Confidential VM option for Azure Databricks Preview

Azure Databricks & Azure Confidential Computing are excited to announce the Public Preview of Azure Databricks support for Azure Confidential Computing options for data plane.
Feature Overview
Azure Databricks now supports using Confidential computing VM options while creating clusters. This new feature emphasizes our commitment to cloud security. With this new feature, now you can run your Azure Databricks workload securely & confidentially on Azure. Azure confidential computing generally attracts customers in highly regulated industries & regions but is equally applicable to any business that is looking to run their analytics, machine learning and other workloads in a privacy preserving way.
Security Benefits
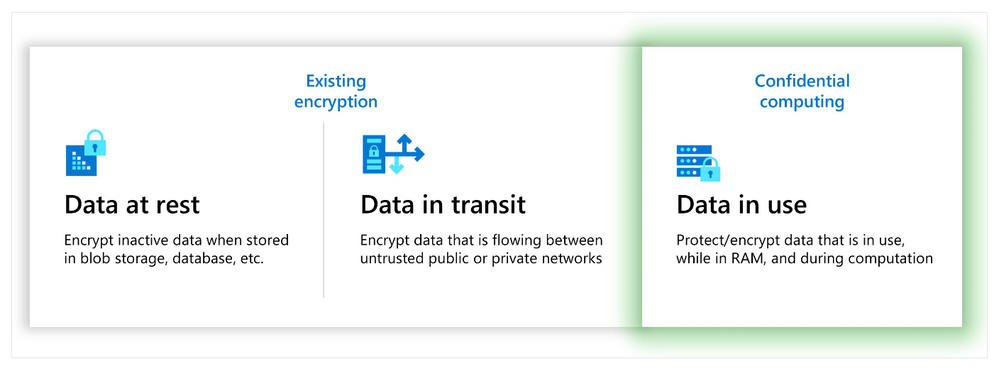
Azure already encrypts data at rest and in transit, and confidential computing helps protect data in use, including the cryptographic keys. Azure confidential computing helps customers prevent unauthorized access to data in use, including from the cloud operator, by processing data in a hardware-based and attested Trusted Execution Environment (TEE).
ACC Technology & Offerings
Please start here to understand the technology behind Azure Confidential Computing in depth and also learn about the GA and in-preview offerings.
Azure confidential computing | Microsoft Learn
Supported VM Types for Confidential Databricks Data Plane
Please read this article to find out the DC* & EC* series VM types supported in the new feature release.
Azure Confidential virtual machine options on AMD processors | Microsoft Learn
Current Limitations
The feature release allows adding Confidential VM options while creating clusters in the customer Data plane only. More confidential features will be coming soon.
Configuring Confidential VMs on Azure Databricks
When creating a data plane cluster, select one of the confidential VM options as discussed here. By selecting a confidential VM as the compute option, you would be able to run your workloads in a privacy preserving way & confidential manner. Confidential VMs are available currently in East US, West US, North EU, West EU, with additional regions to be added later.
How to create a Confidential Data plane cluster - https://aka.ms/ADB-ACC-demo
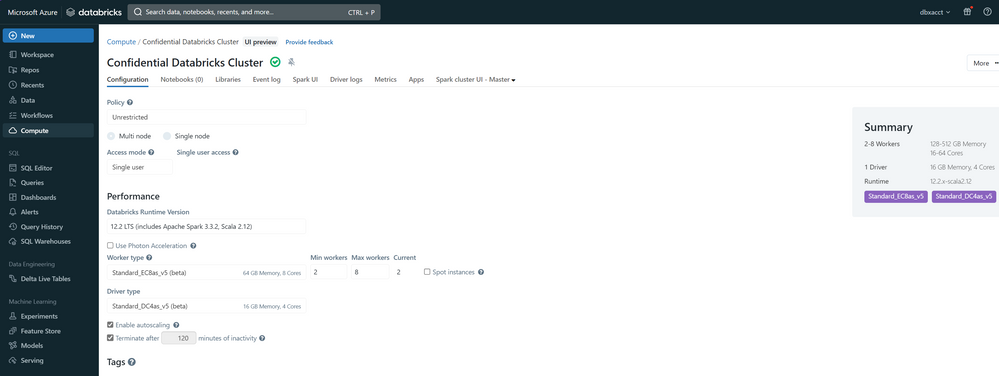
Note: To migrate existing clusters to Confidential compute, simply edit the cluster and select the VM type as discussed above.
Published on:
Learn moreRelated posts
New Secure Boot update resources for Azure Virtual Desktop, Windows 365, and Microsoft Intune
New documentation is now available to help IT administrators prepare for Secure Boot certificate updates and manage update readiness across vi...
Azure DocumentDB: A Fully Managed MongoDB-Compatible Database
Running MongoDB at scale eventually forces a trade-off: invest heavily in managing your own infrastructure or move to a managed service and ri...
Azure SDK Release (February 2026)
Azure SDK releases every month. In this post, you'll find this month's highlights and release notes. The post Azure SDK Release (February 2026...
Recovering dropped tables in Azure Databricks with UNDROP TABLE
Oops, Dropped the Wrong Table? What now? We’ve all been there: you’re cleaning up some old stuff in Databricks, run a quick DROP TABLE… and su...
Azure Developer CLI (azd) – February 2026: JMESPath Queries & Deployment Slots
This post announces the February 2026 release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) – February 2026: JM...
Improved Python (PyPi/uvx) support in Azure MCP Server
Azure MCP Server now offers first-class Python support via PyPI and uvx, making it easier than ever for Python developers to integrate Azure i...
Microsoft Purview: Data Lifecycle Management- Azure PST Import
Azure PST Import is a migration method that enables PST files stored in Azure Blob Storage to be imported directly into Exchange Online mailbo...