Azure Backup: Multi-user authorization for Recovery Services vaults is now generally available

Backup is often considered to be the last line of defense. Hence, it must be ensured that the backup data is always protected from any malicious actions. Multi-user authorization (MUA) for Azure Backup Recovery Services vaults can help you secure your backup data better by adding an additional layer of protection to critical operations on your Recovery Services vaults. A critical operation here can be described as an operation that could lead to loss of backup data, and hence, its misuse must be prevented.
Concepts
For MUA, Azure Backup uses an Azure resource called the Resource Guard to ensure critical operations are performed only with applicable authorization. Therefore, to perform a critical operation successfully, you must have sufficient permissions on the associated Resource Guard as well. The following critical operations can be protected using MUA for Backup.
|
Operation |
Mandatory/Optional |
|
Disable soft delete |
Mandatory |
|
Disable MUA protection |
Mandatory |
|
Modify backup policy (reduced retention) |
Optional: Can be excluded |
|
Modify protection (reduced retention) |
Optional: Can be excluded |
|
Stop protection with delete data |
Optional: Can be excluded |
|
Change MARS security PIN |
Optional: Can be excluded |
MUA for Backup revolves around using 2 personas with clearly defined responsibilities in an organization to ensure no operations can be performed by an individual alone. Let's consider the following personas:
- Backup admin: Owner of the Recovery Services vault and performs management operations on the vault. To begin with, the Backup admin must not have any permissions on the Resource Guard.
- Security admin: Owner of the Resource Guard and serves as the gatekeeper of critical operations on the vault. Hence, the Security admin controls permissions that the Backup admin needs to perform critical operations on the vault.
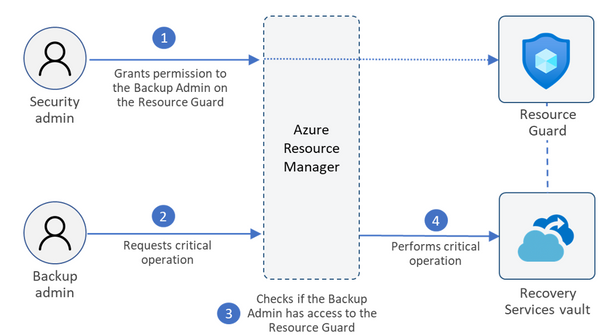
To perform a critical operation that is protected by MUA, the Backup admin must first obtain the right set of permissions on the Resource Guard.
Using MUA for Recovery Services vaults
Described below is a typical scenario for configuring and using MUA for Recovery Services vaults.
- The Backup admin creates the Recovery Services vault. They can also configure MUA on existing vaults.
- The Security admin creates the Resource Guard. The Resource Guard can be in a different subscription or a different tenant with respect to the Recovery Services vault. It must be ensured that the Backup admin does not have Contributor permissions on the Resource Guard.
- The Security admin grants the Reader role to the Backup Admin for the Resource Guard (or a relevant scope). The Backup admin requires the reader role to enable MUA on the vault.
- The Backup admin now navigates to the vault and configures it to be protected by MUA and provides the Resource Guard to be used.
- Now, if the Backup admin wants to perform a critical operation on the vault, they need to request access to the Resource Guard. The Backup admin can contact the Security admin for details on gaining access to perform such operations. They can do this using Privileged Identity Management (PIM) or other processes as mandated by the organization.
- The Security admin temporarily grants the Contributor role on the Resource Guard to the Backup admin to perform critical operations.
- Now, the Backup admin initiates the critical operation.
- The Azure Resource Manager checks if the Backup admin has sufficient permissions or not. Since the Backup admin now has Contributor role on the Resource Guard, the request is completed.
- If the Backup admin did not have the required permissions/roles, the request would have failed.
- The security admin ensures that the privileges to perform critical operations are revoked after authorized actions are performed or after a defined duration. Using JIT tools Azure Active Directory Privileged Identity Management may be useful in ensuring this.
Refer to the documentation to know more about configuring and using multi-user authorization for Backup.
Published on:
Learn moreRelated posts
Automating Business PDFs Using Azure Document Intelligence and Power Automate
In today’s data-driven enterprises, critical business information often arrives in the form of PDFs—bank statements, invoices, policy document...
Azure Developer CLI (azd) Dec 2025 – Extensions Enhancements, Foundry Rebranding, and Azure Pipelines Improvements
This post announces the December release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) Dec 2025 – Extensions En...
Unlock the power of distributed graph databases with JanusGraph and Azure Apache Cassandra
Connecting the Dots: How Graph Databases Drive Innovation In today’s data-rich world, organizations face challenges that go beyond simple tabl...
Azure Boards integration with GitHub Copilot
A few months ago we introduced the Azure Boards integration with GitHub Copilot in private preview. The goal was simple: allow teams to take a...
Microsoft Dataverse – Monitor batch workloads with Azure Monitor Application Insights
We are announcing the ability to monitor batch workload telemetry in Azure Monitor Application Insights for finance and operations apps in Mic...
Copilot Studio: Connect An Azure SQL Database As Knowledge
Copilot Studio can connect to an Azure SQL database and use its structured data as ... The post Copilot Studio: Connect An Azure SQL Database ...
Retirement of Global Personal Access Tokens in Azure DevOps
In the new year, we’ll be retiring the Global Personal Access Token (PAT) type in Azure DevOps. Global PATs allow users to authenticate across...
Azure Cosmos DB vNext Emulator: Query and Observability Enhancements
The Azure Cosmos DB Linux-based vNext emulator (preview) is a local version of the Azure Cosmos DB service that runs as a Docker container on ...