Latest innovations in Azure confidential computing
Today we are pleased to announce two major milestones in the Azure confidential computing portfolio: the general availability of Azure confidential ledger and general availability of the DCasv5 and ECasv5-series confidential VMs featuring the third generation AMD EPYC™ processors with Secure Encrypted Virtualization Secure Nested Paging (SEV-SNP).
Azure confidential ledger is a new and highly secure service for managing sensitive data records and it runs exclusively on hardware-backed secure enclaves. Azure confidential ledger offers unique data integrity advantages, including immutability, tamper-proofing, and append-only operations. These features, which ensure that all records are kept intact, are ideal when critical metadata records must not be modified, such as for regulatory compliance and archival purposes.
The Azure DCasv5 and ECasv5 confidential VM series provide a hardware-based Trusted Execution Environment (TEE) that features AMD SEV-SNP security capabilities, which harden guest protections to deny the hypervisor and other host management code access to VM memory and state, and that is designed to protect against operator access. Customers can easily migrate their legacy workloads from on-premises environments to the cloud with minimal performance impact and without code changes by leveraging the new AMD-based confidential VMs. These confidential VMs also support added protections such as full OS disk encryption and integrations with Azure Managed HSM (Hardware Security Module) and Azure Key Vault. Customers can also use the free Microsoft Azure Attestation (MAA) service to verify the operating environment, rooted down to the AMD hardware.
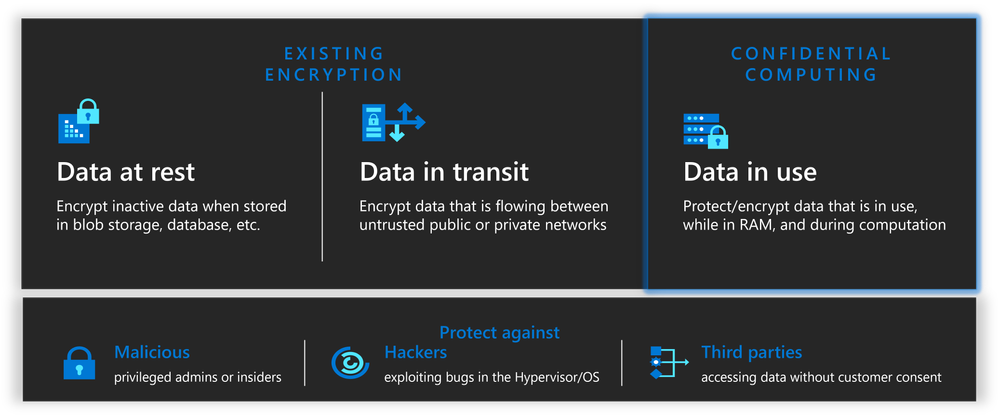
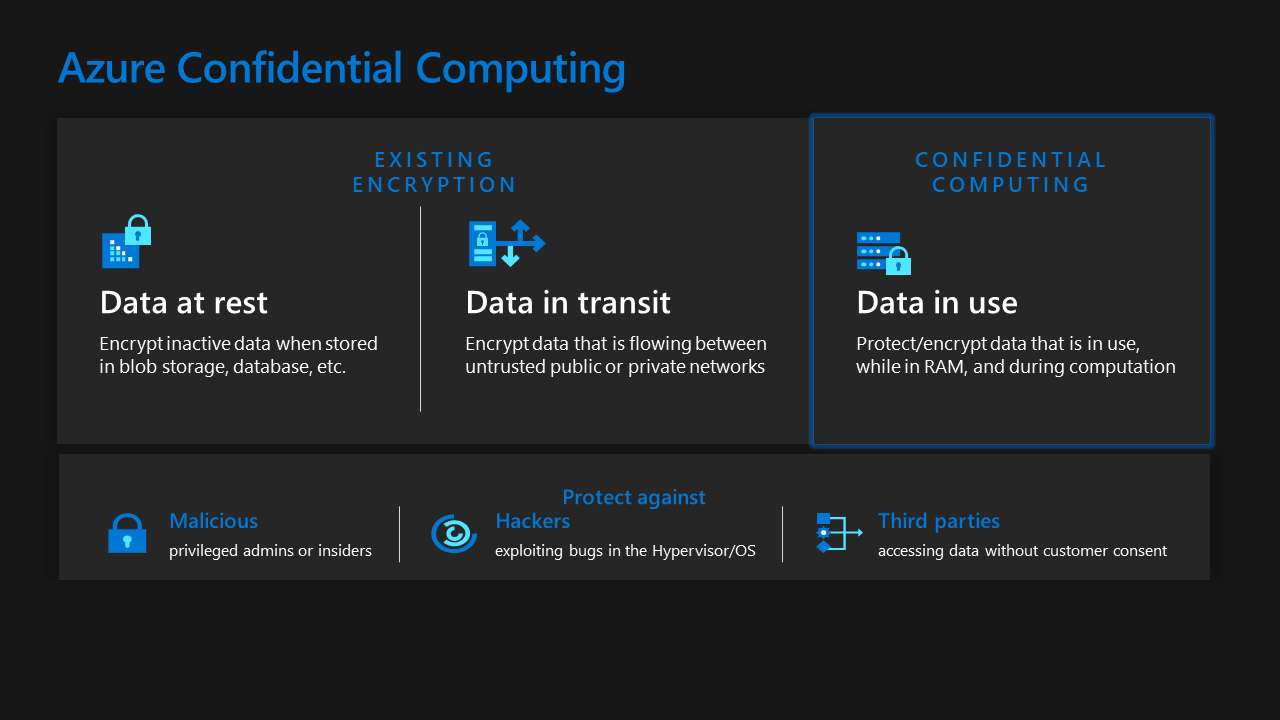
As a founding member of the Confidential Computing Consortium (CCC), Microsoft is leading the way to help software developers accelerate their adoption of TEE technologies and standards. Combined with data-at-rest encryption and data-in-transit encryption, confidential computing helps customers have verifiable assurance that their workloads (both data and code) are protected from the time they are created until the time they are destroyed.
Azure confidential computing portfolio
Today, Azure provides the broadest set of confidential offerings for virtual machines (VMs), containers and applications across CPUs and GPUs. Azure has been working very closely with our hardware vendors from the CCC such as AMD, Intel, and Nvidia, and has been the cloud service provider launch partner for all three of them. In addition, Azure provides a strong ecosystem of partners who can help customers make their existing or new solutions confidential.
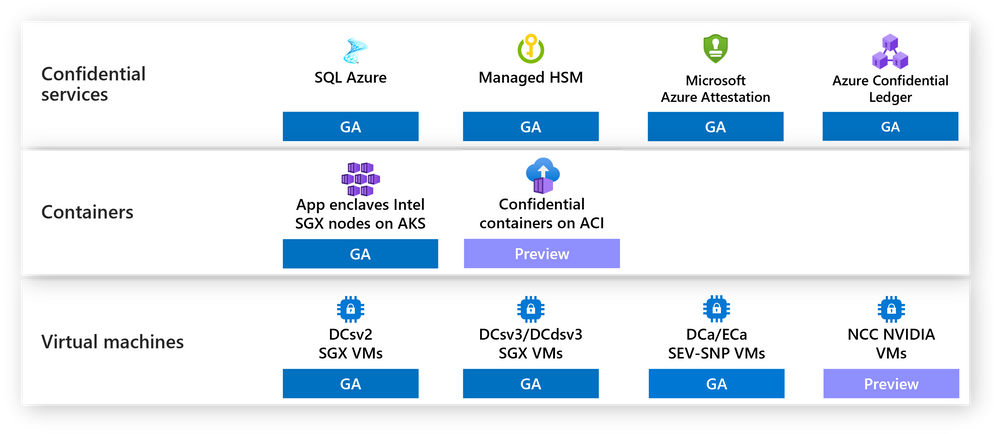
In addition to the general availability of Azure confidential ledger and AMD SEV-SNP based confidential VMs, announced today, the Azure confidential computing portfolio also includes the Azure services outlined below.
Virtual Machines
Virtual machines with application enclaves on Intel SGX
Intel SGX helps protect data in use by giving developers the flexibility to isolate their applications into trusted and untrusted regions in memory. Azure was the first major Cloud Service Provider (CSP) to make generally available a virtualized environment for Intel SGX Virtual Machines (VMs) with DCsv2 VM sizes. Earlier this year, we extended our partnership with Intel to release the next generation DCsv3 and DCdsv3 VMs on 3rd generation Intel Xeon Scalable processors, which increased Enclave Page Cache (EPC) memory by 1500x, RAM by 12x, and CPU cores by 6x enabling the deployment of larger workloads while maintaining data confidentiality. Customers can provision DCsv2 or DCsv3 VMs to create applications that run inside enclaves using the Open Enclave SDK, CCF SDK or solutions from a growing ecosystem of partners.
Confidential virtual machines on NVIDIA GPUs
Many industries such as healthcare, finance, transportation, and retail are going through a major AI-led disruption. The exponential growth of datasets has resulted in growing scrutiny of how data is exposed—both from a consumer data privacy and compliance perspective. Earlier this year, we partnered with NVIDIA to combine the power of GPU-accelerated computing with confidential computing for state-of-the-art AI workloads. To request access to the limited preview, please sign up here.
Containers
Confidential node pools on AKS with Intel SGX VMs
Azure Kubernetes Service (AKS) supports adding Intel SGX confidential computing VM nodes as agent pools in a cluster. These nodes allow you to run sensitive workloads within a hardware-based Trusted Execution Environment (TEE).
Confidential containers on Azure Container Instances (ACI)
Confidential containers on ACI are a first to market fully managed serverless offering allowing customers to easily lift-and-shift Linux containers to Azure in a hardware-based trusted execution environment with AMD SEV-SNP technology. With confidential containers on ACI, customers can easily run existing containerized workloads in a verifiable hardware-based Trusted Execution Environment (TEE). To get access to the limited preview, please sign up here.
Services
Managed HSM confidential key management
Azure Key Vault Managed HSM (Hardware Security Module) is a fully managed, highly available, single-tenant, standards-compliant cloud service that enables you to safeguard cryptographic keys for your cloud applications, using FIPS 140-2 Level 3 validated HSMs. The Managed HSM Service runs inside a TEE built on Intel SGX and offers enhanced protection from internal and external attackers through hardware isolation that protects data in use.
Azure SQL always encrypted with secure enclaves
Always Encrypted with secure enclaves expands confidential computing capabilities of Always Encrypted by enabling in-place encryption and richer confidential queries. Always Encrypted with secure enclaves allows computations on plaintext data inside a secure enclave on the server side. There's no way to view any data or code inside the enclave from the outside, even with a debugger. These properties make the secure enclave a trusted execution environment that can safely access cryptographic keys and sensitive data in plaintext, without compromising data confidentiality.
Azure SQL Database Ledger
Azure SQL Database ledger is a confidential tamper-proof solution for your databases that provides cryptographic proof of your database’s integrity. Using a blockchain data structure implemented as system tables in your database, the ledger feature ensures that any transaction which modifies relational data in your database can be tracked, and any potential tampering detected and easily remediated. Ledger is a feature of Azure SQL Database, meaning there is no additional cost to add tamper-evidence capabilities. You don’t have to migrate data from your existing SQL databases to add tamper-evidence capabilities and no changes are needed to your applications as ledger is an extension of existing SQL table functionality.
Microsoft Cloud for Sovereignty
Governments and public sector customers around the world are looking to accelerate their digital transformation, creating opportunities for social and economic growth, and enhancing citizen services. Microsoft Cloud for Sovereignty is a new solution that will enable public sector customers to build and digitally transform workloads in the Microsoft Cloud while meeting their compliance, security, and policy requirements. With Microsoft Cloud for Sovereignty, we will deliver capabilities that will provide customers additional layers to protect and encrypt sensitive data. The portfolio of confidential VMs, containers, and services will be available for Microsoft Cloud for Sovereignty to ensure protection of data is use. More details on Microsoft Cloud for Sovereignty are being announced here and here.
Azure is the world’s computer from cloud to edge
Customers of all sizes, across all industries, want to innovate, build, and securely operate their applications across multi-cloud, on-premises, and edge. Just as HTTPS has become pervasive for protecting data during internet web browsing, we believe that confidential computing will be a necessary ingredient for all computing infrastructure.
We will partner with hardware vendors and innovate within Microsoft to bring the highest levels of data security and privacy to our customers. In our journey to become the world’s leading confidential cloud, we will drive confidential computing innovations horizontally across our Azure infrastructure and vertically through all the Microsoft services that run on Azure.
Learn more about Azure confidential computing.
Published on:
Learn moreRelated posts
Azure Developer CLI (azd): One command to swap Azure App Service slots
The new azd appservice swap command makes deployment slot swaps fast and intuitive. The post Azure Developer CLI (azd): One command to swap Az...