Public facing Azure Container Registry Reference Architecture
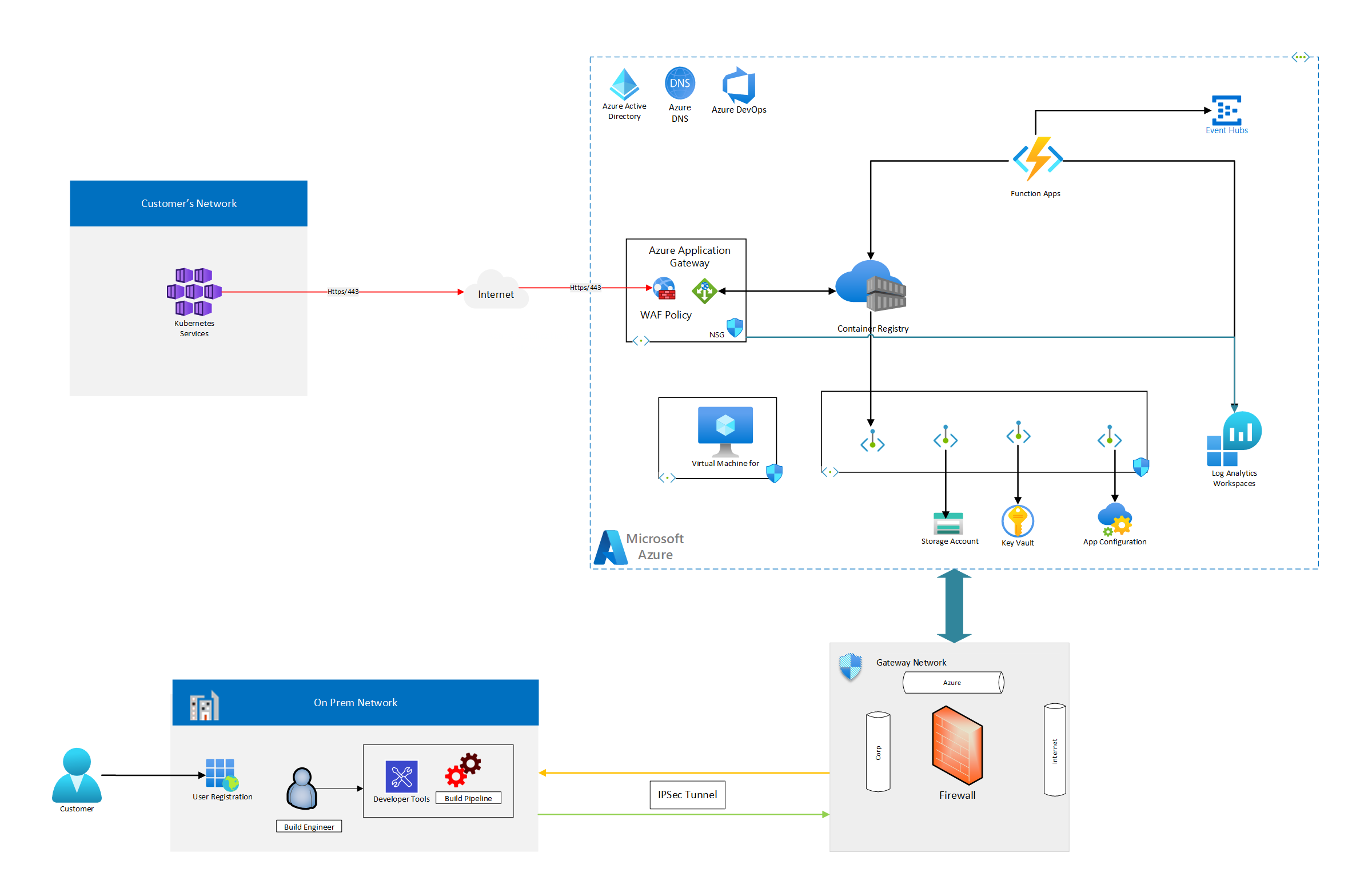
- Host container images for secured on-demand delivery of customer's application software and updates.
- Restrict embargo countries/regions to download and deploy hosted container images.
- Implement custom DNS solution for publicly accessible container registry.
Architecture
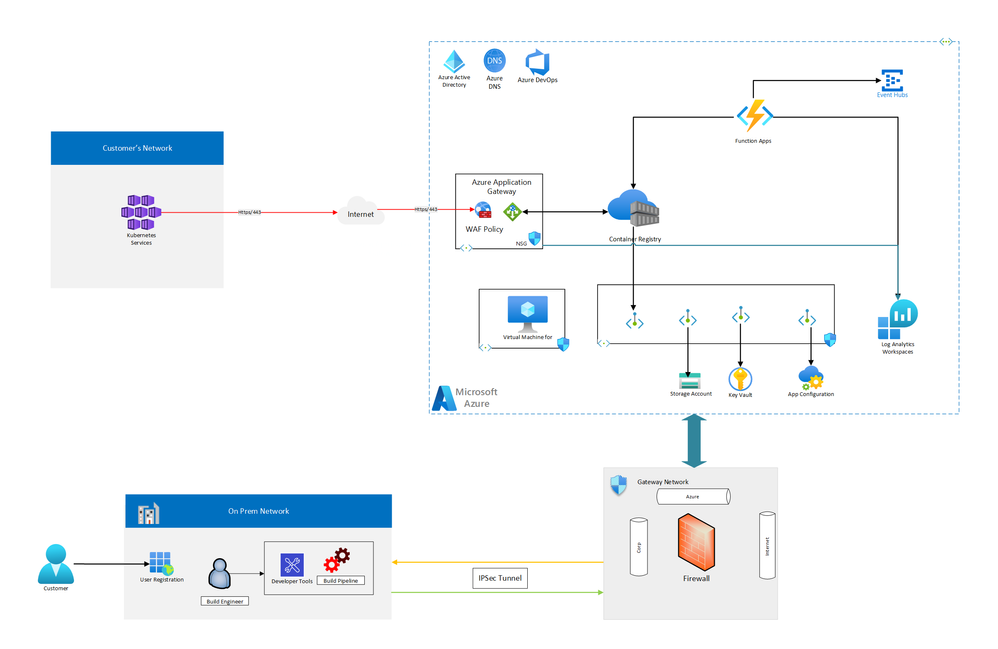
Components
- Azure Key Vault: Key Vault is provisioned for storing sensitive values and keys used specifically for on-premises systems like build pipeline and user registration application to access ACR API and function App to publish data to on-premises applications.
- Azure App Gateway: Azure App Gateway with WAF v2 is used to load balance and route traffic to Azure Container registry and provide Layer 7 connectivity to authenticate/authorize customer applications and download container images.
- Container registry: The container images for the workload are stored in a managed container registry. In this architecture, a single Azure Container Registry is used for all Kubernetes instances in the cluster. Geo-replication for Azure Container Registry enables replicating images to the selected Azure regions and providing continued access to images even if a region is experiencing an outage.
- Log Analytics: Regional Log Analytics instances are used for storing regional networking metrics and diagnostic logs. Additionally, a shared Log Analytics instance is used to store metrics and diagnostic logs for the ACR instance.
- Logging and threat detection: Microsoft Defender for Cloud built-in threat detection capability for Container Registry provides another layer of security intelligence. It detects unusual and potentially harmful attempts to access or exploit the Container Registry resources.
- Azure Functions: Azure Functions serves as the processing engine to manage the life cycle of container images in ACR. These functions also process specific logs and monitor security events and notify security and monitoring operations control via Azure Event Hubs.
- Kubernetes Cluster: Kubernetes Cluster is a consuming application cluster deployed by consumers of the hosted container images in Azure Container Registry.
- Hybrid Cloud Networking: Host the applications and tools (DevOps) used by developers to create container images and publish them to Azure Container Registry. Gateway Network is implemented to provide a secure communication layer between on-premises applications and applications hosted in Azure.
Azure Resources Configuration
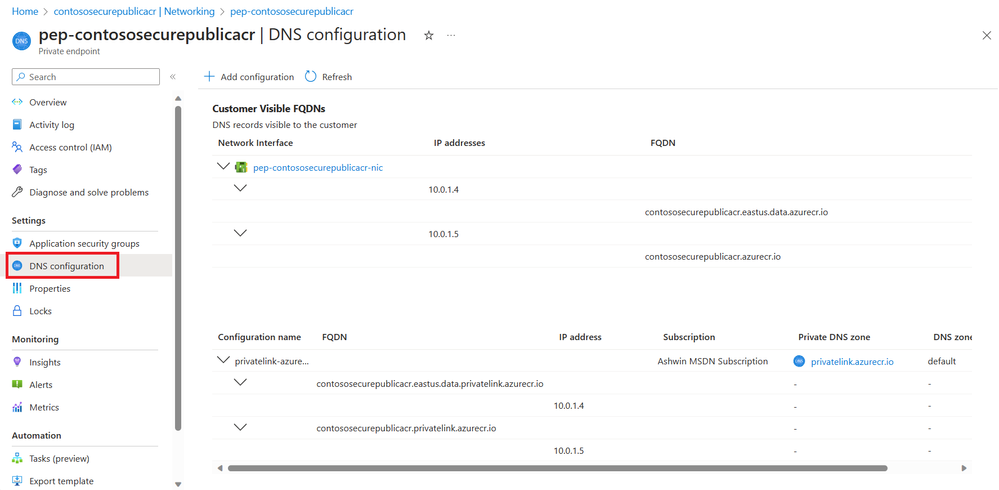
Azure Container Registry
Overview
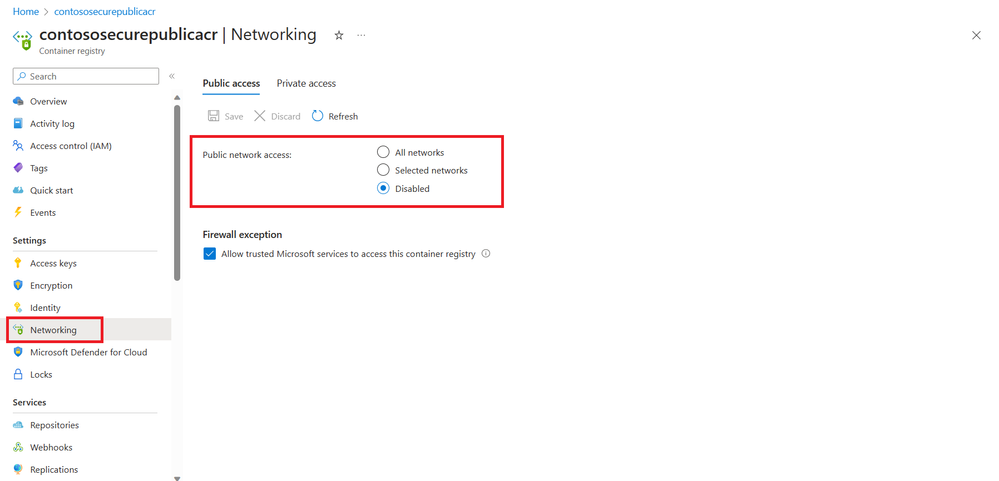
Public access
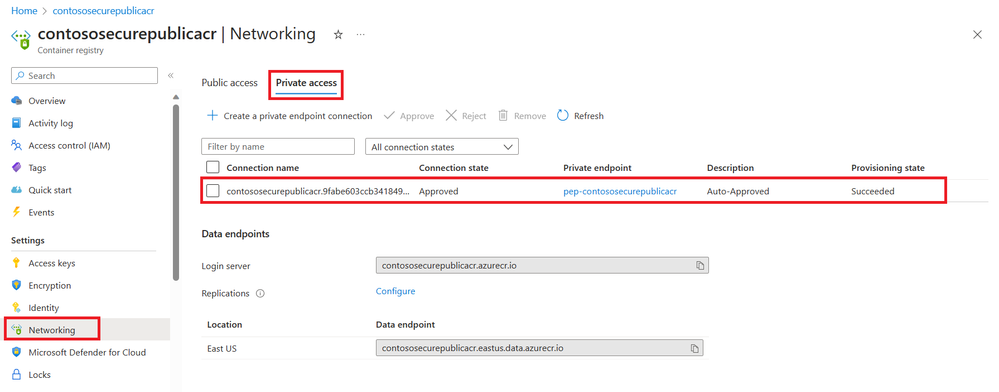
Private access
Azure Application Gateway
Overview
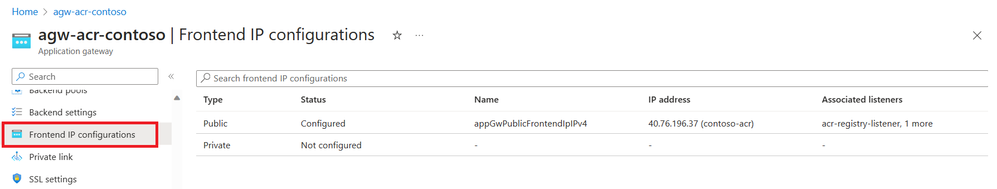
App Gateway Frontend IP Configuration
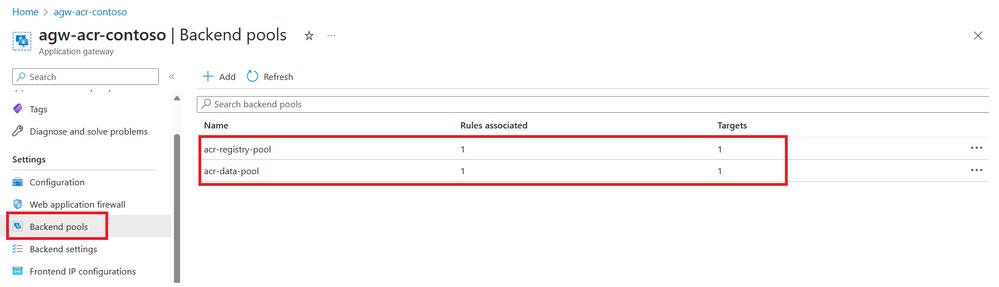
App Gateway Backend pools
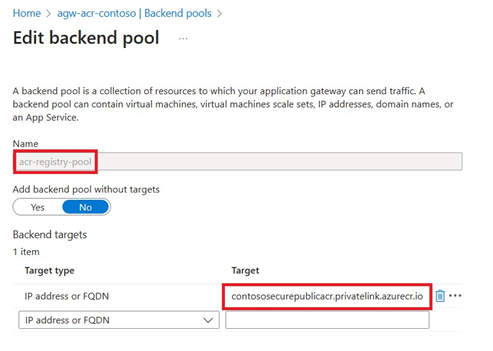
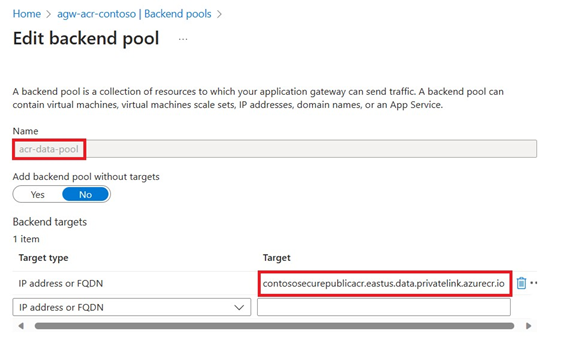
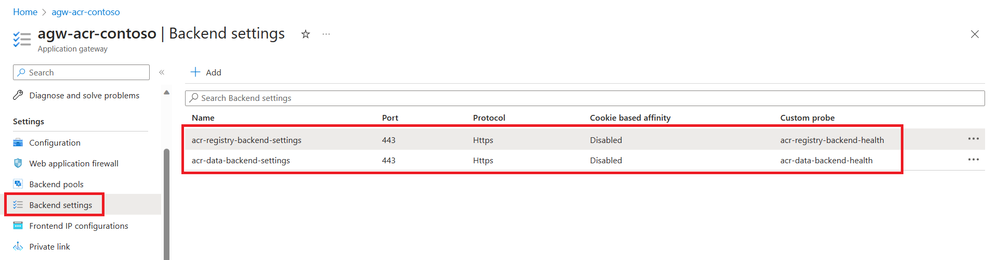
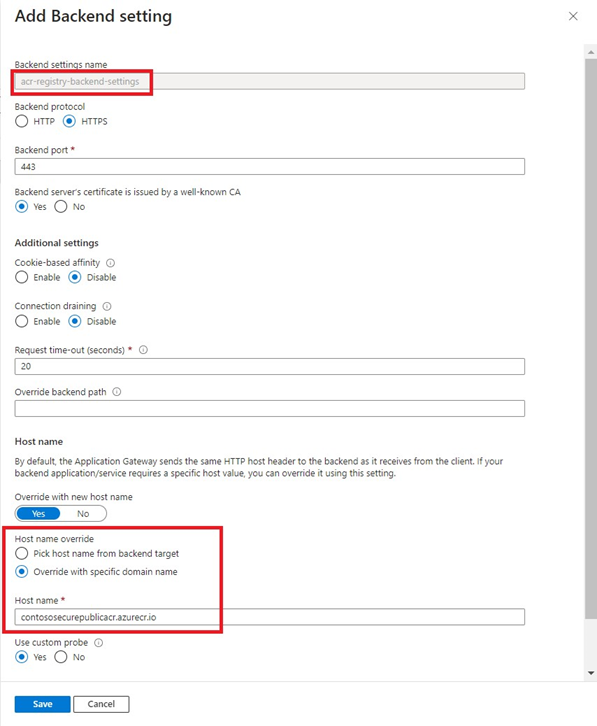
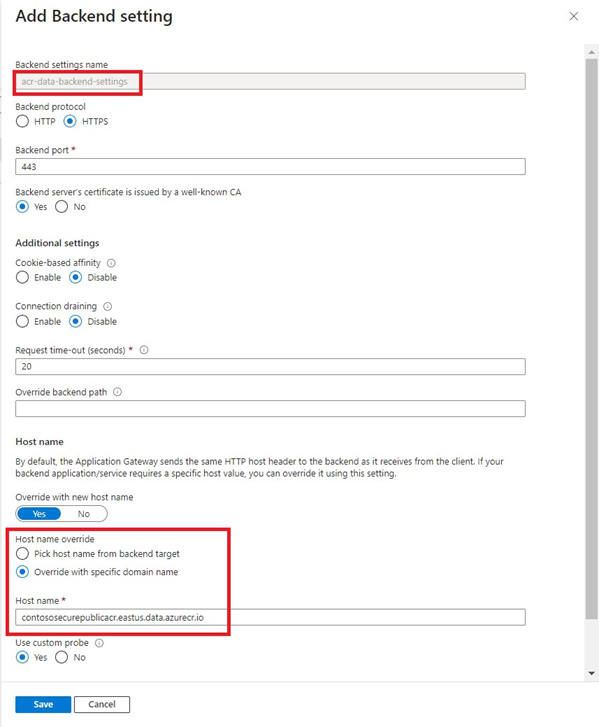
App Gateway Backend settings
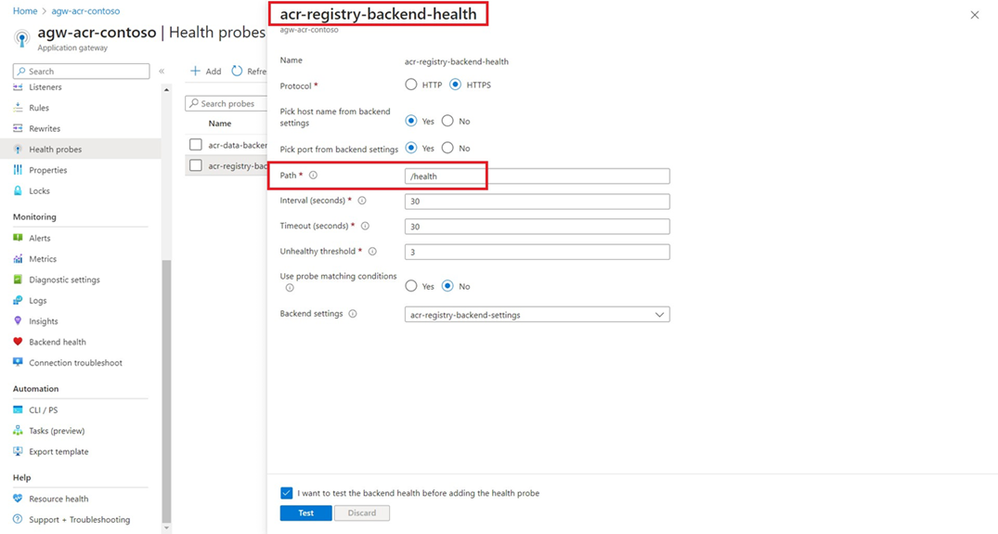
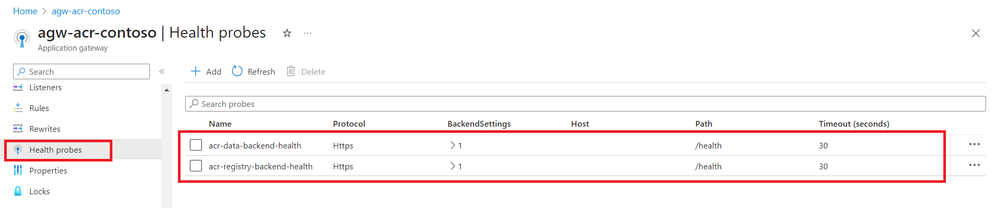
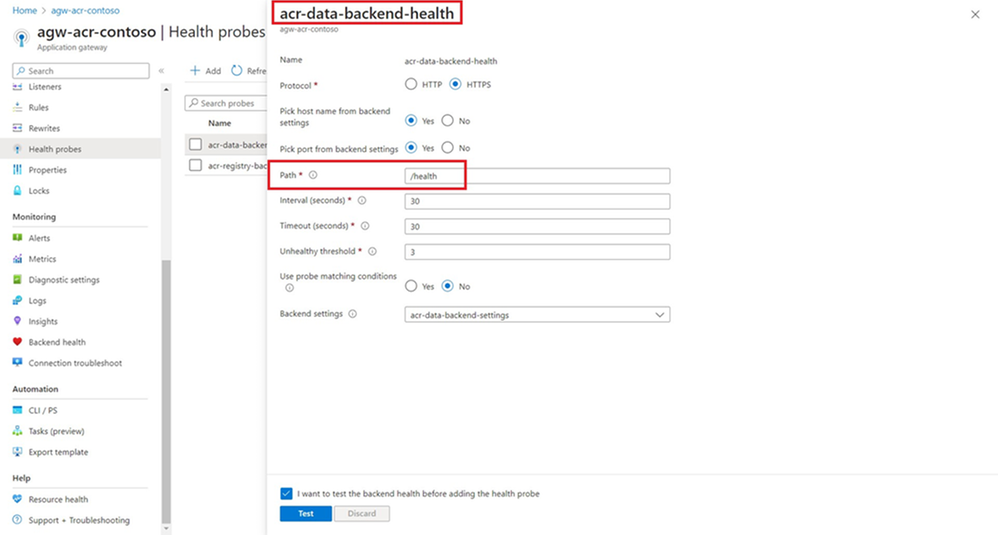
App Gateway Health probes
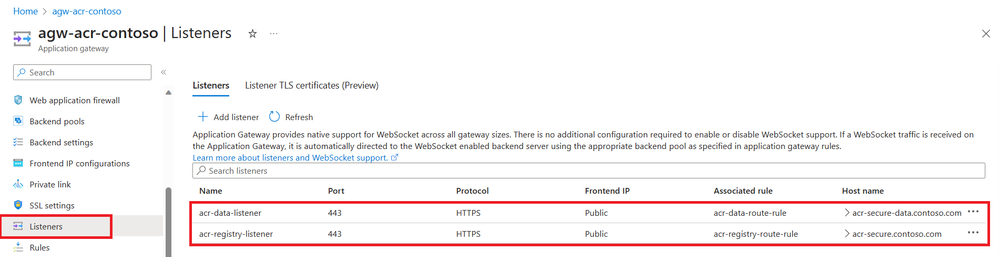
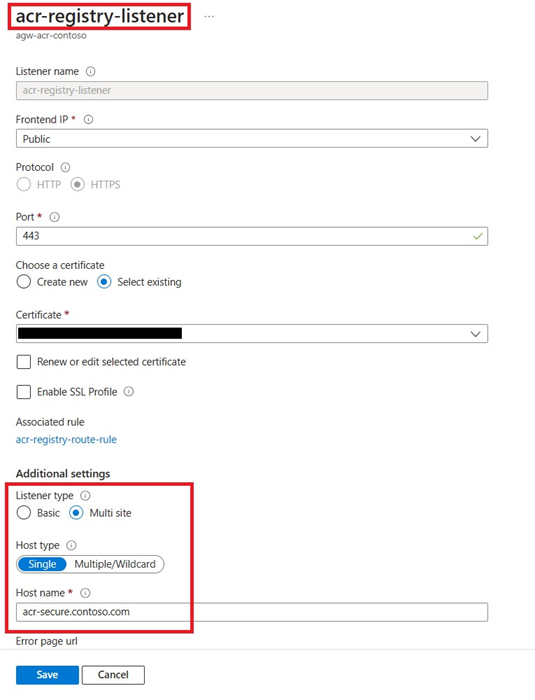
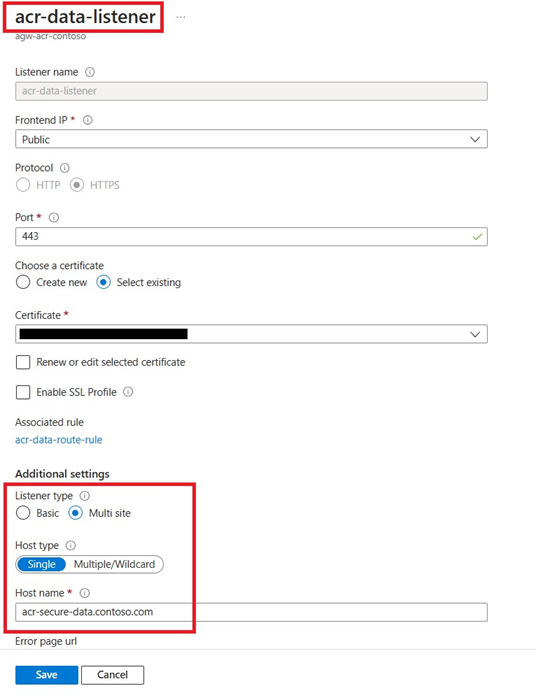
App Gateway Listeners
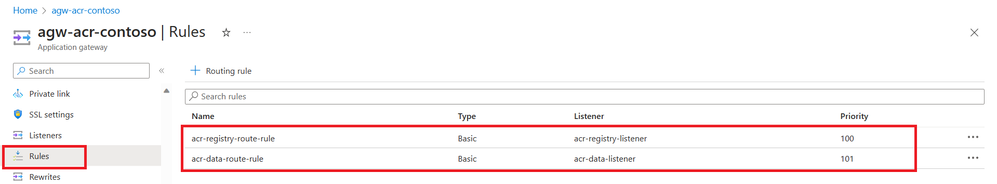
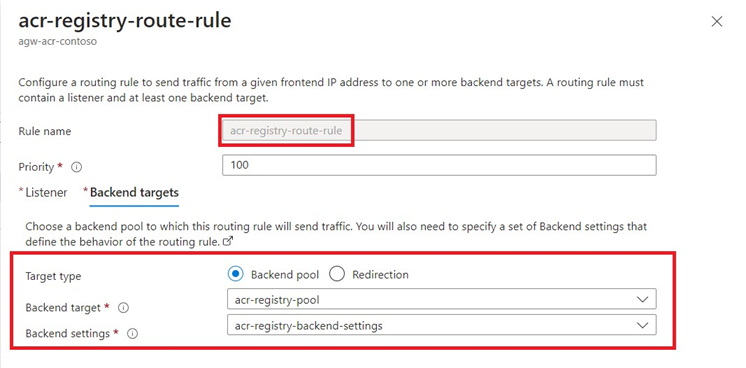
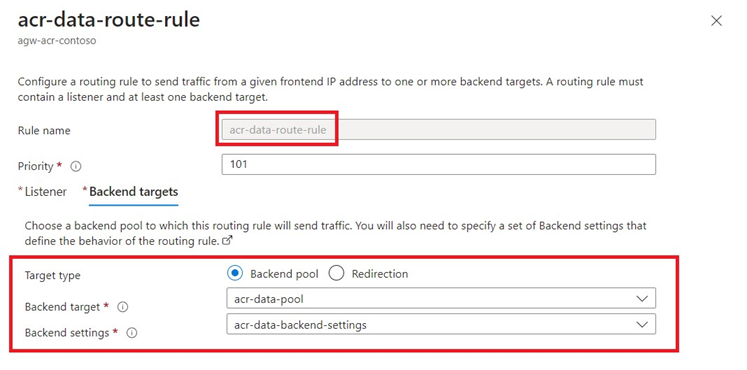
App Gateway Rules
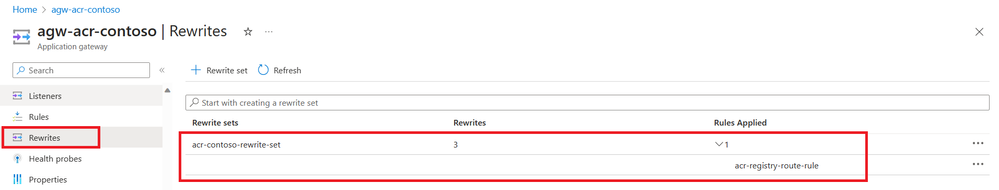
App Gateway Rewrites
Since ACR returns its own endpoints in various REST APIs, the application gateway's "rewrite headers" capability is used to replace the ACR endpoints with App gateway endpoints.
- Rewrite Location Header
- Rewrite WWW-Authenticate Header
- Rewrite Data Location Header
- Rewrite Location Header:
The 'Rewrite Location Header' rule rewrites the 'Location' header in the HTTP response that matches ACR endpoint to the registry/login endpoint of the app gateway when the status code is 302.
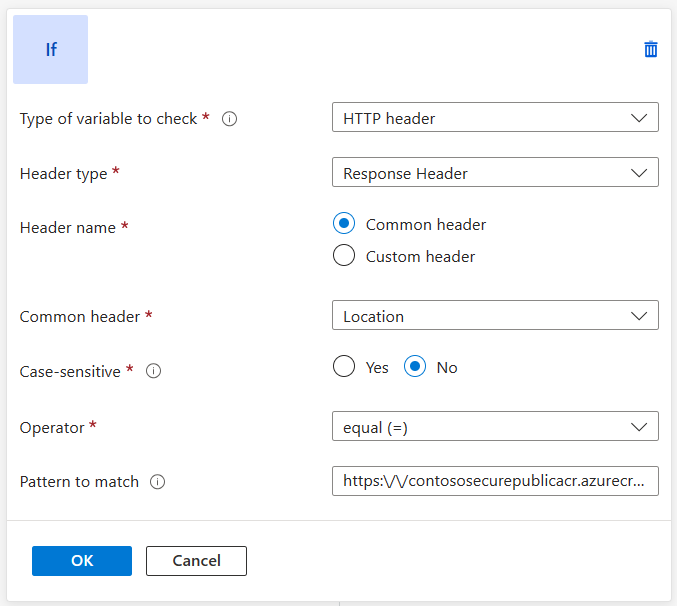
- Add a condition to evaluate whether the location header in the response contains the Azure Container Registry endpoint, contososecurepublicacr.azurecr.io in this example:
-
Select Add condition and then select the box containing the If instructions to expand it.
-
In the Type of variable to check list, select HTTP header.
-
In the Header type list, choose Response Header.
-
Select Common header under Header name.
-
In the Common header list, select Location.
-
Under Case-sensitive, select No.
-
In the Operator list, select equal (=).
-
Enter the regular expression pattern:
https:\/\/contososecurepublicacr.azurecr.io(.*)$, and make sure to substitute 'contososecurepublicacr.azurecr.io' with your ACR instance endpoint. -
Select OK
-
-
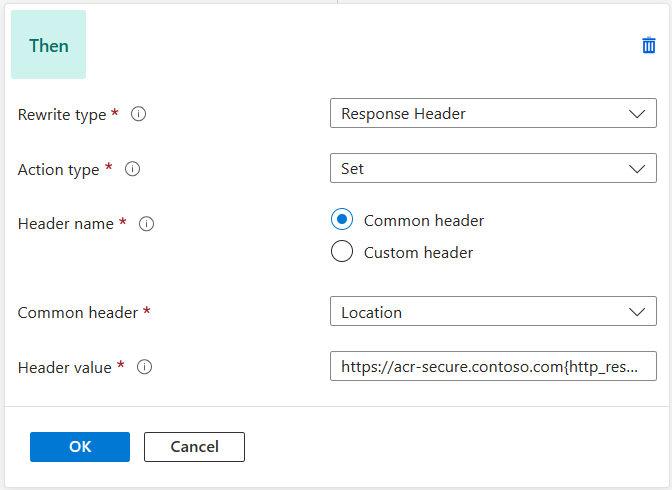
Add an action to rewrite the location header:
-
In the Rewrite type list, select Response Header.
-
In the Action type list, select Set.
-
Under Header name, select Common header.
-
In the Common header list, choose Location.
-
Use
https://acr-secure.contoso.com{http_resp_Location_1}as the header value, and be sure to substitute 'acr-secure.contoso.com' with your custom domain endpoint. This action replaces contososecurepublicacr.azurecr.io with acr-secure.contoso.com in the location header. -
Select OK.
-
- Add a condition to evaluate whether the location header in the response contains the Azure Container Registry endpoint, contososecurepublicacr.azurecr.io in this example:
- Rewrite WWW-Authenticate Header:
The 'Rewrite WWW-Authenticate Header' rule modifies the 'WWW-Authenticate' header in the HTTP response that matches ACR endpoint to the registry/login endpoint of the app gateway when the status code is 401.
-
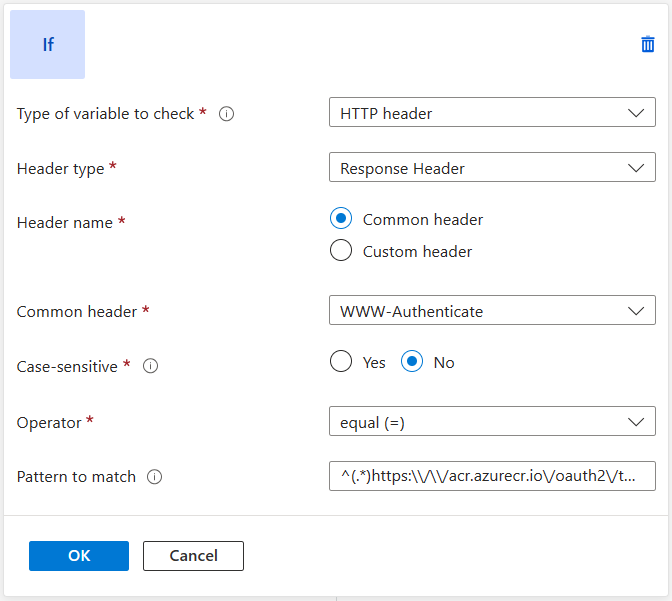
Add a condition to evaluate whether the WWW-Authenticate header in the response contains the Azure Container Registry endpoint, contososecurepublicacr.azurecr.io/oauth2/token in this case:
-
Select Add condition and then chooses the box containing the If instructions to expand it.
-
In the Type of variable to check list, select HTTP header.
-
In the Header type list, choose Response.
-
In the Header name, select Common header.
-
In the Common header list, choose WWW-Authenticate.
-
Under Case-sensitive, select No.
-
In the Operator list, select equal (=).
-
Enter the regular expression pattern:
^(.*)https:\/\/contososecurepublicacr.azurecr.io\/oauth2\/token(.*)$, and make sure to replace 'contososecurepublicacr.azurecr.io' in the pattern with your custom domain endpoint. -
Select OK
-
-
Add an action to rewrite the WWW-Authenticate header:
-
In the Rewrite type list, select Response Header.
-
In the Action type list, choose Set.
-
Under Header name, select Common header.
-
In the Common header list, choose WWW-Authenticate.
-
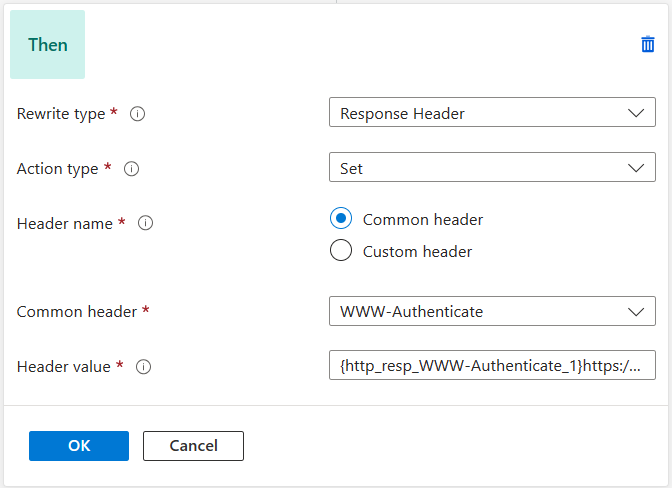
Specify the header value:
{http_resp_WWW-Authenticate_1}https://acr-secure.contoso.com/oauth2/token{http_resp_WWW-Authenticate_2}, and be sure to substitute 'acr-secure.contoso.com' with your custom domain endpoint. This action rule replaces contososecurepublicacr.azurecr.io with acr-secure.contoso.com in the WWW-Authenticate header. -
Select OK.
-
-
- Rewrite Data Location Header:
The 'Rewrite Data Location Header' rule rewrites the 'Location' header in the HTTP Response that matches the ACR data endpoint to the data endpoint of the app gateway when the status code is 302.
-
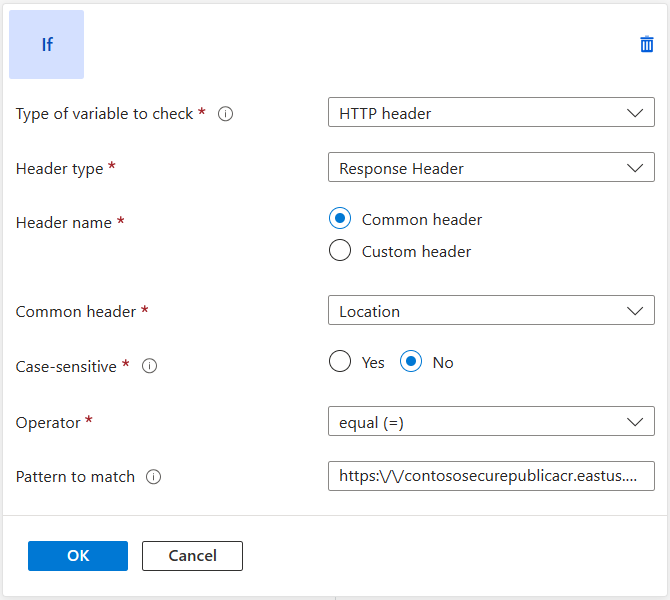
Add a condition to evaluate whether the location header in the response contains contososecurepublicacr.eastus.data.azurecr.io:
-
Select Add condition and then choose the box containing the If instructions to expand it.
-
In the Type of variable to check list, select HTTP header.
-
In the Header type list, choose Response Header.
-
Select Common header under Header name.
-
In the Common header list, choose Location.
-
Under Case-sensitive, select No.
-
In the Operator list, select equal (=).
-
Enter the regular expression pattern:
https:\/\/contososecurepublicacr.eastus.data.azurecr.io(.*)$, and make sure to substitute 'contososecurepublicacr.eastus.data.azurecr.io' with your ACR instance data endpoint url. -
Select OK
-
-
Add an action to rewrite the location header:
-
In the Rewrite type list, select Response Header.
-
In the Action type list, choose Set.
-
Under Header name, select Common header.
-
In the Common header list, choose Location.
-
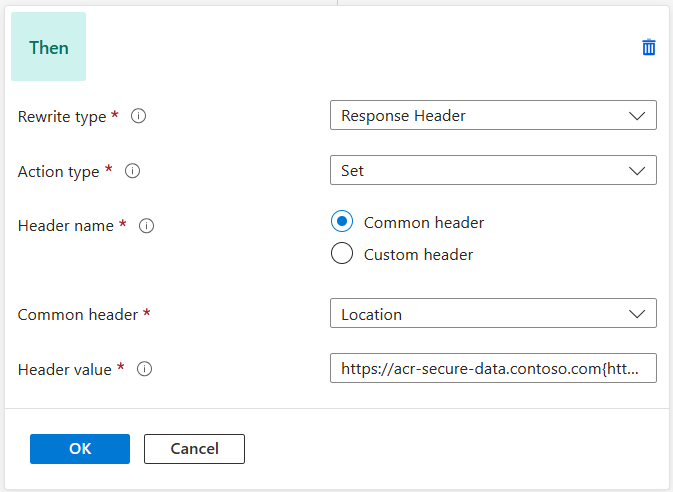
Specify the header value:
https://acr-secure-data.contoso.com{http_resp_Location_1}, and make sure to substitute 'acr-secure-data.contoso.com' with your custom domain data endpoint. This action effectively replaces contososecurepublicacr.eastus.data.azurecr.io with acr-secure-data.contoso.com in the location header. -
Select OK.
-
-
Azure Web Application Firewall (WAF)
Overview
Azure Web Application Firewall (WAF) on Azure Application Gateway provides the ability to Geo-filter traffic, permitting or blocking access from certain countries/regions to applications. This feature serves to restrict access to embargoed countries/regions or IPs identified by customer teams.

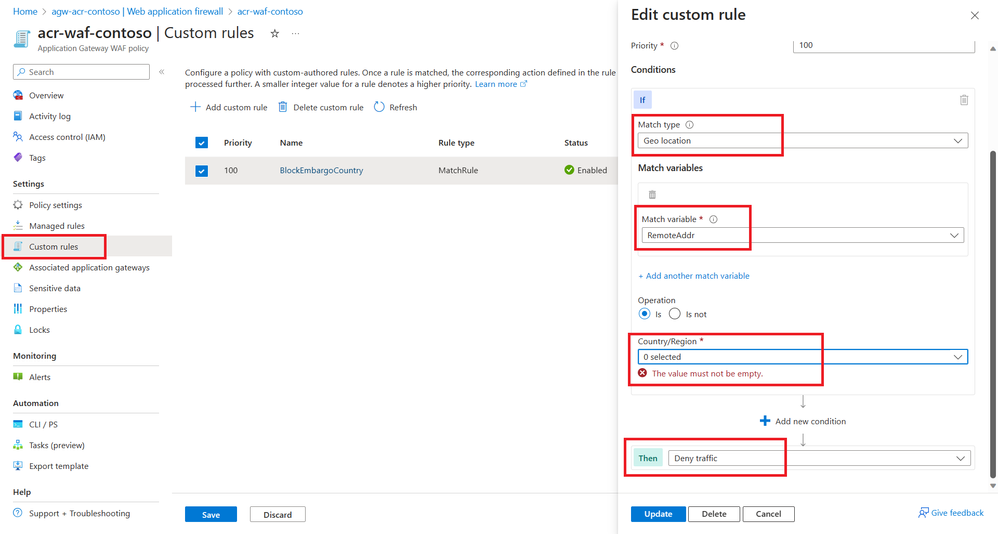
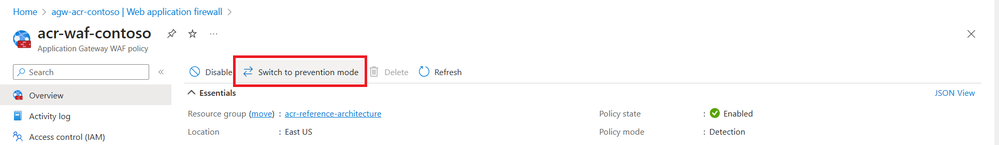
Next Steps
This reference architecture depicts the integration of Azure Container Registry (ACR) and Azure Application Gateway with WAF policy to allow public access to the container images while keeping the ACR private. It also provides granular access control using the ACR's token and scope map feature. This architecture can be further extended to using geo-replication enabled ACR for multiple regions, by deploying an app gateway instance in each geo-replicated region and setting up a performance-based traffic manager with multiple app gateway endpoints.
Related resources
Published on:
Learn moreRelated posts
Choosing the right Virtual Machine on Azure
Build and run everything from simple web apps to AI supercomputing by matching each workload to the right Azure VM in minutes. Find and know e...
Record Scanner for vinyl collectors cuts costs with Azure Cosmos DB vector search
by Artur Drozdz, Founder of Record Scanner (recordscanner.com) If you’re like me, there’s at least one room in your home with an entire cabine...
🚀 Introducing the New VS Code Extension for Azure Cosmos DB
We’re excited to share that the Azure Databases extension for Visual Studio Code is now officially rebranded as the Azure Cosmos DB extension!...
AI-based T-SQL Refactoring: an automatic intelligent code optimization with Azure OpenAI
This article presents an AI-powered approach to automating SQL Server code analysis and refactoring. The system intelligently identifies ineff...
Azure Boards integration with GitHub Copilot (Private Preview)
Several months ago, GitHub introduced the public preview of its Copilot coding agent, a powerful new capability that allows you to assign GitH...
What is Azure Key Vault and How It Secures Microsoft Dynamics 365 CRM Systems?
Azure Key Vault is a service by Microsoft Azure that helps securely store and manage sensitive information such as API keys, connection string...