Leveraging the convergence of Microsoft Defender for Identity in Microsoft 365 Defender Portal

The Microsoft Defender for Identity portal experience and functionality have been converged into Microsoft’s extended detection and response (XDR) platform, Microsoft 365 Defender. Converging core elements of the legacy Defender for Identity portal into our XDR platform experience you are better able to pair the advanced identity threat detection and investigation capabilities with other security workloads to maximize not only their identity protection but also deliver a more comprehensive security posture.
In this blog post, we explore the remarkable advantages this convergence brings, and guide you through the new ways you can access some of the core elements of the old Identity experience.
One of the most important elements of Microsoft Defender for Identity is the prioritized view of all identity alerts. With the new experience, Microsoft 365 Defender automatically correlates these alerts with information with telemetry from across your Microsoft 365 security. The incident level visibility helps spot the increasingly sophisticated, cross-domain strategies attackers better than siloed alerts and signals.
If you do only want to see Identity related alerts you can select Defender for Identity within the filters at the top of the page to see identity-based incidents and alerts from the last 180 days. While investigating an alert, you benefit from the broader platform integration and can link alert to incident or further tune it. Alert tuning rules provide the ability to create complex exclusion rules that are not available via the exclusion feature. When drilling down into the alert, you can view the alert story which provides important information to help you understand the detected threats. By managing the alert, you can change its status, assign it to a specific persona, and classify it.
From the alert, you can also pivot to the impacted identity page to gather additional information and take remediation actions.
Figure 1: Microsoft Defender for Identity alert page
The Microsoft 365 Defender identity page provides necessary tools and insights to investigate user behavior, detect anomalies, and respond effectively to identity-related security incidents from the different available workloads. There, you can find information such as the Azure Active Directory Identity risk level, organization tree, user accounts, tags, Active Directory control flags, and more. Through the new user page, you can respond to compromised users by disabling their accounts or resetting their passwords. After taking actions on users, you can check the activity details in the action center.
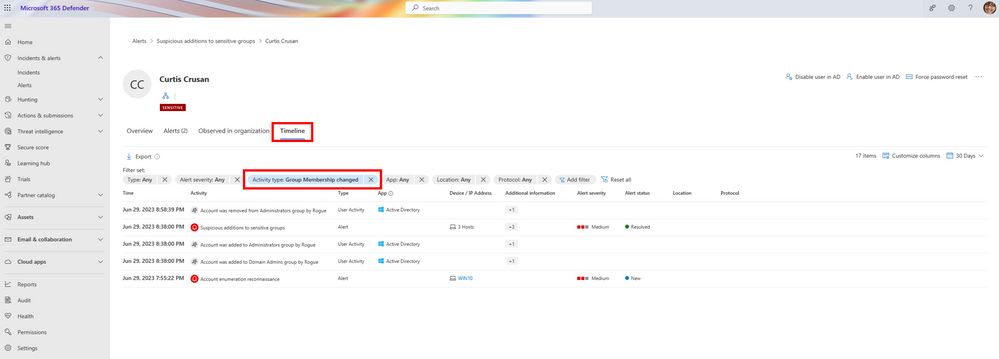
In addition, you can use the unified Identity Timeline, which displays a chronological view of user activities and alerts as it consolidates the user's identity activities across identity workloads such as Microsoft Defender for Identity, Microsoft Defender for Cloud Apps, and Microsoft Defender for Endpoint. The timeline allows you to track the user's activities over time to identify notable or suspicious items and then further investigate with various filters and important information about each activity and alert.
Figure 2: Identity timeline in Microsoft 365 Defender portal
If you observe abnormal activity, you can pivot to the Advanced hunting view within Microsoft 365 Defender to query additional sources for information on advanced threats. Using these queries, you can search through vast amounts of data in a single pane of glass allowing a quick view critical information from across different deployed products.
For example, in the updated IdentityInfo table, we provide account information (such as the roles assigned to the account) from various sources, including Azure Active Directory. The query below detects Defender for Identity logins which involves a sensitive user account.
Additionally, while working with Advanced hunting, you can create custom detection rules that automatically trigger alerts as well as response actions. This proactive monitoring and response capability helps you stay ahead of various events and system states.
The Identities tab in the Microsoft 365 Defender settings page provides a variety of information about your workspace and allows you to adjust environment settings. For example, you can apply entity tags to sensitive or honeytoken accounts, configure detection exclusions to help Microsoft Defender for Identity ignore specific entities and reduce false positive alerts, manage action and directory service accounts for specific users to perform remediation actions, define alert notifications, and more. In the next coming weeks additional functionality from Microsoft Defender for Identity will also be gradually released including the reports feature. This capability will allow customers to either download reports immediately or schedule a report be delivered periodically via email through Microsoft 365 Defender portal.
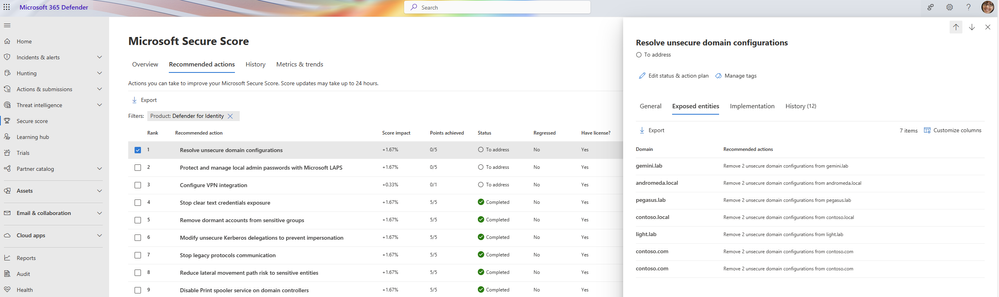
Identity related security posture assessments are also available within Microsoft 365 Defender. These assessments proactively identify potential identity risks and help reduce overall attack surface and can be accessed through the Secure Score recommended actions section within Microsoft 365 Defender and filtering on Defender for Identity. We continually update our recommendations and release new reports and assessments based on the latest strategies so check back often to ensure you have the latest protections in place.
Figure 3: Microsoft Defender for Identity's security posture assessments
Thank you to all our customers for your continued support, suggestions, and feedback throughout this entire process. We will continue to work on improving your experience and provide you with the solutions you need to detect, investigate, and respond to identity-based attacks and threats in real time.
Check out our updated documentation to learn more about the Microsoft Defender for Identity user experiences available within the Microsoft 365 Defender portal and follow the What’s New page to stay updated with new releases.
Published on:
Learn moreRelated posts
Open Word, Excel, and PowerPoint Files in Microsoft 365 Copilot Chat
Starting early February 2026, Word, Excel, and PowerPoint files cited in Microsoft 365 Copilot Chat (web) will open directly within the chat i...
Drawn electronic signatures with eSignature for Microsoft 365
eSignature for Microsoft 365 will add a drawn signature option for signing PDFs, allowing use of stylus, touch, or mouse. Rolling out worldwid...
Viva Glint: Teams notifications now support user language preferences
Viva Glint notifications in Microsoft Teams will now appear in each user’s configured language instead of the tenant default, starting mid-Feb...
Microsoft Copilot (Microsoft 365): Copilot connectors are available for U.S. Department of Defense environment
Copilot connectors enable organizations to integrate content from other external data sources into Microsoft Graph, improving Copilot’s intell...
Microsoft 365: New map-based room booking experience in Places Finder
We are enhancing the room booking experience in the new calendar experience across Outlook for Windows, Outlook for the web, and Teams by intr...
Microsoft Teams: People Skills on the profile card expanding to Teams
Access to People Skills on the Microsoft 365 profile card is expanding to Microsoft Teams. With this update, employees will be able to view sk...
Microsoft 365: New profile cards for buildings, rooms and desks
Buildings, rooms and desks that are added to the Places directory will have new profile cards, accessible from Copilot Chat and across other M...
Microsoft Copilot (Microsoft 365): Microsoft Copilot (Microsoft 365): Open Word, Excel, and PowerPoint Files in Copilot Chat
Currently, clicking on cited content in Copilot opens files outside of Copilot. With this new feature, content can be opened directly in Copil...
Integrating Virtual Tables with Power Pages – Step by Step Guide
What Are Virtual Tables (Quick Context) Virtual tables allow Dataverse to read/write data from external systems without storing the data in Da...