Discover, monitor and protect the use of Generative AI apps

Organizations are adopting Generative AI at a rapid rate. For instance, it took only 2 months for ChatGPT to reach 100 million users, one of the fastest adopted technologies ever. A core challenge is having visibility into hundreds of newly developed Generative AI apps and understanding their risk. As employees incorporate Generative AI apps into their daily activities, security teams struggle with how to effectively manage these apps in a secure way without disrupting productivity. According to Gartner, more than 80% of enterprises will be using Generative AI apps or deploy Generative AI-enabled applications by 2026. In addition, there are already many Generative AI apps available today, so even if an organization blocks access to a common Generative AI app, employees can pivot to using other ones on the market.
To help companies navigate the sprawl of Generative AI apps and provide ways to enable users to safely interact with these apps without sacrificing productivity, we announced at Ignite that Microsoft Defender for Cloud Apps and Microsoft Purview released new capabilities to help organizations to secure the use of AI. We are thrilled to share that the Defender for Cloud Apps discovery capabilities (extension to over 400 Generative AI apps) is now generally available.
Discover Generative AI apps and understand their risk
Security teams can use Defender for Cloud Apps to discover and efficiently manage Generative AI apps. The first step is gaining visibility into the ones in use. The cloud app catalog now contains hundreds of new Generative AI apps that will enable security teams to discover the use and understand the risk each app poses. To help organizations quickly identify which apps are considered, “Generative AI,” a new category has been added to streamline this process.
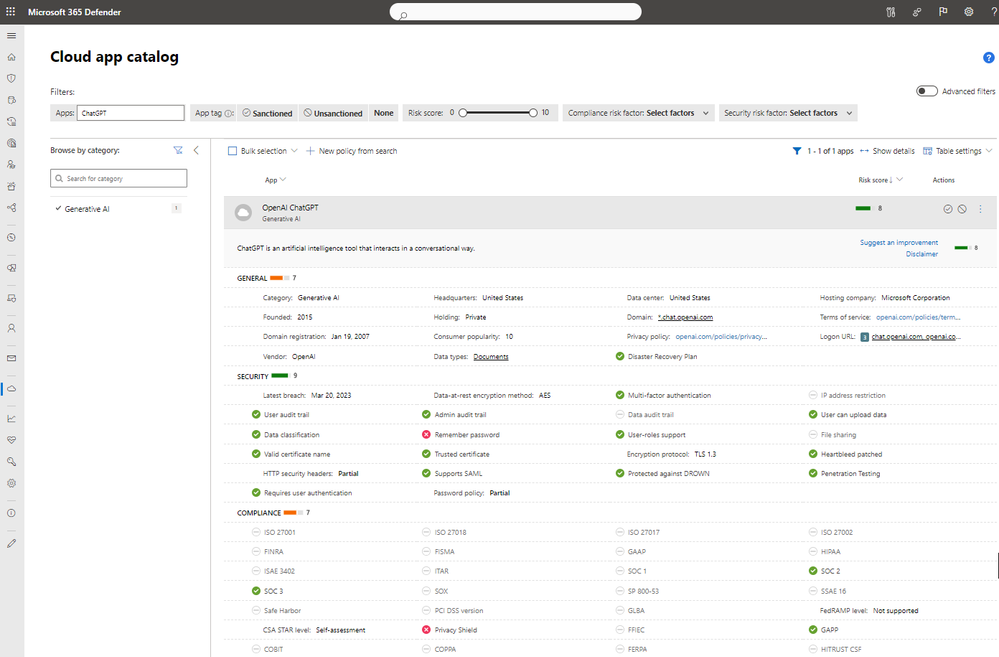
The category can be used in policies and tags to automate controls such as unsanctioning apps with a low-risk score, or apps that do not meet compliance standards, such as SOC2. For organizations that use the Defender for Endpoint integration, apps that have been tagged as, “unsanctioned,” will be instantly blocked on onboarded devices. The list of apps will also include the list of risk parameters available for other applications, see Figure 1.
Figure 1. A Generative AI application with its risk factors shown in the cloud app catalog
Security teams can setup policies to automatically trigger an alert when a new Generative AI app is being used in their organization, see Figure 2.
Figure 2. A policy template that will alert when a new Generative AI has been used in the organization’s environment.
Protect your organization from risky Generative AI apps
Organizations may choose to block the usage of apps for various reasons. Some are concerned that sensitive data will be unknowingly shared with applications and exposed later to an audience outside the organization. This could cause the organization to block the usage of all unmanaged GAI apps. While other companies need to ensure all the apps in use are compliant according to different standards, such as SOC2, or HIPAA. To easily block unsanctioned apps from being used on protected devices, follow the following steps:
- Connect the Defender for Endpoint log to Defeder for Cloud Apps by following the few simple steps described here (or alternatively ingest logs from 3rd party appliances like described here).
- Investigate the usage of Generative AI applications and filter on applications from “Generative AI” category, using the discovery dashboard shown in Figure 3.
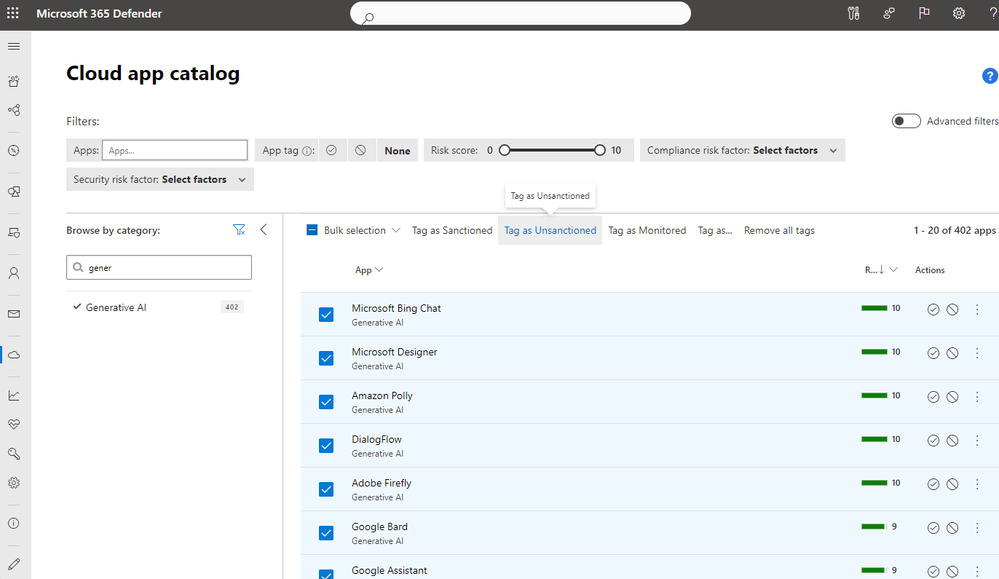
Figure 3. Discovered apps filtered on the “Generative AI,” category
- Decide if you want to unsanction applications with this category in the “Cloud App Catalog” page based on the different filtering options shown in Figure 4.
Figure 4. Generative AI apps in the cloud app catalog that could be tagged as unsanctioned
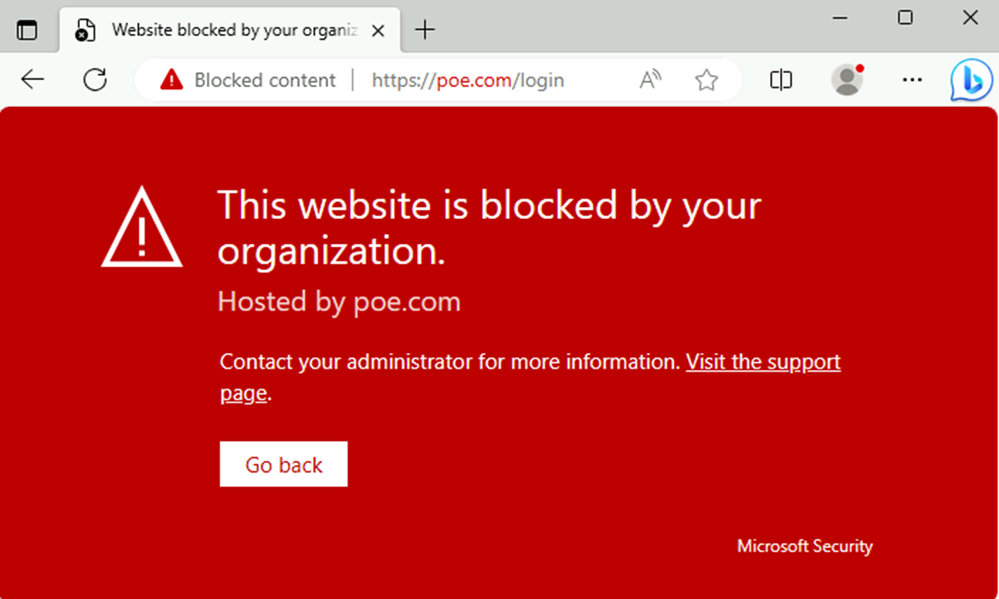
- To connect Defender for Endpoint to Defender for Cloud Apps, in Microsoft Defender XDR navigate to Settings > Endpoint > Advanced Features and toggle the radio button to “on” for Microsoft Defender for Cloud Apps. If the user tries to access an unsanctioned app, then they will see the following block screen in Figure 5.
Figure 5. Block screen presented when a user tries to access an unsanctioned app
It can be challenging to find the balance between security and productivity when it comes to the use of Generative AI apps. As the technology continues to evolve, it is critical that security teams adopt safe practices to ensure their users and data are protected from risky apps.
Resources:
Watch the Ignite on-demand session with Microsoft Purview.
Watch The Future of Security with AI keynote session from Ignite
Read about Ignite XDR news
Read about the Microsoft Purview & Microsoft Defender news
Published on:
Learn more