Try new Azure confidential ledger features, including an Azure Blob Storage Marketplace application

To support customers in regulated industries and compliance scenarios who asked about higher integrity protection of storage blobs, the Azure confidential ledger team has launched a preview of a managed Marketplace application that will further protect data: Blob Storage Digests Backed by Confidential Ledger (Preview).
Data signatures from blob can be harvested and stored in a confidential ledger for tamper protection. At a later point in time and to demonstrate tamper proofness for compliance and auditing purposes, signatures can be recalculated and validated against the signature in Azure confidential ledger. To express your interest, to learn how to get started.
Customers needing confidentiality guarantees in key-value store can continue utilizing Azure confidential ledger directly and can leverage the integration between Azure SQL Database ledger with digest stores in Azure confidential ledger for continuing to protect their relational data.
The Azure confidential ledger team has also launched new features to enhance product and auditing experience:
- The Azure confidential ledger Portal experience has been improved with a new Ledger Explorer feature that allows observing transactions and validating the cryptographic proofs of ledger transactions.
- The multi-admin delete (upcoming) feature will allow deleting ledgers only with approval from multiple administrators, compared to a single administrator requested delete today.
These features will be available beginning December 1, 2023.
Quick Glance of the new Marketplace App: Blob Storage Digests Backed by Confidential Ledger (Preview)
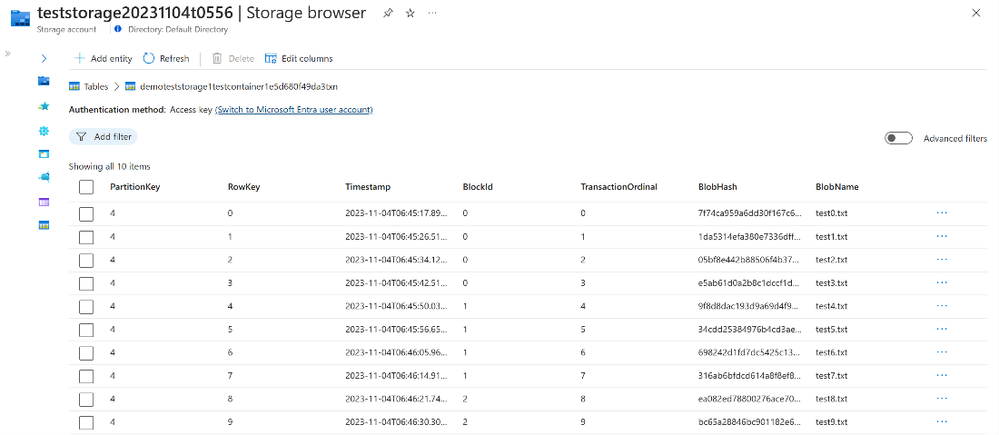
Step 1: When a new blob gets created, the transaction table will be populated with a new entry
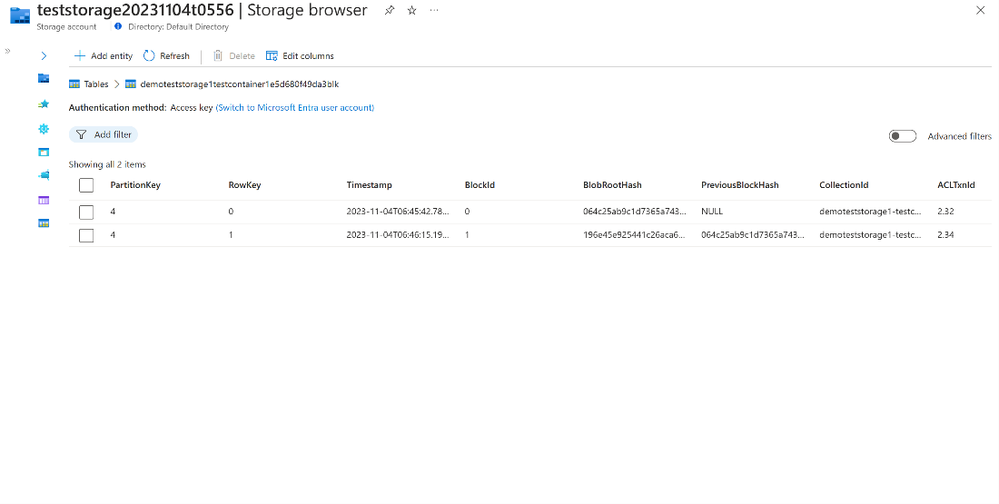
Step 2: When enough blob records have been created, a digest will be calculated and stored in to Azure Confidential Ledger. An entry will be created within the block table and contain the Azure Confidential Ledger Transaction ID.
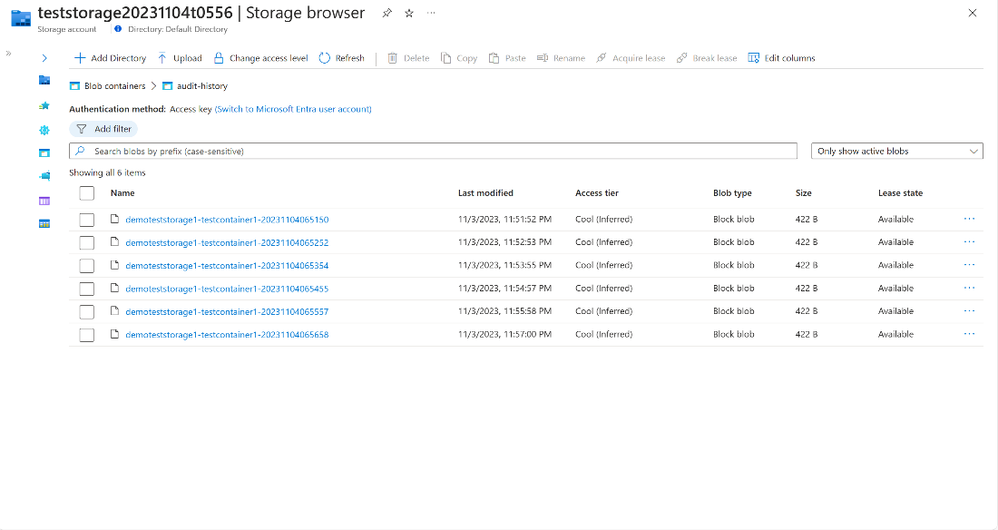
Step 3: When it comes time to performing an audit, a history of audit records can be viewed for every blob storage container
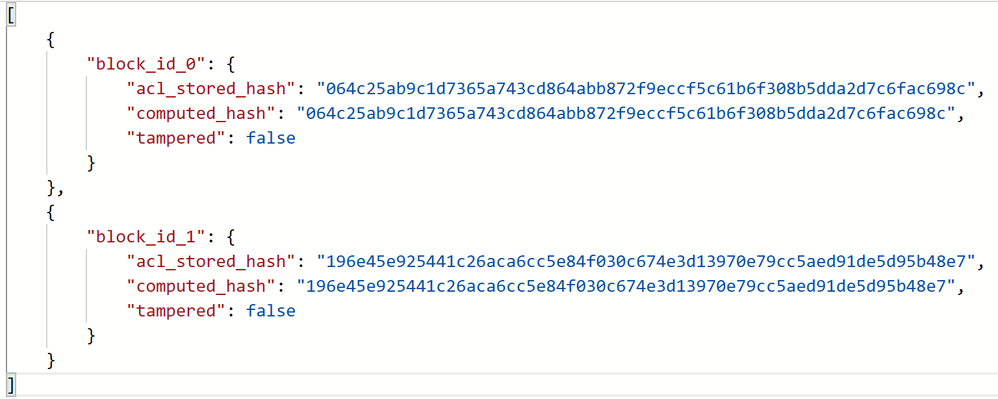
Step 4: The audit record will verify transactions and demonstrate the integrity protection status by comparing the digest hash stored in Azure Confidential Ledger against re-calculated digest hash
Getting Started & Resources
For getting started with Azure confidential ledger, read our documentation and past blog posts:
- ACL Get Started
- ACL Documentation
- BeekeeperAI Case Study
- ACL Hardware Supply Chain Post
- ACL Securing Compliance Data Post
Published on:
Learn moreRelated posts
Azure Developer CLI (azd): One command to swap Azure App Service slots
The new azd appservice swap command makes deployment slot swaps fast and intuitive. The post Azure Developer CLI (azd): One command to swap Az...