Upgrading your server and client TLS protocol just got easier using Automanage Machine Configuration
Ensuring secure communication protocols across server environments has been a clear requirement for IT admins, operators, and developers for the past two decades. What wasn’t clear was how to set a desired communication protocol and maintain this at scale, until now.
To prevent bad actors from accessing or disrupting sensitive data as it moves through the internet, we have relied on various cryptographic protocols over the years, namely Secure Socket Layers (SSL) and Transport Layer Security (TLS). As weaknesses were discovered, new versions of SSL and then TLS were created and although technologies have evolved, so have the tactics of hackers and other cyber criminals.
As of 2020, TLS versions 1.0 and 1.1 are no longer supported. TLS 1.2 is required to maintain secure connections and offers higher performance on top of improved reliability. It does this by leveraging a combination of symmetric and asymmetric cryptography, including security improvements to both the client and server, and providing real solutions to serious security threats. In the past decade, TLS 1.0 and TLS 1.1 have proved to be vulnerable against cryptographic threats, notably BEAST, POODLE, and HEARTBLEED.
Now, using Automanage Machine Configuration, configuring your secure communications protocol across your servers running in Azure, or running anywhere else using Azure Arc is easier than ever. The rest of the post will walk through how to get started.
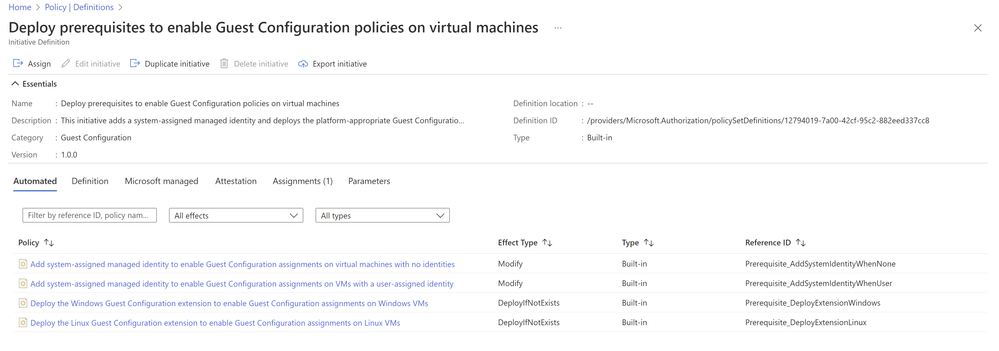
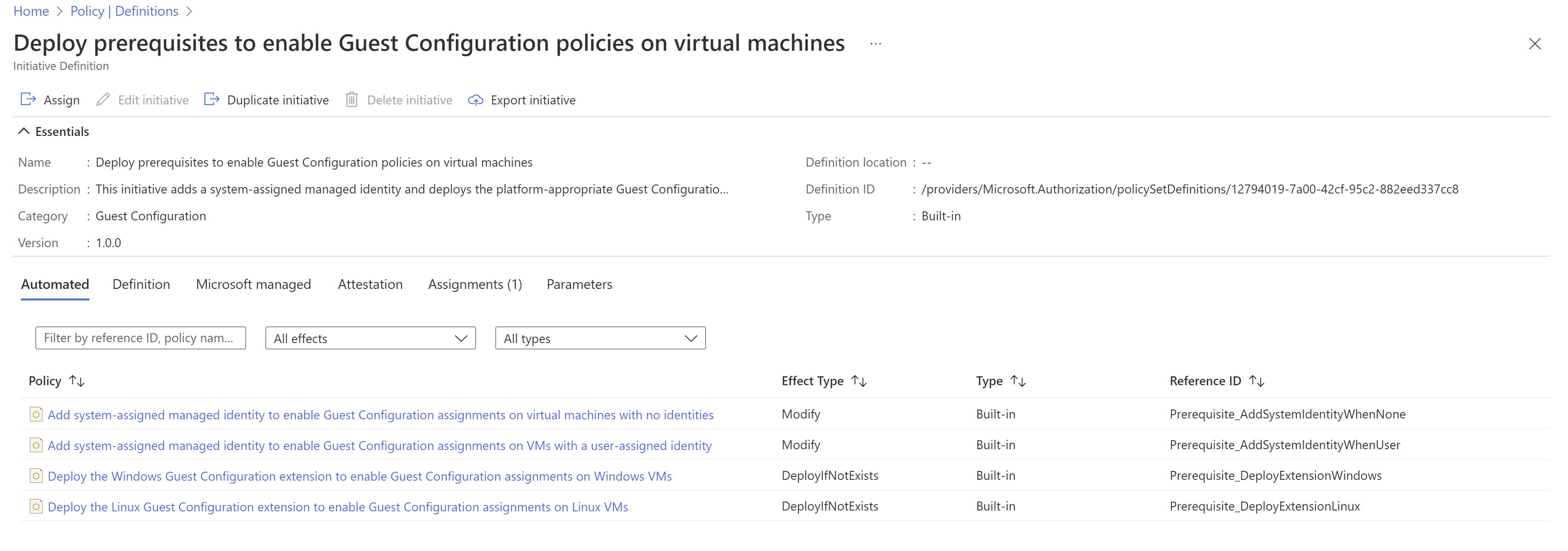
To get started with Automanage Machine Configuration on Azure VMs, assign the following pre-requisite initiative to get started: Deploy prerequisites to enable Guest Configuration policies on virtual machines. The initiative deploys both the extension, as well as a managed identity. For servers running outside of Azure, you’ll need to connect them using Azure Arc-enabled servers. Azure Arc enables you to leverage Automanage Machine Configuration and many other Azure services on your on-premises servers and VMs running in other clouds.
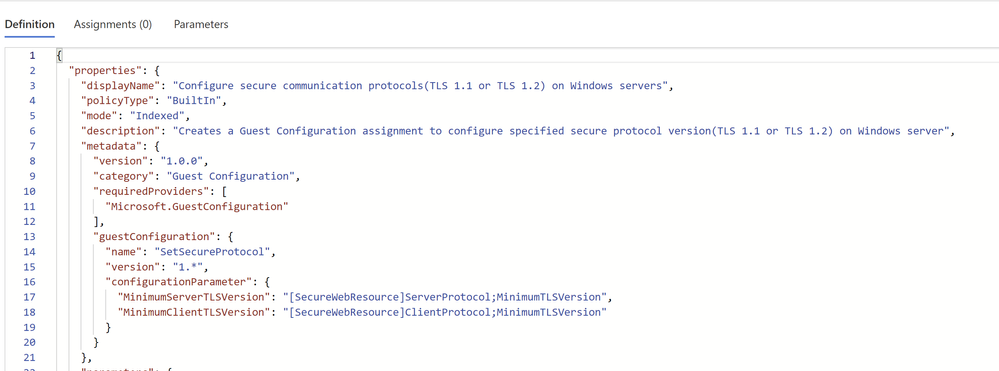
After you configure the pre-requisites, navigate to the built-in policy definition: Configure secure communication protocols (TLS 1.1 or TLS 1.2) on Windows servers.
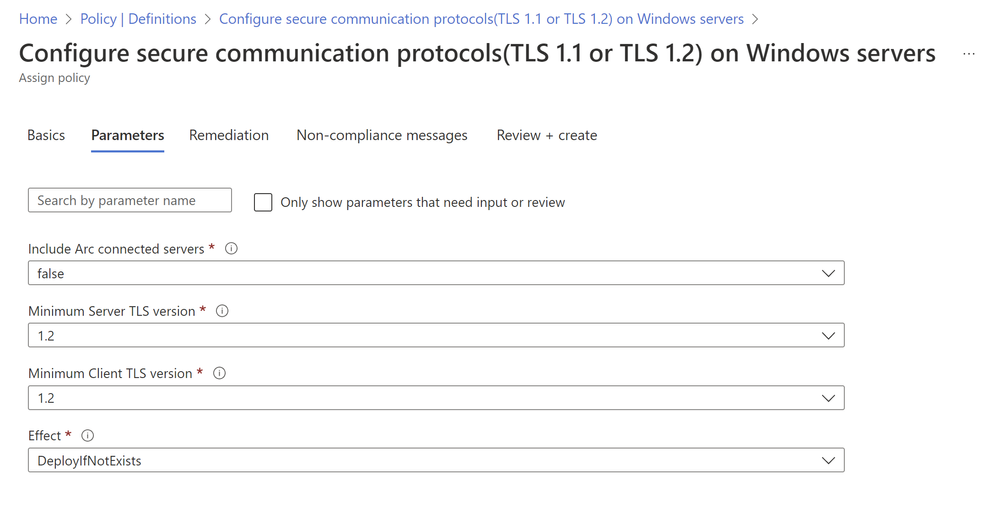
This policy can be assigned at the resource group, subscription group, or management group level. When navigating through the assignment process, you can choose which communications protocol to apply with TLS 1.2 set by default. You can also choose whether to apply the policy to Azure Arc-enabled servers.
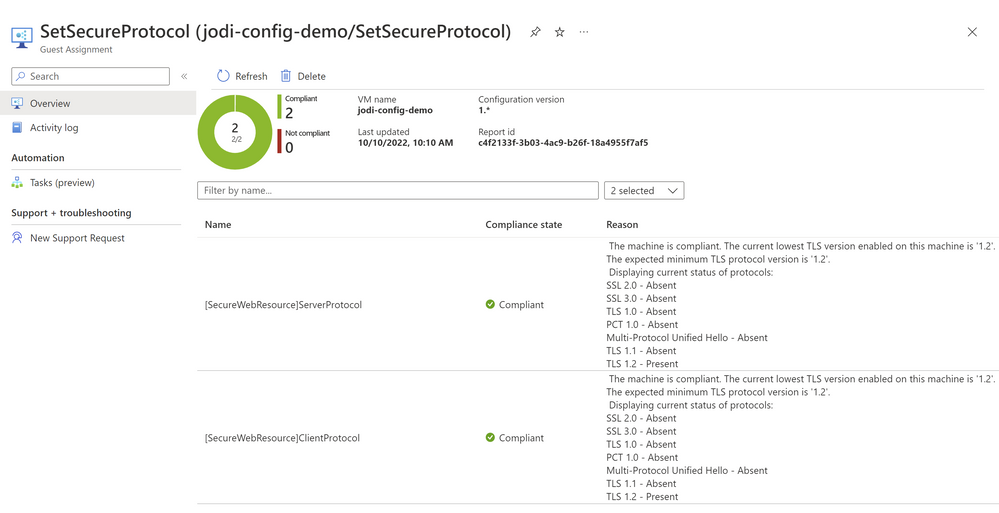
After the configuration has been assigned, the compliance status can be viewed in detail through navigating to the Guest Assignments page and scoping down to the impacted resources. You will be able to see the compliance status of your resources, as well as a deeper explanation describing the reasons for compliance or non-compliance.
For more information on Automanage Machine Configuration, please see aka.ms/mc-docs.
Please note that the use of Automanage Machine Configuration on Azure Arc-enabled servers will incur a charge of $6/server/month. You only pay the charge once no matter how many machine configuration policies you apply to the server. Learn more about Azure pricing
Published on:
Learn more