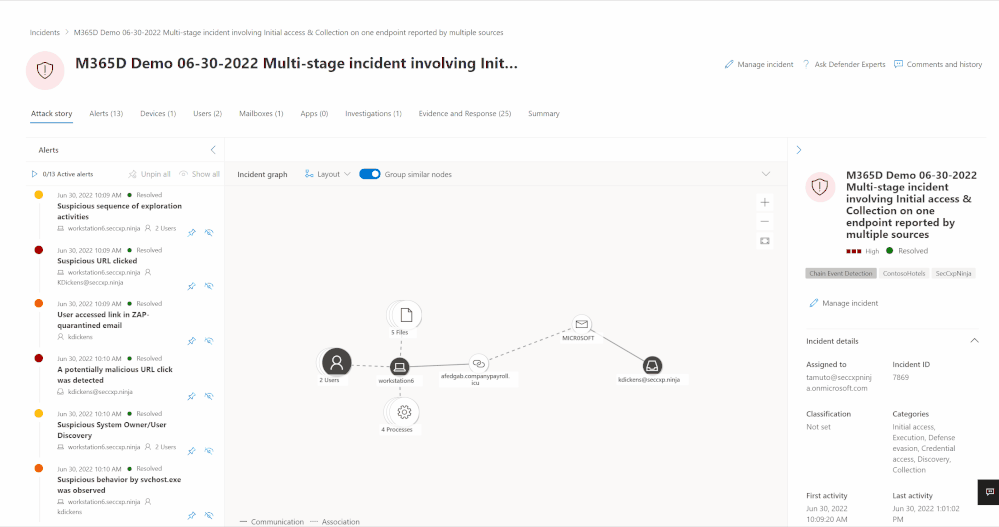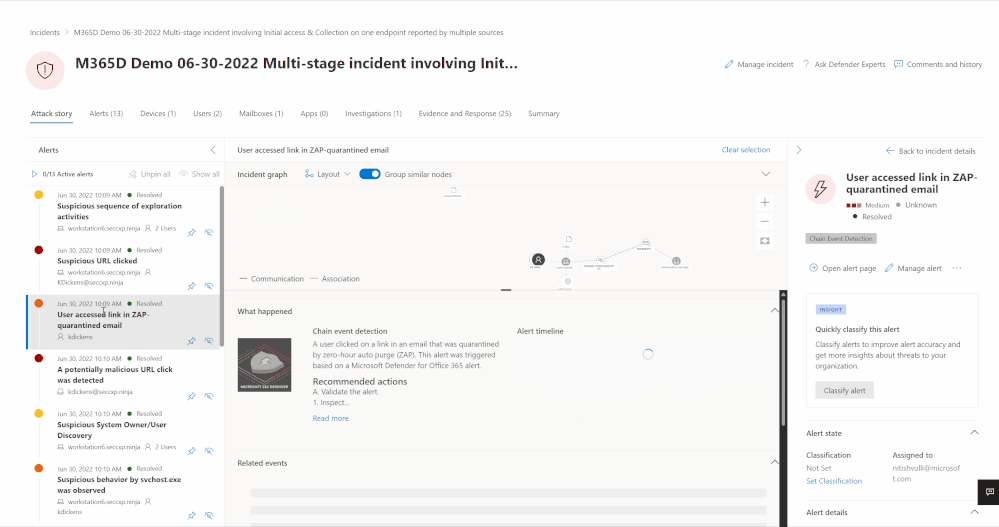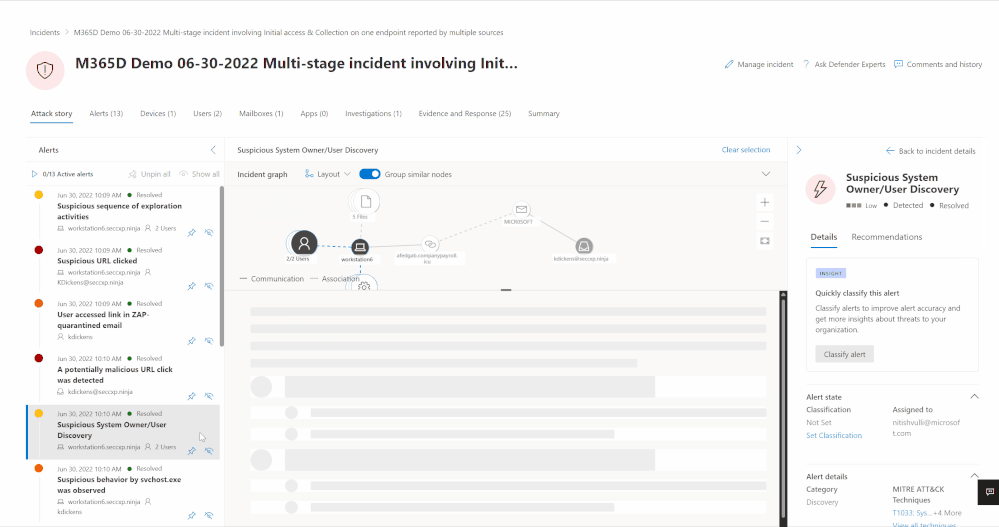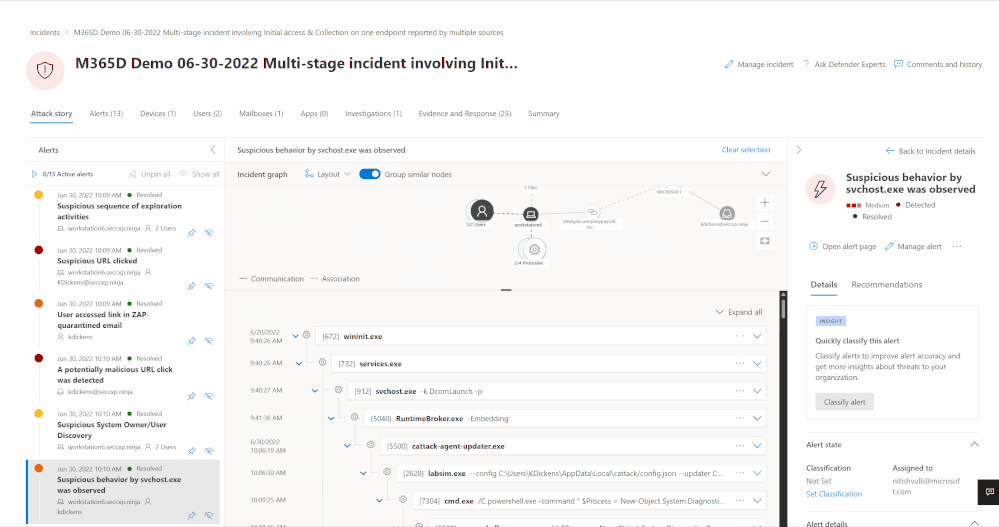
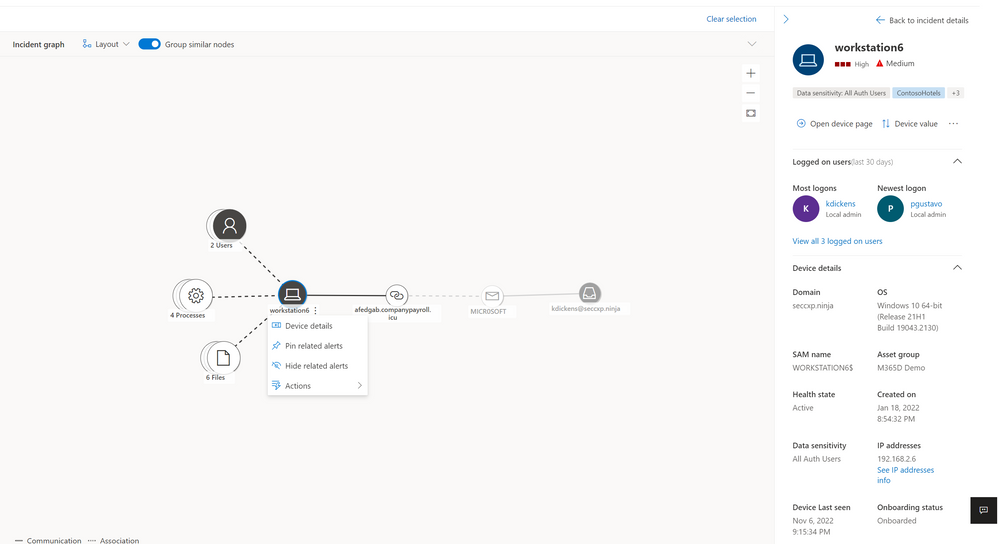
Alternatively, analysts can also engage directly with the graph to review the entity details by clicking on the relevant asset (image 3) and even select the action they want to take to further investigate or start remediation as shown in image 4.

The new attack story view changes the game for SOC teams – gone are the days of never-ending context switching and trying not to lose sight of the overall incident and affected assets. The interactive view will make the investigation and response more intuitive and most importantly - help respond to threats faster and limit the impact of an attack.
For more information, check out these resources:
- Get an overview of incident response with Microsoft 365 Defender
- Learn more about incident management with Microsoft 365 Defender
- Understand how to investigate incidents in Microsoft 365 Defender
Published on:
Learn moreRelated posts
Fetch message trace data via the Graph API
A quick look at the recently introduced /admin/exchange/tracing/messageTraces Graph API endpoint to fetch Exchange Online message trace detail...
Turn Chaos into Clarity: Build a Simple Risk & Issue Register with Teams + Copilot
In yesterday’s blog, I looked at how Microsoft Teams can become the central hub for managing your project, conversations, meetings, tasks, and...
SharePoint Embedded – Your first steps
As the SharePoint Embedded connector was released last night, I thought it would be useful to start a series of posts about SharePoint Embedde...
Still no good solution for cleaning deleted items via the Graph API
2026 is the year in which Microsoft plans to pull the plug on EWS, and before this happens, I’m taking some time to go over my code samp...
Microsoft Teams: Digital signage in Teams Rooms on Android
As with Teams Rooms on Windows, IT Admins can now set up Teams Rooms on Android to show dynamic signage content on the front-of-room display w...
New policy to add watermarks to content generated or altered by using AI in Microsoft 365
Microsoft 365 will offer a policy to add visual or audio watermarks to AI-generated or altered video and audio content, available via Cloud Po...
Microsoft Purview: Insider Risk Management – Quick policy to detect data theft from non-Microsoft 365 data sources
A new quick policy template in Microsoft Purview Insider Risk Management will help detect data theft from Microsoft Fabric and non-Microsoft 3...
Teams Integrates Viva Engage Communities
A new integration with Viva Engage is available for Teams. The integration adds communities to the Teams navigation bar. It’s kind of odd when...
Using Microsoft Teams + Copilot for Project Management
When people think about project management, they often picture complex tools, rigid templates, and admin overhead that few people enjoy. In re...
Microsoft 365 & Power Platform Community Call – January 22nd, 2026 – Screenshot Summary
Call Highlights SharePoint Quicklinks: Primary PnP Website: https://aka.ms/m365pnp Documentation & Guidance SharePoint Dev Videos Issues...