Apply CIS compliant Azure Security baselines through Azure Automanage!
We are thrilled to announce that Azure Automanage Machine Best Practices now enables you to apply CIS aligned Azure security baselines through Automanage Machine Configuration.
Azure Automanage Machine Best Practices is a consolidated management solution that simplifies daily server management through effortless automation by handling the initial setup and configuration of Azure best practice services. Automanage continuously monitors machines across their entire lifecycle, automatically bringing them back into conformance should they drift from the desired state. And the best part - Automanage machine best practices is generally available and free to use! You only pay for the services you enable, just as you would if you were doing it all manually, without any additional cost.
Azure has released a new Windows server security benchmark that is fully compliant with the newly released CIS Azure Compute Microsoft Windows Server 2019 Benchmark. Working in partnership with CIS, this new compute benchmark includes cloud-specific security controls and removes non-applicable controls that have no significant risk impact in cloud environment.
What’s new for Azure Automanage machine best practices and server security baselines
Using Automanage Machine Best Practices, you can now apply the CIS compliant Windows baselines by leveraging the Automanage Machine Configuration offering. Machine Configuration is a key service that you can enable on your Azure Virtual Machines and Arc-enabled servers through an Automanage configuration profile. Just as Machine Best Practices lets customers describe desired state for management services, Machine Configuration provides the same functionality within the actual resources, by auditing or configuring operating system settings as code. When you select Machine Configuration in your configuration profile, Machine Configuration will automatically apply Azure Windows security baseline settings*.
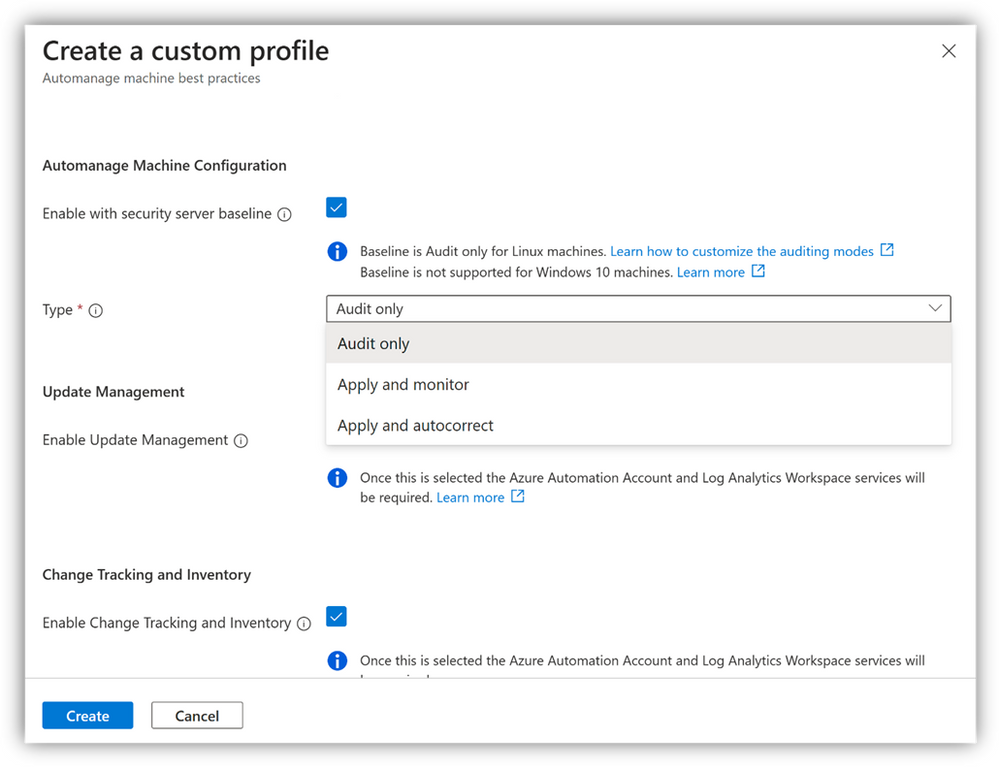
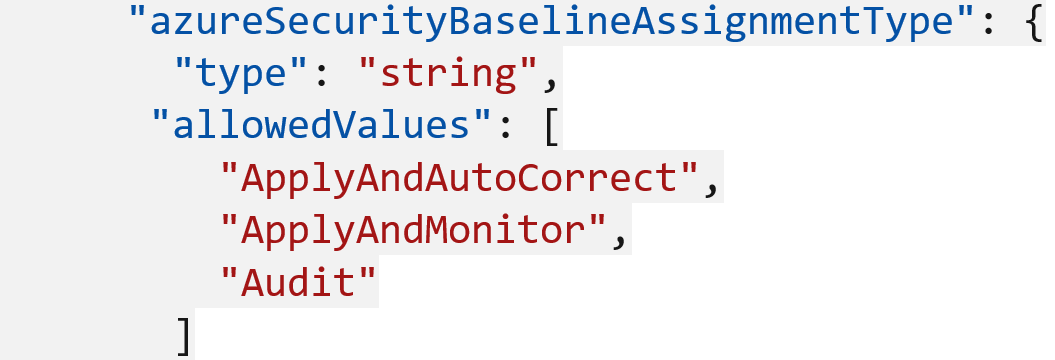
Machine Configuration can deliver changes within a machine in three different ways. This can be done by assigning the following modes as a parameter of machine configuration definitions that support the policy effect DeployIfNotExists (DINE) -
- Audit - This mode reports the current state of the machine but does not implement any change.
- Apply and monitor - This mode applies the recommended change to the machine once and then monitors it for deflections. If the configuration becomes non-compliant at any time, a manual remediation needs to be triggered to make any change.
- Apply and autocorrect - This mode applies the changes to the machine. If there is a deflection, the local service within the machine corrects it at the next evaluation.
These modes can be assigned through the Automanage Portal experience here (details in the Get started section below) or through an ARM template.
Get started
Let’s dive deeper and show you how to get started:
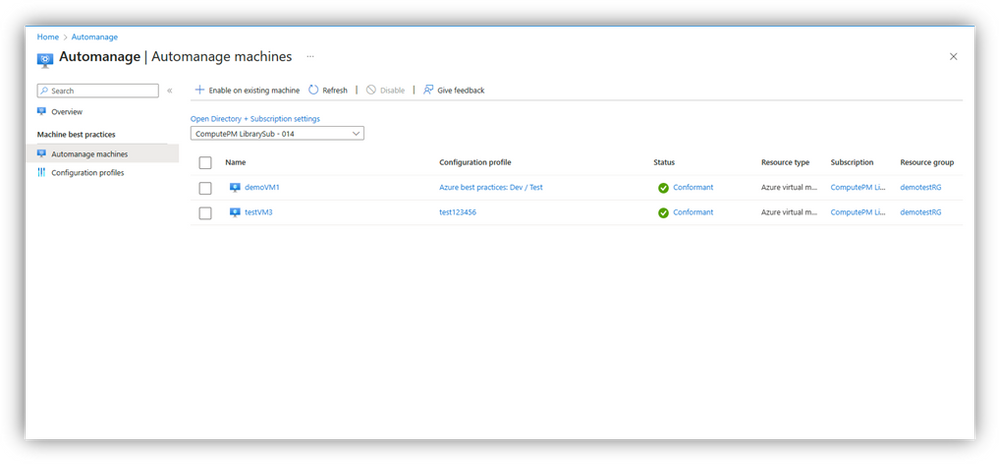
- To enable Azure Automanage for servers in Azure and Arc-enabled servers, start by browsing to the Automanage portal and click “Enable on existing machine”.
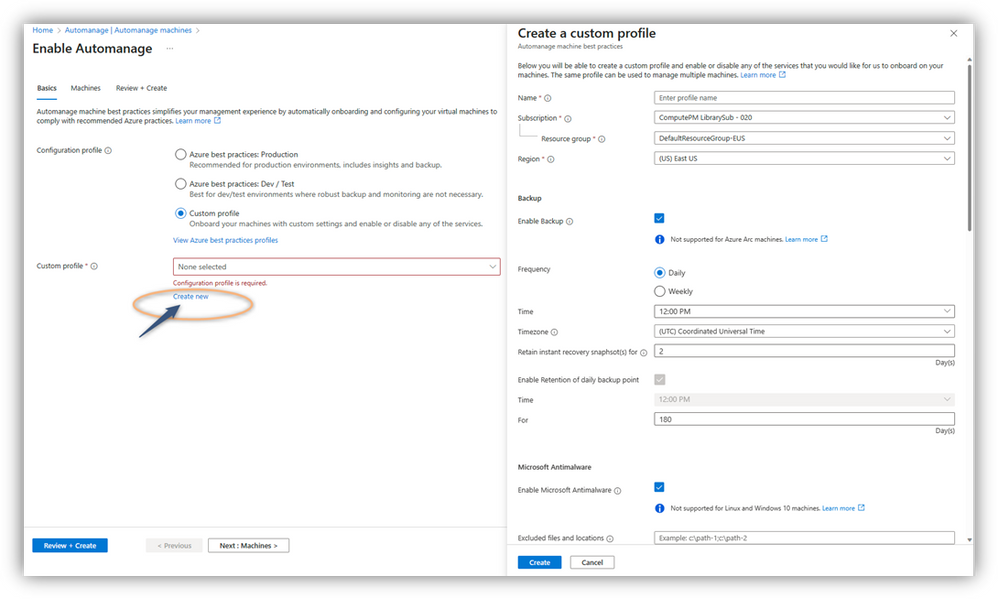
- Then create a custom configuration profile in the Configuration profile selection option.
- Enable the Machine Configuration service in the custom configuration profile and select the Assignment type/mode of your choice.
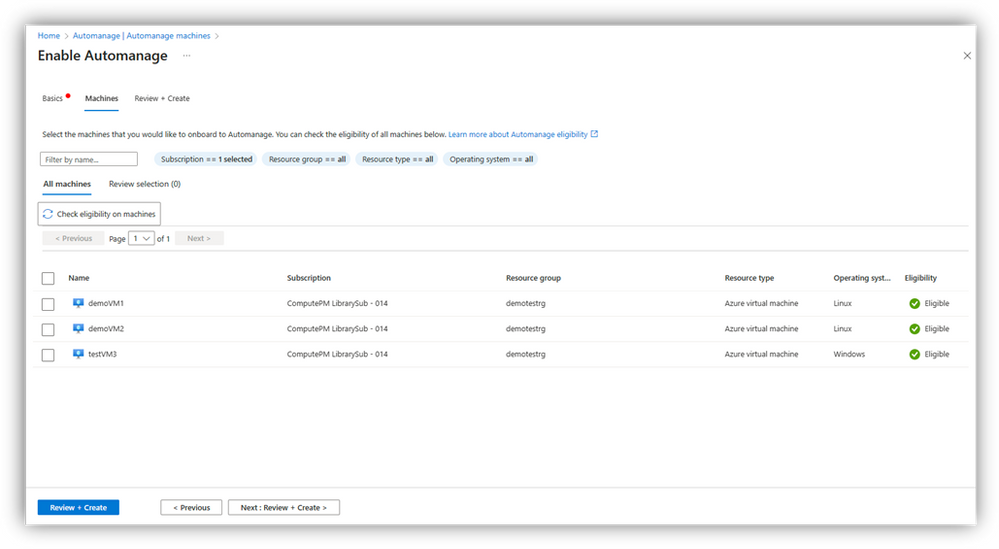
- After you choose/create your profile, select the Azure virtual machines and/or Arc-enabled servers that you want your custom profile applied to.
- Once you have selected the machines, you can click on “Review + Create”. This will initiate the Configuration profile assignment process. Automanage has now configured your machines with the best practices services. You can click on the status column to get the latest Automanage status report for your machines.
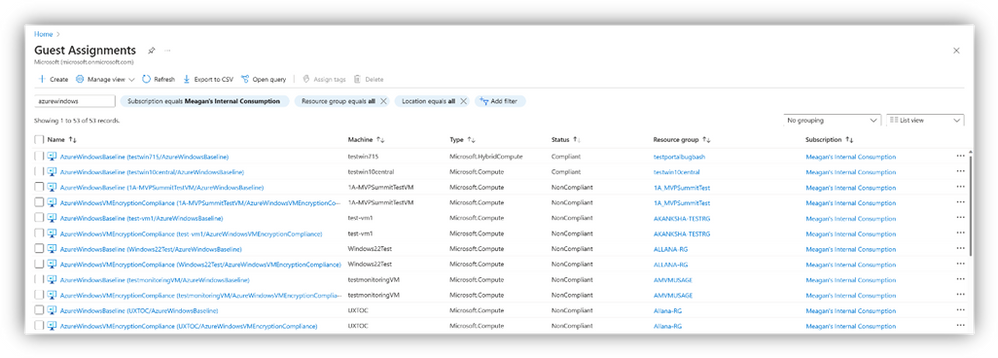
- You can query the compliance status for your entire environment using the Guest Assignments page in the Azure Portal, and through the Machine Configuration menu item within the Arc-enabled servers table of contents.
Through Guest Assignments:
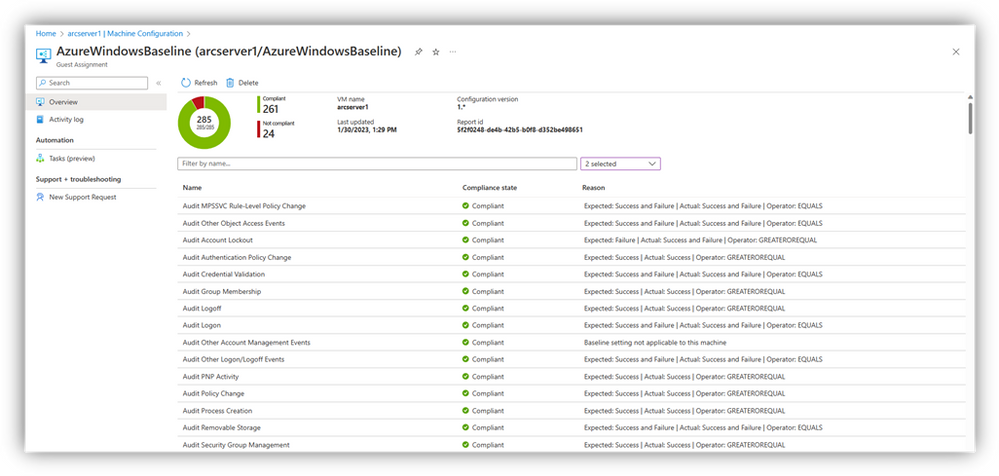
Through the Guest Assignments view for Azure VMs and Arc-enabled servers, you can see all the configuration details for the selected subscriptions. At a high level, you are able to glance at the compliance across your environment.
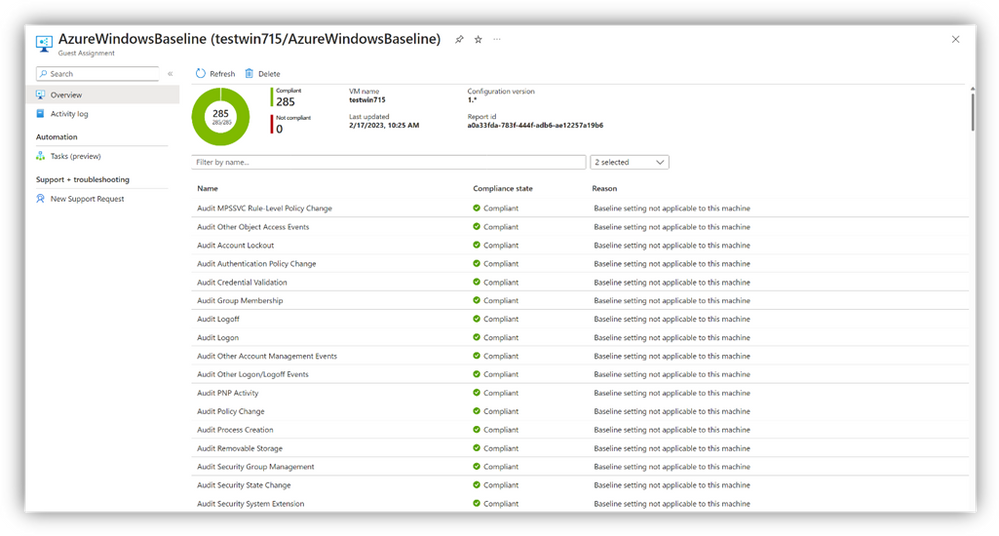
Through clicking into an individual Guest Assignment, you can see a breakdown of this compliance on a per-rule basis as well as some additional context for the reasons for non-compliance.
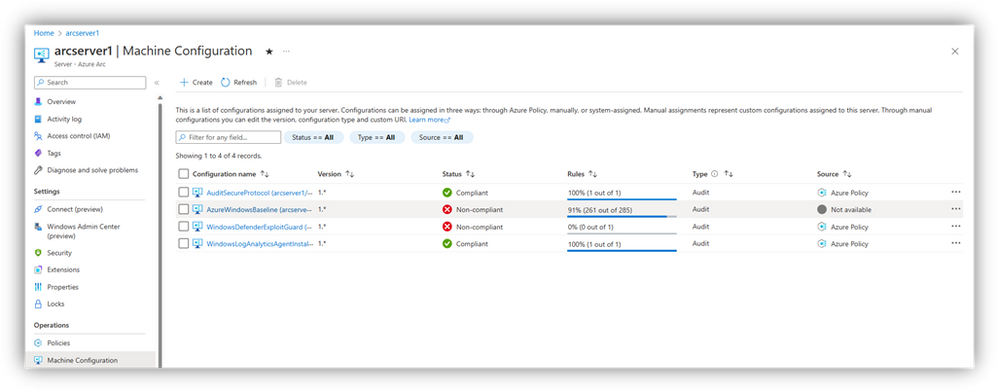
Through Arc-enabled servers Table of Contents:
This view is only for non-Azure machines – here you can see all the compliance across your Arc-enabled servers.
Clicking into an individual entry links to a Guest Assignment, showing you the breakdown of this compliance on a per-rule basis and reasons for non-compliance.
Voila! With Azure Automanage, now you can just point and click to apply CIS compliant Azure Security baselines to your environment and view its compliance.
*Note: The Windows and Linux security baselines can be applied independently of Azure Automanage. The Linux security baseline is in private preview right now.
Related Resources
To keep learning about the exciting new capabilities of Azure Automanage:
- Get started with Azure Automanage | Microsoft Azure
- Learn more about Automanage machine best practices
- Learn more about Automanage machine configuration
Published on:
Learn moreRelated posts
Announcing Azure MCP Server 1.0.0 Stable Release – A New Era for Agentic Workflows
Today marks a major milestone for agentic development on Azure: the stable release of the Azure MCP Server 1.0! The post Announcing Azure MCP ...
From Backup to Discovery: Veeam’s Search Engine Powered by Azure Cosmos DB
This article was co-authored by Zack Rossman, Staff Software Engineer, Veeam; Ashlie Martinez, Staff Software Engineer, Veeam; and James Nguye...
Azure SDK Release (October 2025)
Azure SDK releases every month. In this post, you'll find this month's highlights and release notes. The post Azure SDK Release (October 2025)...
Microsoft Copilot (Microsoft 365): [Copilot Extensibility] No-Code Publishing for Azure AI Foundry Agents to Microsoft 365 Copilot Agent Store
Developers can now publish Azure AI Foundry Agents directly to the Microsoft 365 Copilot Agent Store with a simplified, no-code experience. Pr...
Azure Marketplace and AppSource: A Unified AI Apps and Agents Marketplace
The Microsoft AI Apps and Agents Marketplace is set to transform how businesses discover, purchase, and deploy AI-powered solutions. This new ...
Episode 413 – Simplifying Azure Files with a new file share-centric management model
Welcome to Episode 413 of the Microsoft Cloud IT Pro Podcast. Microsoft has introduced a new file share-centric management model for Azure Fil...
Bringing Context to Copilot: Azure Cosmos DB Best Practices, Right in Your VS Code Workspace
Developers love GitHub Copilot for its instant, intelligent code suggestions. But what if those suggestions could also reflect your specific d...
Build an AI Agentic RAG search application with React, SQL Azure and Azure Static Web Apps
Introduction Leveraging OpenAI for semantic searches on structured databases like Azure SQL enhances search accuracy and context-awareness, pr...
Announcing latest Azure Cosmos DB Python SDK: Powering the Future of AI with OpenAI
We’re thrilled to announce the stable release of Azure Cosmos DB Python SDK version 4.14.0! This release brings together months of innov...