Top Threat Protection use cases in Microsoft Defender for Cloud Apps

The combined power of Microsoft Defender for Cloud Apps and Microsoft 365 Defender provides unique threat protection capabilities which use the native integration between a multi-purpose Cloud Access Security Broker (CASB) and an integrated XDR+SIEM platform. Security teams can protect their organizations from increasing and evolving cloud attacks that threaten the organization’s valuable data and assets managed by cloud apps, by maintaining secure posture, detecting, responding to breaches in real time, and investigating the activities in their cloud app environments.
In this blog, we will showcase the top examples from each part of the threat protection landscape, to protect your organization from cloud apps threats, according to the following classifications:
- Prevent – SaaS Security Posture Management (SSPM)
- Detect – Business Email Compromise (BEC) scenario
- Respond – Suspend user
- Investigate – Investigate a compromised user
Prevent
Today, most apps have capabilities that can be configured to your organization’s usage in a secure way without impacting productivity. Common configurations like enforcing multi-factor authentication for all users, maximum invalid login attempts, and verifying that drives’ owners belong to internal users only can easily help prevent potential breaches. The difficult task is ensuring these prevention configurations are in place. The two main challenges security teams face are:
- Difficulty in identifying which SaaS apps are secure and which are potentially risky.
- Having to manually analyze – app by app – and make sure these configurations are in place.
Thankfully, combining Microsoft Secure Score and Microsoft Defender for Cloud Apps will solve both problems. In the following example, we show how to successfully prevent one of the riskiest configurations in your SaaS apps – multi-factor authentication configuration.
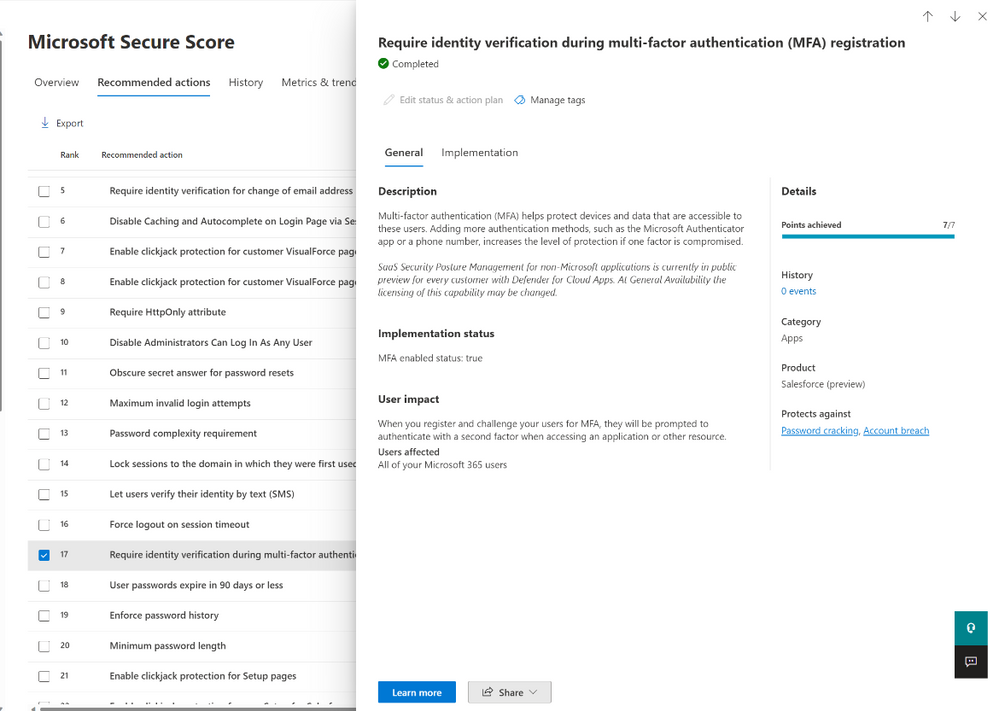
Ensure multi-factor authentication is enabled in your SaaS apps
To ensure all users have multi-factor authentication configured in your Salesforce and ServiceNow environments, you can easily check Secure Score in Microsoft 365 Defender. In Secure Score, you can review multi-factor authentication recommended actions without needing to manually check each app. Below, you can see a multi-factor authentication control in Salesforce, and if it has been enabled.
By improving app posture and taking actions to prevent such breaches, the less gaps there are in your environment. Using Secure Score & Defender for Cloud Apps data together, customers can easily remediate the potential gaps in app protection.
Detect
One of the most common cyber-attack types is business email compromise (BEC). While advanced persistent attacks (APT) are very complicated and usually focus on specific organizations, BEC attacks occur all the time and they threaten every user in every organization and can result in serious financial damage.
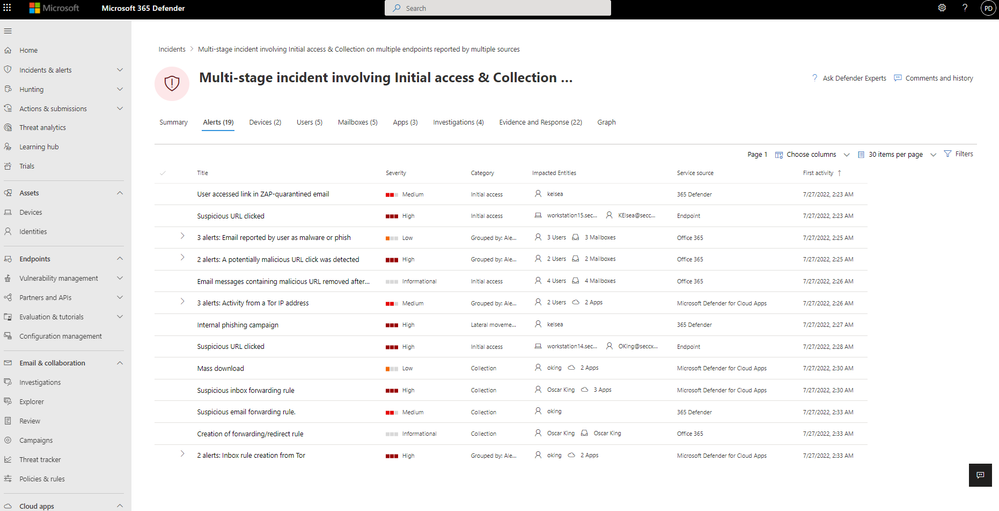
Defender for Cloud Apps with Microsoft 365 Defender provides many detection capabilities to cover different attack use cases, using signals from various products. In the following example, we’ll demonstrate how a successful BEC attack would look like from Microsoft 365 Defender, where an incident is created based on the following scenario:
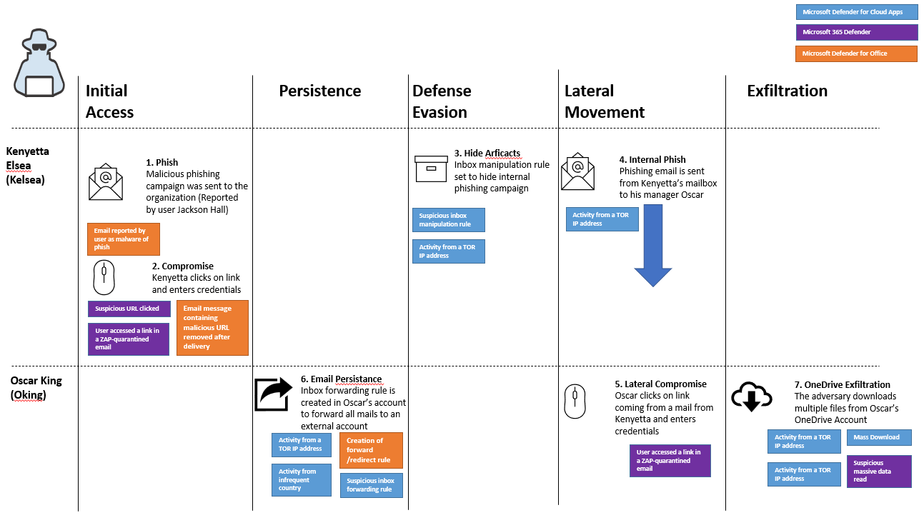
- User Kelsea:
- Initial Access - A malicious email is sent to Kelsea’s mailbox. The user clicks on the URL and enters their credentials on the phishing site.
- Lateral movement – An internal phishing campaign is started, the user Oking is also compromised.
- User Oking:
- Persistence – The adversary creates a forwarding rule to forward all incoming emails to an external address.
- Defense Evasion – The adversary creates an inbox rule to delete certain messages and hide their traces.
- Exfiltration – Multiple files are being downloaded from Oking’s OneDrive account
The scenario is demonstrated on the following kill chain diagram:
We can see that multiple alerts were triggered based on various products, where Defender for Cloud Apps anomaly detections such as “Mass download”, “Activity from infrequent country”, “Suspicious inbox manipulation rule”, “Suspicious inbox forwarding rule” and “Activity from TOR IP address,” correlate with alerts generated by Microsoft Defender for Office, Microsoft Defender for Endpoint alerts, and Microsoft 365 Defender. Each workload has alerts based on the data coming from the Defender for Cloud Apps Office 365 app connector:
By combining Defender for Cloud Apps data, visibility, and anomaly detections, together with Microsoft Defender for Office in Microsoft 365 Defender will help you detect BEC attacks in multiple vectors in the attack and gain wide coverage of the MITRE kill chain.
Respond
Defender for Cloud Apps has native response capabilities that can be automated through policies or manually implemented when responding to a threat.
Suspend user
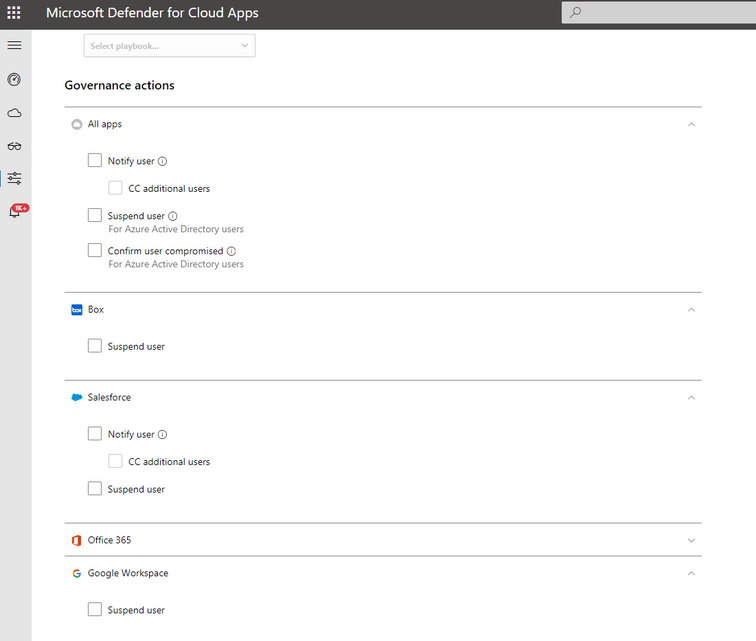
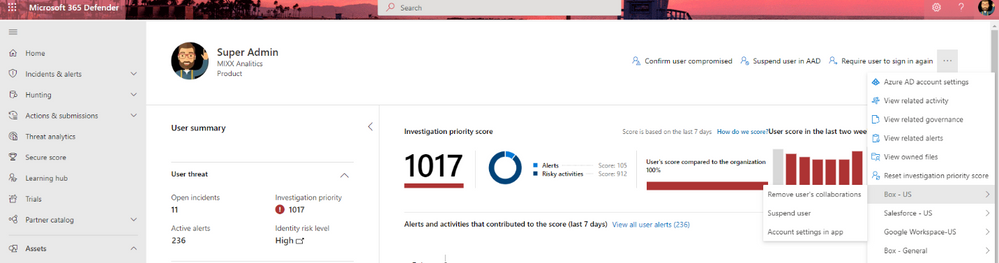
One of the most useful actions is to suspend the compromised user who triggered the alert. This will stop them from carrying out more damage and allow your SOC team to gain a broader understanding of the incident. Defender for Cloud Apps allows you to suspend Azure Active Directory (AAD) users and non-Microsoft apps users (e,g,., Box, Salesforce, and Google Workspace).
This action can be automated through the governance section in a policy configuration:
Or manually from the user’s side pane or user page in Microsoft 365 Defender:
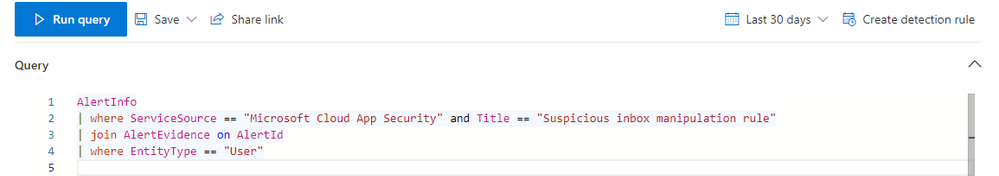
Another option is to use Microsoft 365 Defender Advanced Hunting’s custom detection rules, to create a rule that suspends the user according to a specific query. The query can be based on events from the CloudAppEvents table, or on alerts. Here is an example query:
AlertInfo
| where ServiceSource == "Microsoft Cloud App Security" and Title == "Suspicious inbox manipulation rule"
| join AlertEvidence on AlertId
| where EntityType == "User"
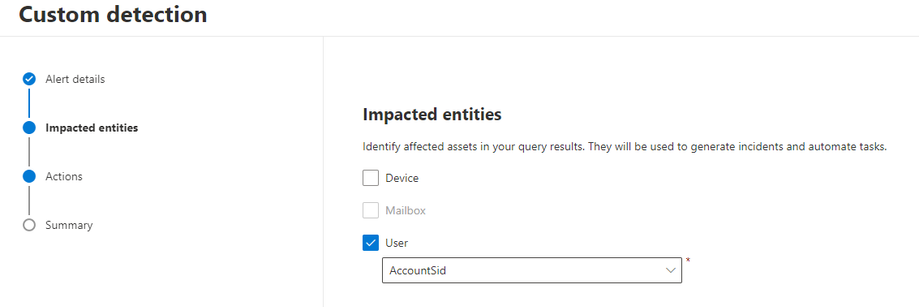
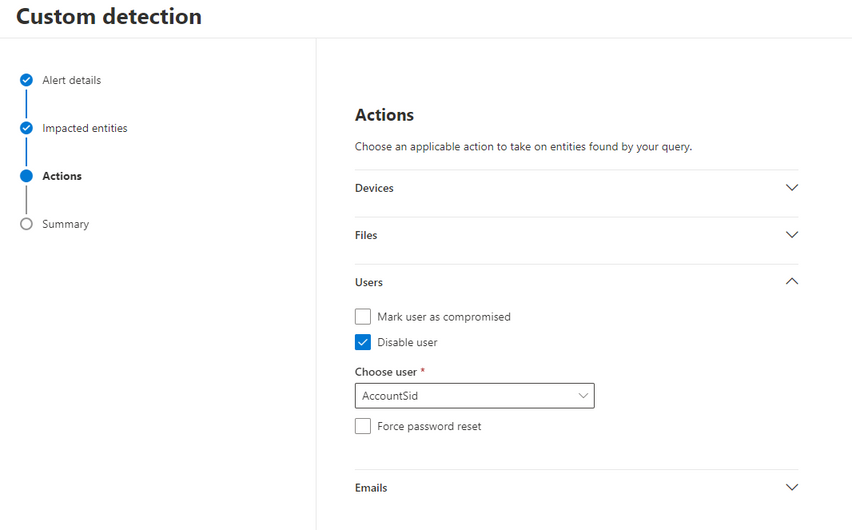
How to create a custom detection:
- Choose the user as an impacted asset:
- Disable the user:
The ability to create custom detections using data from all workloads is one of the most critical features in Microsoft 365 Defender. You can easily create any rule for you organization and take the action required to protect your data, users and assets.
Investigate
Once an alert has been triggered, the next step is to investigate and understand the scope of the breach. Microsoft 365 Defender advanced hunting provides the ability to query massive amounts of data using multiple fields within a single activity. It aggregates data and integrates information across different security workloads to create a unified experience. We will walk you through three common steps in an incident investigation.
How to start investigating
During the initial investigation, the first step is to scope down activities related to the alert, this will help create a foundation for you to build your advanced queries. This can be completed by using the button “Investigate in Activity Log” in the alert page which will redirect the user to the activity log page with the corresponding filters seen in the alert.
How to investigate a malicious user
The next step is to find the related activities performed the same user. This can provide additional information about the malicious actor and understand the user’s normal habits to determine if this is unusual behavior. Using the following query:
CloudAppEvents
| where AccountObjectId == **enter account id** and Timestamp >= startofday(datetime( **enter alert date** ))
| summarize by ActionType, CountryCode, AccountObjectId
| sort by ActionType asc
There are more specific queries depending on the specific scenario, using other Microsoft 365 Defender workloads. Examples can be found on the Threat Analytics page – for example for BEC you can see the “Recent trends in business email compromise financial fraud“ report.
How to understand the scope of breach within an organization
The final step is to understand how the breach may have affected the rest of the organization. By analyzing other activities that share similar attributes of the alert and related activities, such as same IP, may lead to other users that were inhibited by the same malicious actor. The following query can be used:
CloudAppEvents
| where IPAddress == **enter IP address ** and Timestemp >= startofday(datetime( **enter alert date** ))
Summary
Using Microsoft 365 Defender, there are various ways a customer can prevent, detect, respond and investigate threats across their security workloads. SaaS applications continue to be one of the most critical assets within an organization and together with Defender for Cloud Apps and Microsoft 365 Defender, we can provide 360 coverage for your environment.
If you would like to see additional scenarios of how Microsoft Defender for Cloud Apps & Microsoft 365 Defender work together, drop a comment below!
Resources
Get security configuration recommendations for your SaaS applications | Microsoft Docs
Business email compromise: How Microsoft is combating this costly threat - Microsoft Security Blog
Create and manage custom detection rules in Microsoft 365 Defender | Microsoft Docs
Published on:
Learn more