|
OT network sensors now run on Debian 11. Sensor versions 23.2.0 run on a Debian 11 operating system instead of Ubuntu. Learn more on our docs.
|
 |
Default privileged user is now admin instead of support. Starting with version 23.2.0, the default, privileged user installed with new OT sensor installations is the admin user instead of the support user. Learn more on our docs. |
 |
New architecture for hybrid and air-gapped support. Defender for IoT now provides new guidance for connecting to and monitoring hybrid and air-gapped networks. The new architecture guidance is designed to add efficiency, security, and reliability to your SOC operations, with fewer components to maintain and troubleshoot. Learn more on our docs.
|
 |
On-premises management console retirement. The legacy on-premises management console won't be available for download after January 1st, 2025. We recommend transitioning to the new architecture using the full spectrum of on-premises and cloud APIs before this date. Learn more on our docs. |
 |
Live statuses for cloud-based sensor updates. When running a sensor update from the Azure portal, a new progress bar appears in the Sensor version column during the update process. As the update progresses the bar shows the percentage of the update completed, showing you that the process is ongoing, is not stuck or has failed. 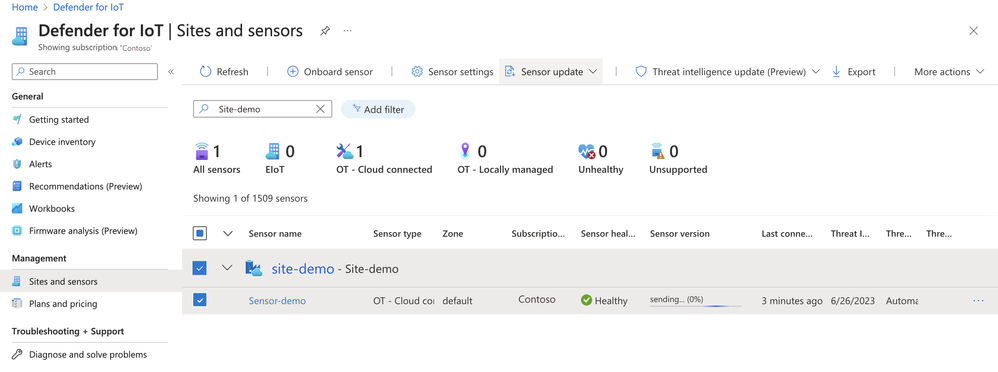
For more information, see Update Defender for IoT OT monitoring software.
|
 |
When integrating with Microsoft Sentinel, the Microsoft Sentinel SecurityAlert table is now updated immediately only for changes in alert status and severity. Other changes in alerts, such as last detection of an existing alert, are aggregated over several hours and display only the latest change made.
For more information, see Understand multiple records per alert.
|