Announcing: Microsoft moves $25 Billion in credit card transactions to Azure confidential computing

Microsoft is proud to showcase that customers in the financial sector can rely on public Azure to add confidentiality to provide secure and compliant payment solutions that meet or exceed industry standards.
Financial sector customers are very discerning about which workloads they move into the cloud. Given the high bar for data privacy, sovereignty, and security, it is not surprising that these same customers favor hybrid cloud solutions over moving everything to a public cloud. Among the areas traditionally guarded and reserved for “on-premises deployment” are confidential cryptographic keys, their operation, storage, and rotation. Traditionally, this material is protected through dedicated Hardware Security Modules (HSM), specialized hardware designed to prevent private key operations from being accessible by privileged operating system processes as well as types of radio frequency snooping. Using these devices allows for the in-memory private key operations to be protected and avoid leakage in memory crash dumps. These services, the HSMs, and the corresponding infrastructure and encrypted data storage, are often the last components to move into the public cloud.
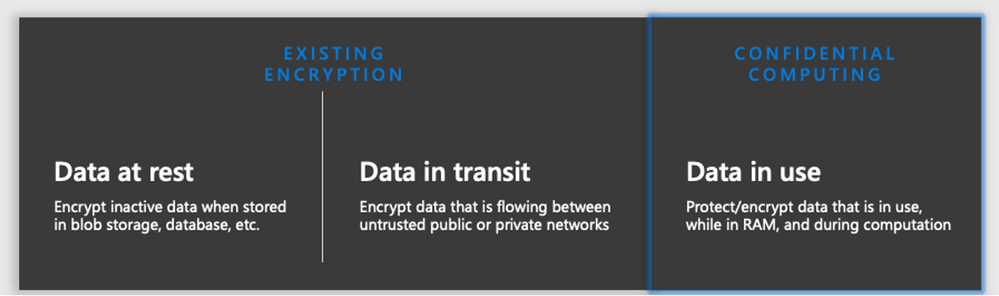
Microsoft’s solutions in this space provide industry-leading capabilities for migration and hosting confidential workloads, in the cloud, through the combined use of Azure confidential computing (ACC) infrastructure and Azure Key Vault’s Managed HSM (mHSM), which uses Intel SGX VMs with application enclaves and FIPS 140-2 L3 certified HSMs. What HSMs provide in the manner of private key protection, confidential computing offers for app process level isolation via Intel SGX and whole-VM isolation via AMD SEV-SNP using processor level memory encryption available on select Azure VM SKUs. This confidentiality solution provides the protection of data in-use by processing data in a hardware-based, attested Trusted Execution Environment (TEE) – adding to existing platform capabilities of encryption in-transit, and at-rest. These products help enable even the most security sensitive workloads to be safely deployed in public Azure, without the need for sovereign, dedicated, or hybrid on-prem cloud solutions.
Microsoft Trusts Azure for hosting Payment Instrument Data
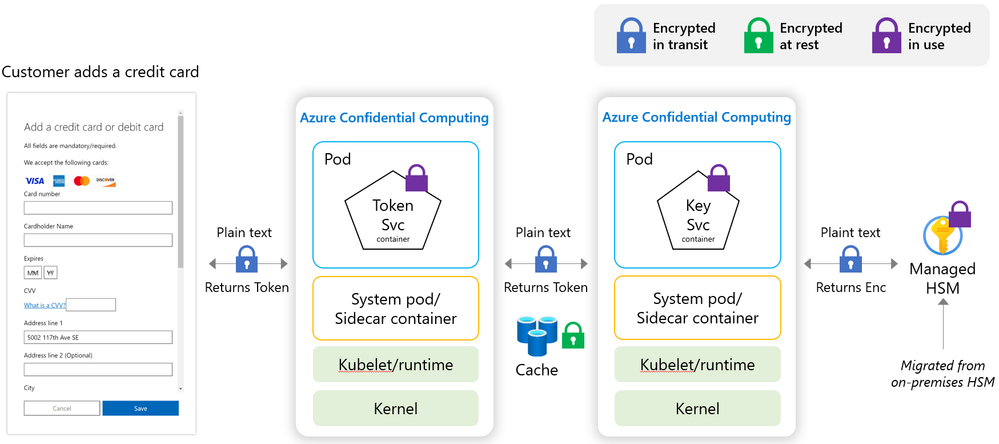
Microsoft is committed to hosting 100% of our payment services on Azure, just as we would expect our customers to do. Microsoft’s Commerce Financial Services (CFS) has completed a critical milestone by deploying a level 1 Payment Card Industry Data Security Standard (PCI-DSS) compliant credit card processing and vaulting solution, moving $25 Billion in annual credit card transactions to the public Azure cloud. The solution involves a novel implementation of ACC and mHSM in a payment service. Pioneering how to do secure payments processing in the public cloud, this approach brings compute confidentiality to the payment solution space by ensuring that payment instruments AND the private key material used to protect them are always encrypted and protected in-use. The solution is built on top of existing Azure enterprise technologies such as Azure Firewall Premium, Azure Kubernetes (AKS), and Microsoft Entra ID.
Microsoft’s solution meets or exceeds the current PCI-DSS standards for data and access protection, successfully implementing the capabilities offered by Azure confidential computing VMs with Intel SGX application enclaves running as node pools on AKS, and Managed HSMs which provide a cloud-native, hardware-backed HSM solution for protecting sensitive cryptographic key operations. Keys from an existing on-premises HSM were successfully migrated using a supported “bring your own key” (BYOK) method. Lastly, the interaction of SGX app enclave node pools running on AKS with mHSM is further secured through the use of private endpoints and Entra ID. These design elements ensure the highest degree of data security and privacy of the sensitive material customers trust Microsoft to safeguard, and it was done in the public Azure cloud.
The solution is storage technology agnostic, as it relies on the encryption of payment instrument data prior to persistence in either cache or long-term storage and does not require expensive Payment HSMs. Security and Payment Architects can utilize storage technologies without dependency on managing encryption at the data or storage layers.
For more information on the products involved in this solution, refer to:
- Azure Confidential Computing – Protect Data In Use | Microsoft Azure
- Azure Managed HSM Overview - Azure Managed HSM | Microsoft Learn
- How to generate and transfer HSM-protected keys for Azure Key Vault Managed HSM - Azure Key Vault | Microsoft Learn
- How to choose the right key management solution - How to choose between Azure Key Vault, Azure Managed HSM, Azure Dedicated HSM, and Azure Payment HSM | Microsoft Learn
- Confidential computing application enclave nodes on Azure Kubernetes Service (AKS) | Microsoft Learn
- Confidential containers on Azure | Microsoft Learn
- Azure Firewall Premium features | Microsoft Learn
- Microsoft Entra managed identities for Azure resources documentation | Microsoft Learn
- What is a private endpoint? - Azure Private Link | Microsoft Learn
About Commerce Financial Services (CFS)
Microsoft’s Commerce Financial Services exposes a payment gateway and commerce solution for ecommerce that powers a range of Microsoft properties. The gateway enables individuals, organizations, developers and partners to securely purchase and sell Microsoft products, services, and licenses worldwide through a centralized payment platform. Commerce Financial Services provide support for 30 different payment methods using 80 currencies across 241 markets. The platform demonstrates the highest level of security and compliance as prescribed by PCI-DSS and other applicable standards. While it’s possible to deploy PCI-compliant solutions today on Azure, the addition of Azure confidential computing combined with mHSM provides a level of security beyond the PCI-DSS previously thought only attainable by dedicated private or hybrid cloud solutions.
About the Payment Card Industry Data Security Standard (PCI DSS)
The Payment Card Industry Data Security Standard (PCI DSS) is an information security standard used to manage credit cards from major card brands. The standard is administered by the Payment Card Industry Security Standards Council, and compliance with the standards is mandated by the card brands for entities that manage card data. The standards are developed and maintained by the PCI Security Standards Council (PCI SSC), a global organization that includes representatives from the payment card industry, merchants, banks, service providers, and security experts.
Published on:
Learn moreRelated posts
Azure SDK Release (February 2026)
Azure SDK releases every month. In this post, you'll find this month's highlights and release notes. The post Azure SDK Release (February 2026...
Recovering dropped tables in Azure Databricks with UNDROP TABLE
Oops, Dropped the Wrong Table? What now? We’ve all been there: you’re cleaning up some old stuff in Databricks, run a quick DROP TABLE… and su...
Azure Developer CLI (azd) – February 2026: JMESPath Queries & Deployment Slots
This post announces the February 2026 release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) – February 2026: JM...
Improved Python (PyPi/uvx) support in Azure MCP Server
Azure MCP Server now offers first-class Python support via PyPI and uvx, making it easier than ever for Python developers to integrate Azure i...
Microsoft Purview: Data Lifecycle Management- Azure PST Import
Azure PST Import is a migration method that enables PST files stored in Azure Blob Storage to be imported directly into Exchange Online mailbo...
How Snowflake scales with Azure IaaS
Microsoft Rewards: Retirement of Azure AD Account Linking
Microsoft is retiring the Azure AD Account Linking feature for Microsoft Rewards by March 19, 2026. Users can no longer link work accounts to ...