Secure a web app architecture with Azure confidential computing

In this post, we’ll show you how to build a Personal Identifiable Information (PII) - protecting web application architecture using Azure confidential computing (ACC). ACC completes your traditional cloud privacy with protections for data in use based on state-of-the-art hardware available in Azure today.
Architecture
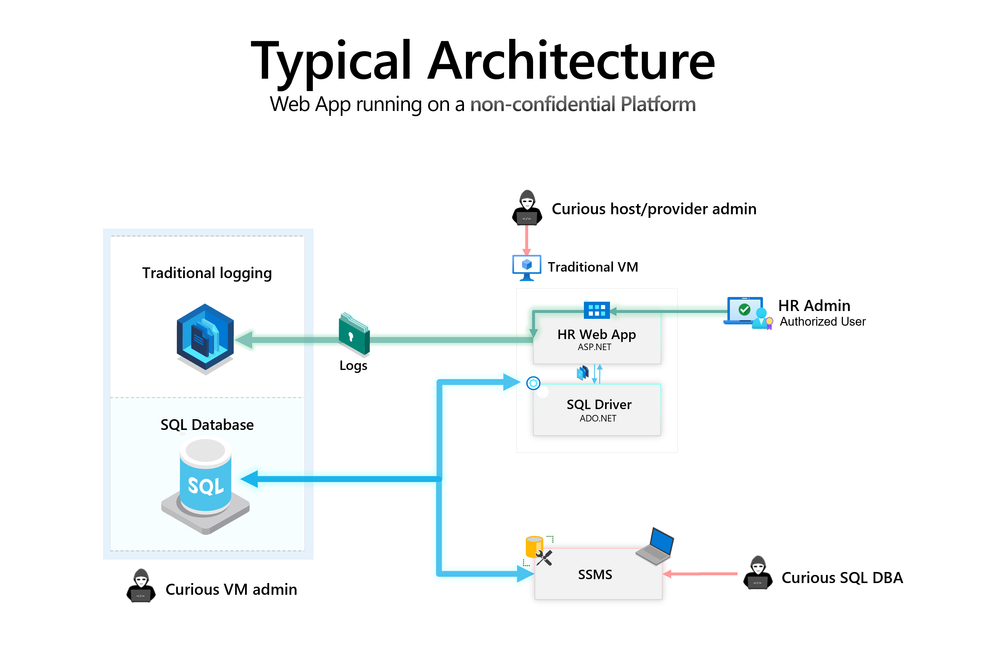
The diagram below showcases a typical architecture pattern for hosting a web application (e.g. On-Premises or Cloud Platform):
Typical architecture for a web application
The problem with this typical approach is that malicious actors could gain access to, as well as manipulate, sensitive data running on this architecture. For example:
- Curious SQL DBA - with db_owner access can access sensitive tables, as well as leverage SQL Server Extended Events Sessions to intercept query predicates.
- Curious VM admin - with access to application logs can manipulate sensitive application logs, e.g. to erase a subset of the history.
- Curious host/provider admin - with access to the underlying Hypervisor can access the Virtual Machines.
Azure confidential computing enhances the security posture of your applications by protecting data and code when in use, that is when running and being processed in memory. This additional level of protection elevates the existing security posture in Azure by running application in hardware-encrypted trusted execution environments.
For an overview of what Azure confidential computing offers, please refer to this article: Navigating confidential computing across Azure.
Going Confidential
Next, we'll show you how to enhance your web application privacy with Azure confidential computing.
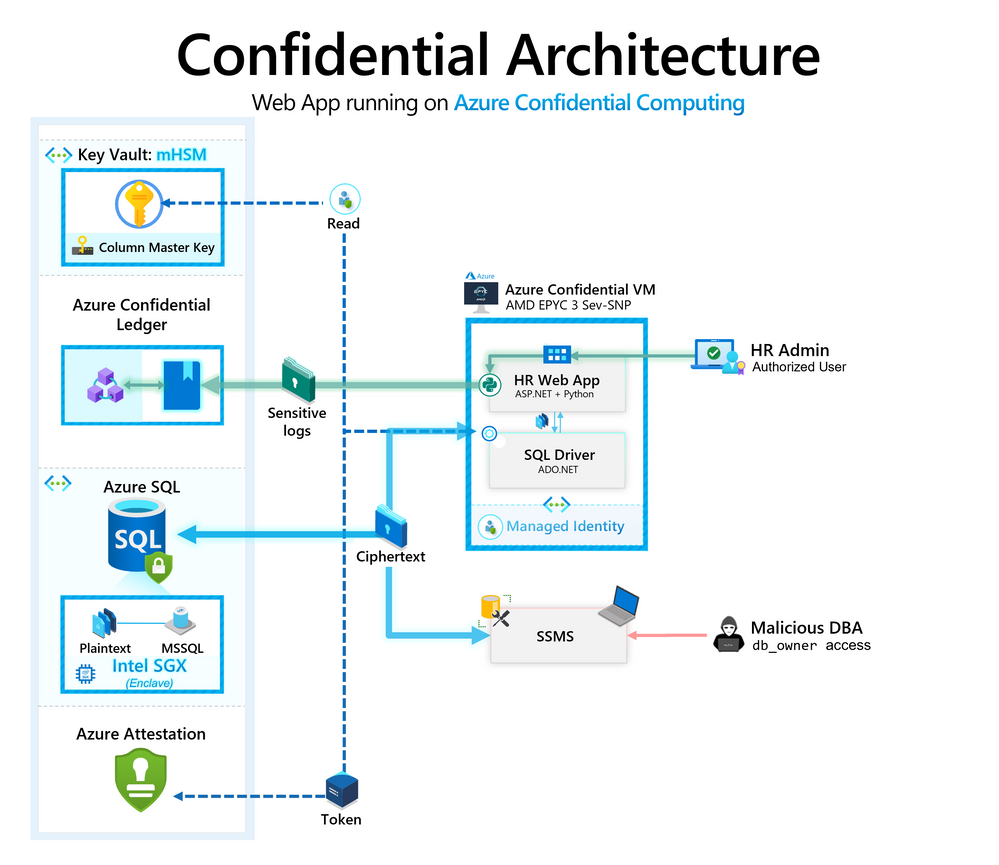
Confidential architecture leveraging Azure confidential computing services
Core components:
- Sensitive Data - Azure SQL DB - Always Encrypted with secure enclaves: For hosting a confidential database - with sensitive columns that are encrypted via CMK (Column Master Key).
- Sensitive Data Encryption Keys - Azure Key Vault - mHSM: A FIPS 140-2 Level 3 validated HSM - used in this case for storing the Always Encrypted Column Master Key - or CMK for the sensitive database.
- Sensitive Application Logic - Azure Confidential VM - with AMD EPYC 3 Sev-SNP: For hosting a Web app that queries the sensitive database within Azure SQL DB, and persists sensitive logs generated on the Web app (e.g. query history).
(Confidential VM AMD EPYC 3 Sev-SNP is not yet generally available at time of writing; sign-up for preview here). - Sensitive Application logs - Azure Confidential Ledger: As an append-only, immutable ledger for hosting sensitive logs.
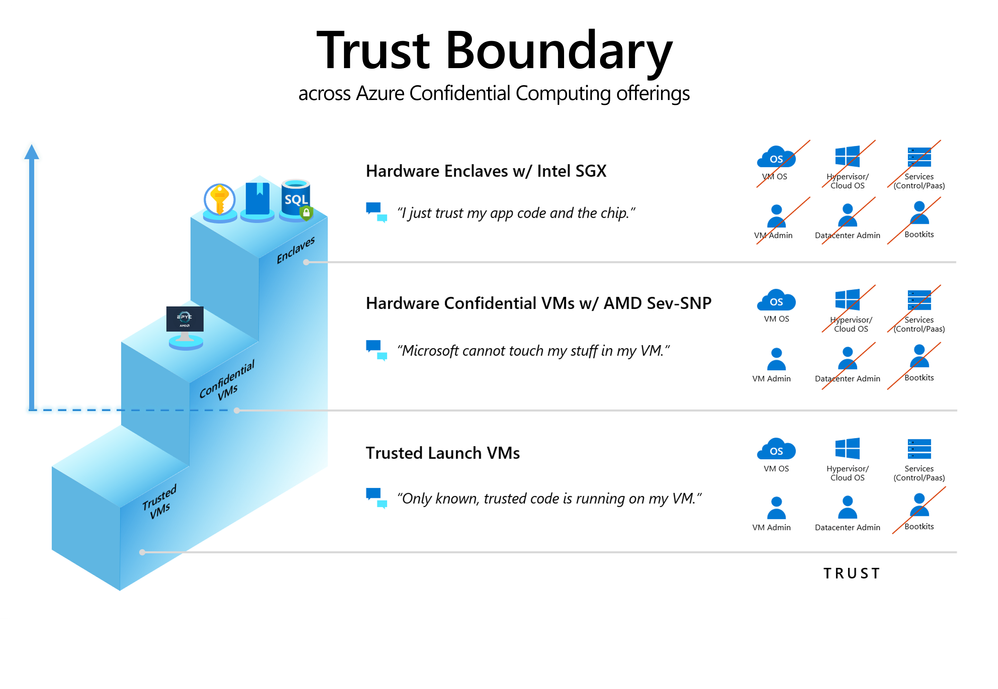
All components of this architecture, including Sensitive Data, Sensitive Data Encryption Keys, Sensitive Application Logic and Sensitive Application logs - are hosted at or above the blue dotted line highlighted below:
Trust boundary across Azure confidential computing services.
To transform an existing (or net-new) application to leverage confidentiality via ACC – the following activities can be easily accomplished for each of the 3 tiers of the application: Data, Code and Logs:
- Sensitive Data: For an existing database, to migrate the data to Azure SQL DB – Always Encrypted with secure enclaves, we can leverage any of the migration techniques available with Azure SQL DB today. For a net new database, we can leverage several techniques to hydrate our database – as illustrated in this repository via T-SQL.
- Sensitive Application Code: Azure Confidential VM with AMD EPYC 3 Sev-SNP allows us to lift-and-shift existing application logic - meaning there are no code changes expected of our application to take advantage of the elevated confidentiality. Any web app framework (see demo below for a simple ASP.NET example) can continue to function as is.
- Sensitive Application Logs: To programmatically send sensitive application logs to Azure Confidential Ledger, we can use any of the SDKs available. In the demo below, we use the Python SDK from PyPi for demonstration – at the time of writing Java and .NET SDK are available as well.
Demonstration
A live demonstration of this architecture pattern is showcased in the short demo video below. In this demonstration, we leverage a Confidential VM to emphasize one core point - no code changes are required of an existing application (in our case, an ASP.NET Web App) to run on an AMD Sev-SNP enabled Virtual Machine on Azure:
Demo Video from Build – starts at 27:34
Get Started
Instructions on how to publish this app are described on the author's GitHub repo.
Published on:
Learn moreRelated posts
Microsoft Entra ID Governance: Azure subscription required to continue using guest governance features
Starting January 30, 2026, Microsoft Entra ID Governance requires tenants to link an Azure subscription to use guest governance features. With...
Azure Developer CLI (azd) – January 2026: Configuration & Performance
This post announces the January 2026 release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) – January 2026: Conf...
Azure SDK Release (January 2026)
Azure SDK releases every month. In this post, you'll find this month's highlights and release notes. The post Azure SDK Release (January 2026)...
Azure Cosmos DB TV Recap – From Burger to Bots – Agentic Apps with Cosmos DB and LangChain.js | Ep. 111
In Episode 111 of Azure Cosmos DB TV, host Mark Brown is joined by Yohan Lasorsa to explore how developers can build agent-powered application...
Accelerate Your Cosmos DB Infrastructure with GitHub Copilot CLI and Azure Cosmos DB Agent Kit
Modern infrastructure work is increasingly agent driven, but only if your AI actually understands the platform you’re deploying. This guide sh...
Accelerate Your Cosmos DB Infrastructure with GitHub Copilot CLI and Azure Cosmos DB Agent Kit
Modern infrastructure work is increasingly agent driven, but only if your AI actually understands the platform you’re deploying. This guide sh...
SharePoint: Migrate the Maps web part to Azure Maps
The SharePoint Maps web part will migrate from Bing Maps to Azure Maps starting March 2026, completing by mid-April. Key changes include renam...
Microsoft Azure Maia 200: Scott Guthrie EVP
Azure Cosmos DB TV Recap: Supercharging AI Agents with the Azure Cosmos DB MCP Toolkit (Ep. 110)
In Episode 110 of Azure Cosmos DB TV, host Mark Brown is joined by Sajeetharan Sinnathurai to explore how the Azure Cosmos DB MCP Toolkit is c...