Centrally manage permissions with the Microsoft 365 Defender role-based access control (RBAC) model

We are excited to announce the public preview of a central role-based access control (RBAC) capability to help unify roles and permissions management across Microsoft Defender for Endpoint, Microsoft Defender for Office 365, and Microsoft Defender for Identity.
The new Microsoft 365 Defender RBAC model, part of Microsoft’s leading Extended Detection and Response (XDR) solution, is an impactful enabler for security admins to centrally manage privileges across domains. It offers a unified and granular cross-services access permission model to help the Security Operations Center (SOC) increase productivity across the various Microsoft Defender products. Additionally, the new model is fully compatible with existing individual RBAC models currently supported in Microsoft 365 Defender portal.
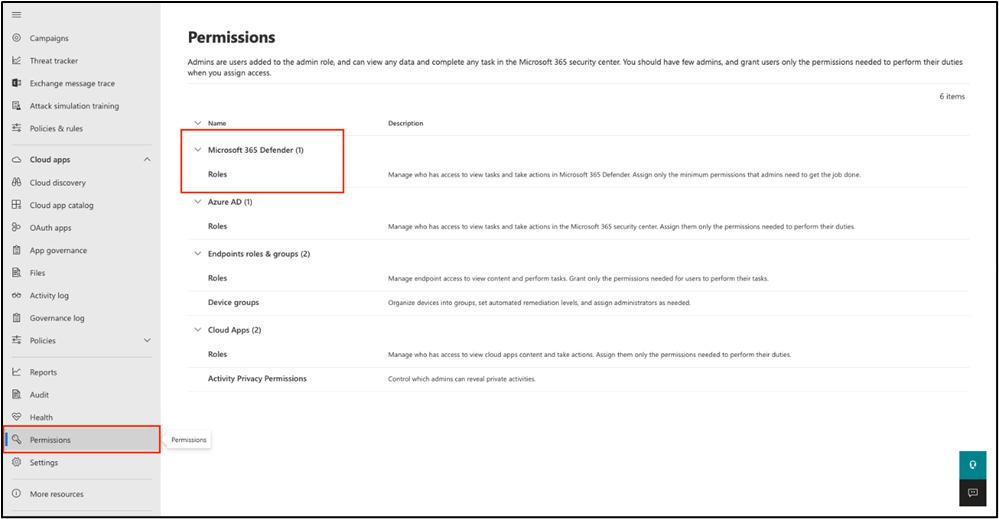
The new Microsoft 365 Defender RBAC experience
Microsoft 365 Defender provides integrated threat protection, detection, and response across endpoints, email, identities, applications, and data within a single portal. The new RBAC model now takes this experience to the next level by allowing admins to centrally manage privileges across these services with a greater efficiency. While Defender for Cloud Apps is not covered in this initial preview, it will be added to the new RBAC model in the future.
The new model organizes permissions by categories. For example, the “Security operations” category includes permissions that are required to perform daily security operations activities and allows admins to either grant out-of-the-box permissions on a per category basis or select permissions one-by-one for custom roles.
In the new model, permissions can be scoped to individual users and/or security groups. By default, custom roles created in the Microsoft 365 Defender RBAC model are scoped to all data sources. However, if needed, a role can be scoped to one or more specific data sources.
To make it easy for you to adopt the new RBAC model, we support role import capabilities so that you can import existing roles from any of our current individual RBAC models to the new Microsoft 365 Defender RBAC model with a click of a button.
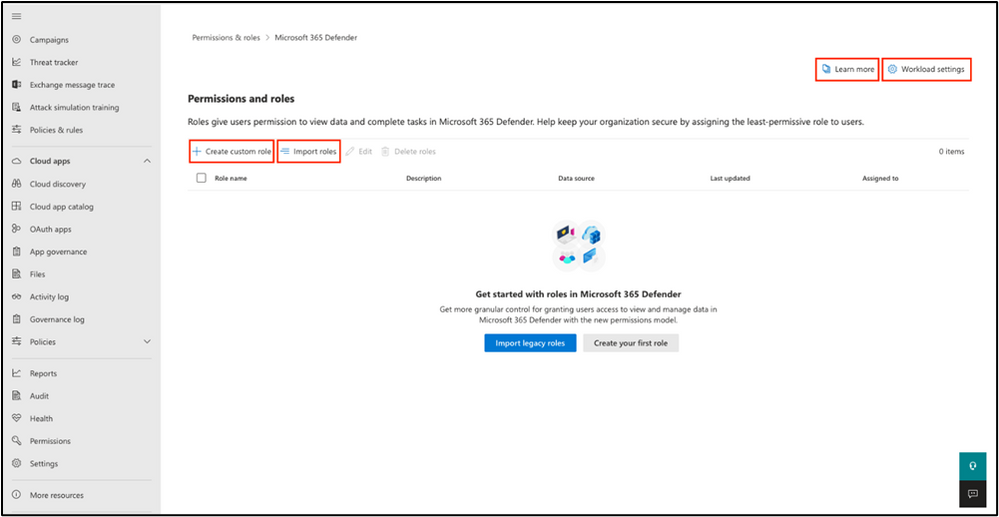
Supported Products
- Microsoft Defender for Endpoint – full support for all endpoint data and actions. All roles are compatible with Defender for Endpoint’s device group aligning.
- Microsoft Defender for Office 365 – support for the SecOps scenarios that are managed in the Microsoft Defender portal.
Note: Scenarios that adhere to Exchange Online roles are not impacted by this new model and will still be managed by Exchange Online. - Microsoft Defender for Identity – Full support for all identity data and actions.
Microsoft Defender for Cloud Apps – Will be added in the future.
Getting Started
Here is how you can get started with the new RBAC model:
If you don’t have any existing roles assigned:
- Start by creating custom roles: Enter the role name and description, select permissions, assign the role to users/a user group
- Activate Microsoft 365 Defender RBAC
- Edit or delete roles anytime as needed
You can find more details on how to create custom roles in our technical documentation.
If you have existing roles within any of the workloads:
- Import roles from the relevant workloads such as Defender for Endpoint, Defender for Identity or Defender for Office 365
- Review and modify as needed
- Activate M365 Defender RBAC
You can find more details on how to import roles in our technical documentation.
Notes:
- There will be no immediate change to the way Microsoft 365 Defender enforces permissions until admins activate the new RBAC model per workload. Only after activation, the new custom roles and imported roles will become effective.
- Only one permissions model can be honored at any given time, but the users will have the option to revert to the individual RBAC model if desired.
What about Azure Active Directory global roles and Privileged Identity Management?
Microsoft 365 Defender security portal will continue to respect existing Azure Active Directory global roles when you activate the Microsoft 365 Defender RBAC model for some or all workloads, i.e., Global Admins will retain assigned admin privileges.
However, with the new RBAC model you will have the flexibility to create more granular roles where appropriate, following the principle of least privilege and granting users only the privileges they need.
More information
- Ready to get started? Check out our technical documentation on how to transition to the new Microsoft 365 Defender RBAC model
- Let us know what you think! Share your feedback with us in the Microsoft 365 Defender portal feedback tool. Learn more about our feedback tool here.
Published on:
Learn moreRelated posts
What You Need to Know About Microsoft 365 Agents Toolkit for Enterprise AI
The journey to enterprise-ready AI often hits a gravity wall: agents that are confined to a single app, lack deep system connections, or intro...
Microsoft 365 & Power Platform Community Call – November 13th, 2025 – Screenshot Summary
Call Highlights SharePoint Quicklinks: Primary PnP Website: https://aka.ms/m365pnp Documentation & Guidance SharePoint Dev Videos Issues...
Microsoft 365 Copilot: Copilot integration for OneDrive files in macOS Finder
Microsoft 365 Copilot will integrate with OneDrive files in macOS Finder starting mid-November 2025, allowing users with appropriate licenses ...
Microsoft Teams: App centric management in Teams Admin Center to manage the Apps access for tenants, end-users, and groups in GCC
App centric management introduces new admin settings to control who in the tenant can install Teams apps. First, admins can set a default valu...
SharePoint: Site Branding Governance via PowerShell
Empower tenant admins to centrally manage SharePoint site branding using PowerShell scripts. This feature enables organizations to enforce con...
Transform Business with Fusion Teams And Low-Code Copilot
In today’s fast-paced business world, the pressure to deliver faster digital solutions is intensifying by the day, especially when it comes to...
Microsoft Makes Another Change to Teams Channel Email Storage Location
In January 2025, Microsoft changed the SharePoint folder location to store copies of the email sent to Teams channels. Apparently, this update...
Legacy SharePoint Online Content Delivery Network (CDN) domain to be retired—review configurations
The legacy SharePoint Online CDN domain publiccdn.sharepointonline.com will be retired by late April 2026. Update all hardcoded references to ...
Microsoft Teams frontline BYOD onboarding wizard
Microsoft is introducing a dynamic onboarding wizard for frontline workers using personal Android or iOS devices to set up Microsoft Teams sec...
New customer onboarding for Google and Microsoft Teams calendar sync paused
Microsoft has paused new customer onboarding for calendar sync between Google Workspace and Microsoft Teams effective immediately. Existing se...