Security and ransomware protection with Azure Backup

Ransomware attacks can cause significant damage to organizations and individuals, including data loss, security breaches, and costly business disruptions. When successful, they can disable a business’ core IT infrastructure, and cause destruction that could have a debilitating impact on the physical, economic security or safety of a business. And unfortunately, over the last few years, the number of ransomware attacks have seen a significant growth in their numbers as well as their sophistication. Having a sound BCDR strategy in place is essential to meeting your overall goals when it comes to ensuring security against ransomware attacks and minimizing their possible impact on your business. To make sure all customers are well protected against such attacks, Azure Backup provides a host of capabilities, some built-in while others optional, that significantly improve the security of your backups. In this article, we discuss some such capabilities offered by Azure Backup that can help you prepare better to recover from ransomware attacks as well as other data loss scenarios. As we shall see, these primarily revolve around:
- Controlling who can access your backups
- Ensuring appropriate data protection measures for your backups
- Performing and storing backups securely
- Monitoring and assessing the security of your backups
Controlling who can access your backups
Making sure that all users have access to only perform actions required to just do their jobs is essentially the first and an obvious step to reduce the risk of overexposing access. This, in turn, significantly reduces the chances of malicious as well accidental destructive actions on your backups. Azure Backup and Azure Site Recovery provide multiple ways to do this, such as, through use of proper RBAC roles and controlling access to Azure.
Use RBAC for fine grained access management
Recovery services vaults and Backup vaults allow you to manage fine-grained access to all personnel who need to interact with your backups in different capacities. Assigning RBAC roles effectively also means that there exists proper isolation between admins managing BCDR data and admins managing production workloads. You can use the built-in RBAC roles as well as create custom roles, per your requirements. Read more about RBAC roles for Azure Backup here.
Leverage identity management security features
Azure Active Directory provides a host of security features that can help authenticate and manage the access to Azure resources centrally. Hence, enabling capabilities such as multi-factor authentication can help you ensure that users are who they claim to be when they access your backups and other resources. Read more about Azure Identity management solutions here.
Isolation of backup data
While your vaults are in subscriptions, the actual vaulted backup data is always stored in dedicated subscriptions managed by Microsoft. This ensures that the only way to access the data is through the vault, thereby reducing the chances of any direct tampering with your backup data in the event of a compromise in your production environment.
Ensuring appropriate data protection measures for your backups
Azure Backup provides various capabilities that can help you add additional layers of security to your backup data.
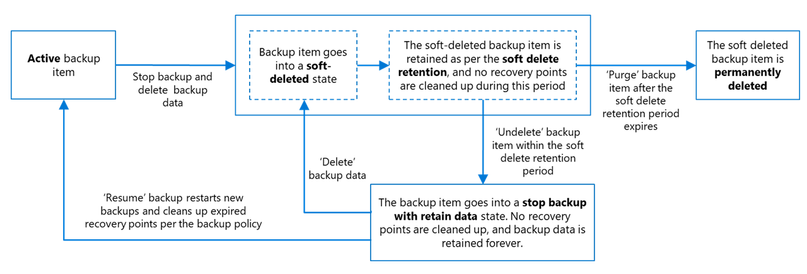
Enable soft delete for your vaults
Enabling soft delete provides you a chance to recover your data even after it has been deleted by retaining it additionally for a specified duration. Soft delete also allows you to make it ‘always-on’, which means, once enabled it cannot be disabled, thereby protecting your backups from malicious actors intending to forcibly disable soft delete while attempting to delete backups. By default all new vaults have soft delete enabled with a soft delete retention of 14 days. You can choose to make it ‘always on’, change the soft delete retention or disable it per your requirements. Read more about soft delete here.
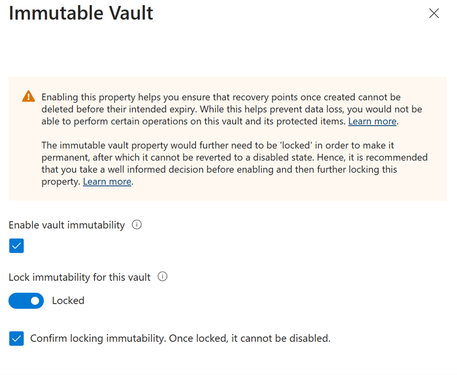
Enable immutable vaults
While Azure Backup provides backup administrators complete control over management of backup data, in the event of a compromise this may lead to attempts to delete backups.
Immutable vaults help protect your backups from any operations that could lead to loss of backups such as deleting backups or reducing retention of backup policies. This means any recovery points once created will be retained at least for the retention defined by your backup policies. Furthermore, you can try out immutability for your vaults before you proceed to lock it, which will make it irreversible and prevent any malicious actors from disabling it. Learn more about immutable vaults for Azure Backup here.
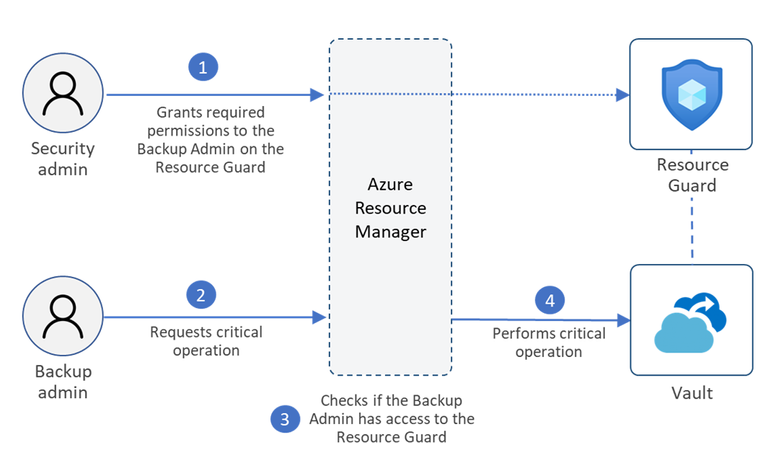
Multi-user authorization using Resource Guard
While locking immutability on vaults provides the highest levels of protection for your backup data, it restricts any actions that can lead to deletion of recovery points (such as reducing retentions and deleting backups). If you require the ability to be able to perform such critical operations, albeit with an additional layer of security, multi-user authorization for Backup (MUA) might be able to help. MUA uses another resource called the Resource Guard, which is owned by a user other than the backup administrator. So in order to be able to perform a backup management operation protected by the resource guard, the backup admin must first get access to the resource guard. Read more about MUA for Backup here.
Performing and storing backups securely
Your backup data is always encrypted at rest using industry-standard encryption measures. During data transfer, all the data is transferred over secure TLS protocols with alternatives to prevent disruptions to your network security rules.
Encryption at rest
Backup, by default, encrypts your data at rest using Microsoft-managed keys. However, you can also use your keys stored in the Azure Key Vault to encrypt your backups. Moreover, you can also back up encrypted resources like virtual machines encrypted using ADE and SQL databases encrypted using TDE. Learn more about encryption in Azure Backup here.
Network security with Azure Backup
Azure Backup provides ways to minimize any changes on your existing network security setup in order to run your backups. Backup of Azure virtual machines, for example, takes place entirely over the Azure backbone network via the VM host, hence, it does not require you to make any exceptions to your network firewall rules just to make your backups work. For backup of workloads like SAP HANA and SQL servers running inside your Azure VMs, and MARS agent backups, you can use private endpoints use private IPs in your virtual networks for backups. Learn more about private endpoints for Backup here.
Monitoring and assessing the security of your backups
While Azure Backup provides a variety of capabilities to help you protect your backups better and in ways to suit your requirements, it is essential that you leverage them as much as possible. This is where the BCDR security posture can help you take stock of the security of your backups, as well as guides you on how to improve it.
BCDR security posture
BCDR security posture allows you to assess the security of your BCDR data across your estate in terms of how well it is poised to help you recover from any ransomware attacks that may require to rely on your backup systems. To do this, Backup classifies the security of your protected resources into security levels ‘Excellent’, ‘Good’, ‘Fair’ and ‘Poor’, which in turn are determined by the state of these security settings on your vaults- immutable vaults, soft delete and multi-user authorization.
The security levels are described as follows:
- Excellent: All backups are protected against accidental deletion and ransomware attacks. To achieve excellent security, following conditions must be true.
- Either immutability or soft-delete vault setting must be enabled and irreversible (locked/always-on).
- Multi-user authorization (MUA) must be enabled on the vault.
- Good: Existing backups are protected against accidental deletions and offer better chances of data recovery. To achieve good security, either immutability with lock or soft-delete must be enabled.
- Fair: All critical backup operations will have an additional layer of protection. To achieve fair security, MUA must be enabled on the vault.
- Poor: Neither advanced protection capability is enabled, nor only reversible capabilities are enabled. Poor security can only provide protection against accidental deletions.
Improving the state of the aforementioned security settings of the vault can help improve the security levels of the corresponding items.
Learn more about BCDR security posture here.
Published on:
Learn moreRelated posts
Announcing GPT 5.2 Availability in Azure for U.S. Government Secret and Top Secret Clouds
Today, we are excited to announce that GPT-5.2, Azure OpenAI’s newest frontier reasoning model, is available in Microsoft Azure for U.S. Gover...
Sync data from Dynamics 365 Finance & Operations Azure SQL Database (Tier2) to local SQL Server (AxDB)
A new utility to synchronize data from D365FO cloud environments to local AxDB, featuring incremental sync and smart strategies.
Azure Cosmos DB Conf 2026 — Call for Proposals Is Now Open
Every production system has a story behind it. The scaling limit you didn’t expect. The data model that finally clicked. The tradeoff you had ...
Powering Real-Time Gaming Experiences with Azure Cosmos DB for NoSQL
Scenario: When Every Millisecond Counts in Gaming Imagine millions of players logging in at the exact moment a new game season launches. Leade...
Access Azure Virtual Desktop and Windows 365 Cloud PC from non-managed devices
Check out this article via web browser: Access Azure Virtual Desktop and Windows 365 Cloud PC from non-managed devices Many organizations use ...
Power Pages + Azure AD B2C: “The Provided Application Is Not Valid” Error
If you are new to configuring Azure AD B2C as Identity Provider in Power Pages, refer Power Pages : Set up Azure AD B2C After completing the s...