enclaive's THE BASE: Developing Confidential Cloud Applications with Ease on Azure DCsv2/DCsv3-serie
The Rise of the Confidential Compute Cloud
Confidential Compute (CC) is a powerful new paradigm, embarking on the cloud computing space. It won’t take much time and a cloud will naturally transform into a confidential one. There are several strong arguments. All of them are centered around creating business value and growth in data-driven sovereign societies. The reason is Confidential Cloud Computing raises the bar in securely storing and most notably processing data in use. In fact, Confidential Cloud Computing is an important cloud enabling technology to base data-driven SaaS and PaaS applications on solid foundations.
Enclaive’s Confidential Container Stack “The Base” for Azure’s DCs-Series
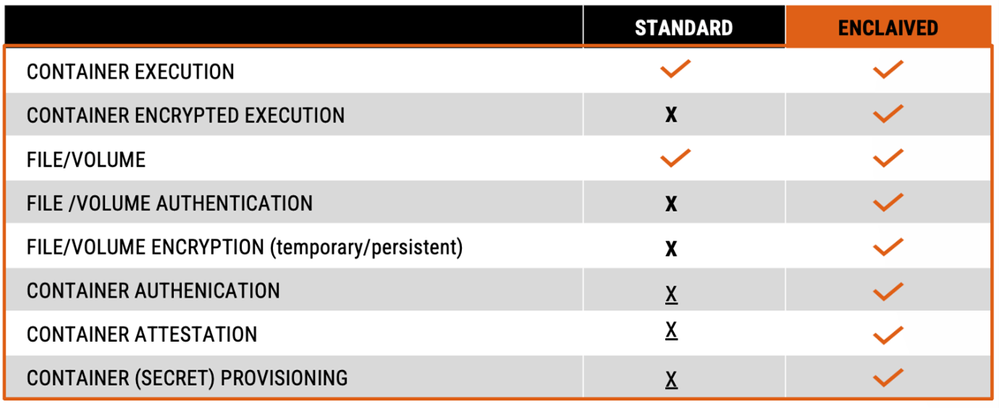
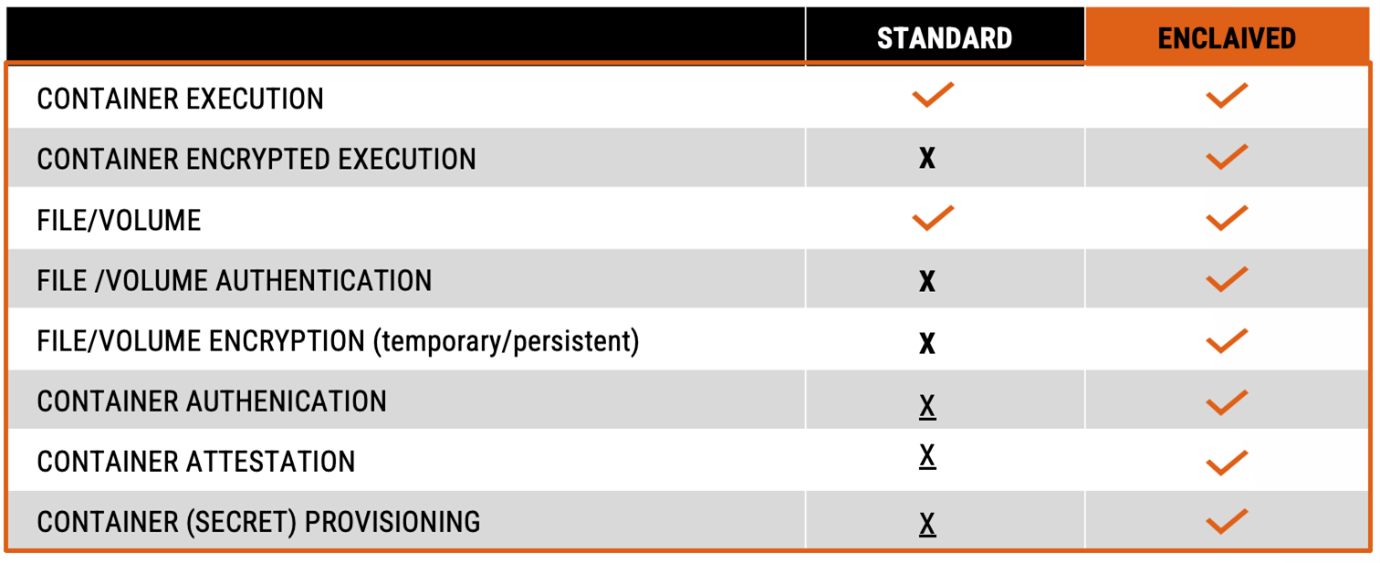
While the Azure team did some wonderful work to provide CC-ready compute infrastructures, the missing building blocks are CC-ready applications. In the last decade, container technologies have established and simplified the deployment, integration, and management of software in the cloud. In fact, they are the cornerstone in the development of cloud applications. Confidential Compute Containers are the natural evolution. They are compatible with DevOps best practices like Docker, Kubernetes and OpenShift. Leveraging confidential compute, they added some important functionalities, including:
- Fully in-memory encrypted execution to conceal data and code
- Encrypted and authenticated (shared) volume/files to persistently store data
- Container authentication to identify the author and application code
- Container attestation to remotely verify the container identity
- Container (secret) provisioning to update the volume with files, environment variables or secrets
To ease and simplify the development of CC applications, and save developer time and costs, enclaive has developed an arsenal of confidential compute containers covering what we call “The Base” stack. The Base includes prominent CC-versions of databases like MariaDB, MongoDB, ArangoDB, or Redis; backend technologies to run Python, Java, Ruby, Rust, JavaScript and PHP applications; load-balancer NGINX and IoT-broker Mosquitto; and some applications like the content management system WordPress and Web traffic analysis tool Umami.
Putting it all together, The Base is a solid collection of open-source applications to build, test and deploy a plethora of cloud applications.
Getting Started: 3steps to a Confidential Cloud
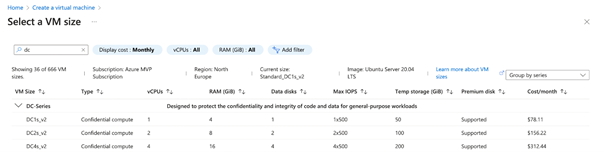
Enclaive’s “The Base” Containers are compatible with DevOps best practices like Docker, Kubernetes, and OpenShift. All they require to be executed is a VM supporting Intel SGX technology (DCsv2/DCsv3-series).
Quickstart: Available on Azure Marketplace
The Base is also available on the Azure marketplace
Build via GitHub
To run a confidential compute base container, set up a VM and pull the image:
1. Configure an Azure DCs-series VM
Note, in the configuration all drivers are upstreamed.
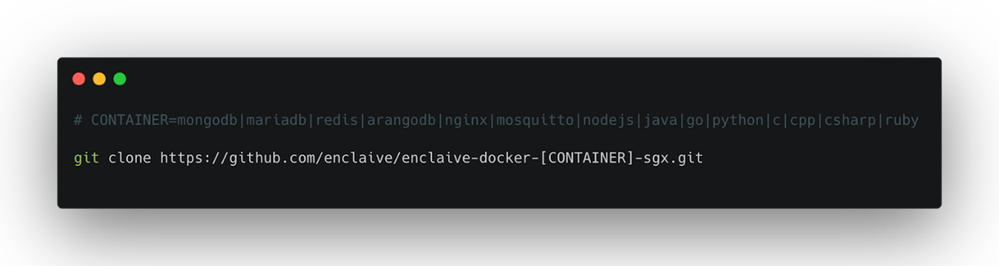
2. Pull the confidential container from enclaive’s github repository
3. Start (building) the container
Use Case: Data-in-Use Encryption in MariaDB
Databases play a key role in cloud applications today. So, the protection of data is crucial for any business. Data-at-rest and data-in-transit are concepts that have been introduced to protect databases. One of the longest open problems was protecting databases while in use. In contrast to data-at-rest encryption, the data is protected in memory during execution. That means not only the data file system is encrypted, but also the query processing it. Effectively the database runs in a black box and acts like an oracle: one can challenge the oracle; however, one learns nothing about the data within the oracle.
With enclaive’s confidential container technology data-in-use protection comes from the container packaging. Below a demo showcasing what happens when one inserts a SQL query into a non-confidential and confidential MariaDB container. The first allows reading the database content after a memory dump while data can only be seen encrypted with the confidential container version.
Youtube Link: https://youtu.be/PI2PosrdrCk
Use Case: Data-in-Use Integrity Protection of protected Volume/Files against Container Escapes
Container escape is a security risk in which malicious players can leverage a containerized application’s vulnerabilities to breach its isolation boundary, gaining access to the host system’s resources. Once an attacker accesses the host system, they can escalate their privilege to access other containers running in the machine or run harmful code on the host. Container escape and privilege escalation attacks can be devastating — costing you sensitive information from files or databases or leading to entire applications going down.
Confidential Containers enable a new kind of volume to mount a protected file system. A protected volume/file system can either be confidential and/or authenticated. This way, one may protect against attempts to extract sensitive information from files or their modification. In a container escape, for example, the attacker may attempt to alter configuration files, extract secrets, and environment variables. Below is a demo showcasing what happens when one attempts to modify a file in a non-confidential and confidential container. The first allows to replace the content from a file while reading. The enclaive protected file system detects the modification.
YouTube Link: https://youtu.be/RnZjhZinOE8
Learn More
Enclaive’s mission is to ease the development of confidential compute environments and help developers, devops, and businesses to deploy in . Next to the open-sourced “The Base” community containers enclaive offers and maintains a larger portfolio of Confidential Compute enterprise ready containers and services, reducing time and costs to leverage a confidential cloud.
For more information , check out:
- Enclaive website
- Azure Marketplace
- GitHub
- Docker Hub
- Youtube: Confidential Containers in Actions
- Azure Webinar: Ask the Experts
- Azure Webinar: Enabling Cookieless eCommerce: Confidential WordPress-SGX
Get in touch via [email protected] to explore how enclaive technology helps you. Join us on Discord to become part of the growing open-source enclaive community.
Trademarks
The respective trademarks mentioned in the offering are owned by the respective companies, and use of them does not imply any affiliation or endorsement.
Published on:
Learn moreRelated posts
What runs ChatGPT, Sora, DeepSeek & Llama on Azure? (feat. Mark Russinovich)
Build and run your AI apps and agents at scale with Azure. Orchestrate multi-agent apps and high-scale inference solutions using open-source a...
Azure Cosmos DB TV – Everything New in Azure Cosmos DB from Microsoft Build 2025
Microsoft Build 2025 brought major innovations to Azure Cosmos DB, and in Episode 105 of Azure Cosmos DB TV, Principal Program Manager Mark Br...
Azure DevOps with GitHub Repositories – Your path to Agentic AI
GitHub Copilot has evolved beyond a coding assistant in the IDE into an agentic teammate – providing actionable feedback on pull requests, fix...
Power Platform Data Export: Track Cloud Flow Usage with Azure Application Insights
In my previous article Power Platform Data Export: Track Power Apps Usage with Azure Data Lake, I explained how to use the Data Export feature...
Announcing General Availability of JavaScript SDK v4 for Azure Cosmos DB
We’re excited to launch version 4 of the Azure Cosmos DB JavaScript SDK! This update delivers major improvements that make it easier and faste...
Confluent Cloud Releases Managed V2 Kafka Connector for Azure Cosmos DB
This article was co-authored by Sudhindra Sheshadrivasan, Staff Product Manager at Confluent. We’re excited to announce the General Availabili...
Now in Public Preview: Azure Functions Trigger for Azure Cosmos DB for MongoDB vCore
The Azure Cosmos DB trigger for Azure Functions is now in public preview—available for C# Azure Functions using Azure Cosmos DB for MongoDB vC...
Now Available: Migrate from RU to vCore for Azure Cosmos DB for MongoDB via Azure Portal
We are thrilled to introduce a cost-effective, simple, and efficient solution for migrating from RU-based Azure Cosmos DB for MongoDB to vCore...
Generally Available: Seamless Migration from Serverless to Provisioned Throughput in Azure Cosmos DB
We are excited to announce the general availability (GA) of a highly requested capability in Azure Cosmos DB: the ability to migrate from serv...