Microsoft Defender for Identity expands its coverage with new AD CS sensor!
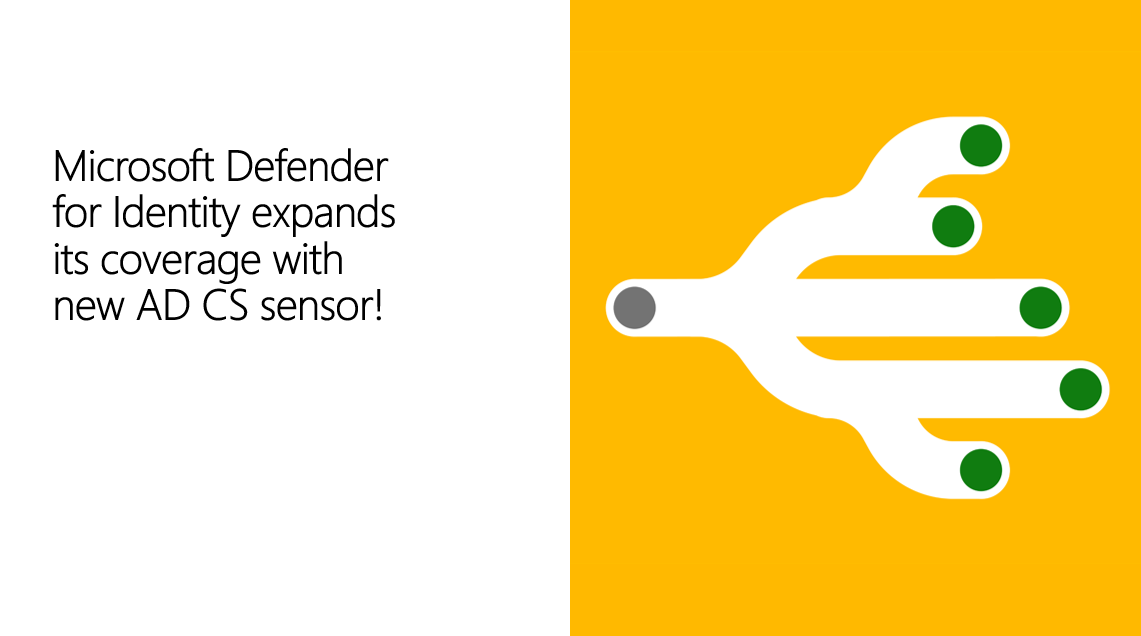
Active Directory (AD) continues to be a major component of most organizations’ IT footprint, and as such, attackers are constantly hunting for vulnerabilities or misconfigurations they can exploit. To stay ahead of these new tactics, and ensure we continue to deliver powerful security solutions to our customers, our research and engineering teams are always evolving and updating our offerings.
One such enhancement is a new Microsoft Defender for Identity sensor that can be deployed on Active Directory Certificate Services (AD CS) servers. This new sensor builds on the existing detections for suspicious certificate usage available today and extends Defender for Identities capabilities and coverage more comprehensively across identity environments.
What is Active Directory Certificate Services?
In Active Directory environments, Active Directory Certificate Services (AD CS) is a role in Windows Server that allows you to create and manage public key infrastructure (PKI) certificates. These certificates are used to establish trusted and secure communication between users, devices, and applications on a network or, more importantly for this discussion, as password- equivalents for user authentication.
While AD CS is not a default element of every AD instance, the adoption of new authentication methods has led to rather widespread deployment. Despite this popularity the security capabilities around this infrastructure has not been a focus. Pairing the lack of protection with the fact that the certificates managed via these servers replace passwords and other authentication mechanisms, they are a ripe target for would be attackers. Further fueling the issue is that AD CS can be extremely easy to misconfigure.
To put the gravity of these vulnerabilities into perspective lets take a hypothetical example. In this case a malicious actor has successfully exploited a misconfiguration in your AD CS server and has minted or stolen a certificate. Because that certificate acts as a password-equivalent the identity and access management controls you have in place will be bypassed and the attacker will have gained a foothold in your organization, all without having to compromise a single password.
What are the benefits of this new sensor?
The new sensor will provide Defender for Identity customers with new detections and security recommendations in Secure Score including:
New detections:
- Domain-controller certificate issuance for a non-DC – also known as ESC8, an attacker can relay NTLM authentication to ADCS, issuing a certificate for the impersonated entity. When the victim of such an attack is a Domain Controller, this can result in full domain compromise.
- Suspicious disable of audit logs of AD CS – Attackers will often disable the logs so that they can perform malicious actions without leaving any trace of their activities. Defender for Identity will now track the audit configurations and alert you when that change has been made.
-
Suspicious deletion of the certificate database – Attackers will often delete certificate requests in an effort to cover their tracks. This new detection will monitor that activity by tracking when and by whom those requests are deleted.
-
Suspicious modifications to the AD CS settings (coming soon)- This event suggests that a change was made to the access control list (ACL) of the certification authority itself. This allows attackers to perform certificate authority level operations that potentially can lead to domain takeover.
Upcoming security recommendations in Secure Score:
- Prevent users from requesting a certificate valid for arbitrary users based on a vulnerable certificate template (ESC1)
- Edit overly permissive Certificate Template with privileged EKU (Any purpose EKU or No EKU) (ESC2)
- Edit misconfigured enrollment agent certificate template (ESC3)
- Edit misconfigured certificate templates ACL (ESC4)
- Edit misconfigured certificate templates owner (ESC4)
Learn more about the new sensor in our documentation here and check back for updates on new detections and security recommendations around AD CS coming over the next few weeks.
Published on:
Learn more