The power of incidents in Microsoft 365 Defender
Incidents in Microsoft 365 Defender are powerful tools allowing SecOps to triage, investigate and response to cyber-attacks in one place.
Incidents provide the full attack picture due to advanced signals correlation capabilities. Our algorithms automatically correlate signals from all Microsoft security & compliance solutions, like an experienced analyst would. It gathers related telemetry and other alerts that belong to the same attack. Microsoft 365 Defender also uses AI to continually analyze the vast amount of available data and, if necessary, suggest more evidence for the analyst to add to the incident from a variety of sources such as:
- Microsoft Defender for Endpoint
- Microsoft Defender for Identity
- Microsoft Defender for Office 365
- Microsoft Defender for Cloud Applications
- Microsoft Data Loss Prevention
- Azure AD Identity Protection (limited preview)
Today, unlike before, all the alerts are part of incidents. Alerts from all these products, are correlated into incidents to help expedite the response time of your SecOps team.
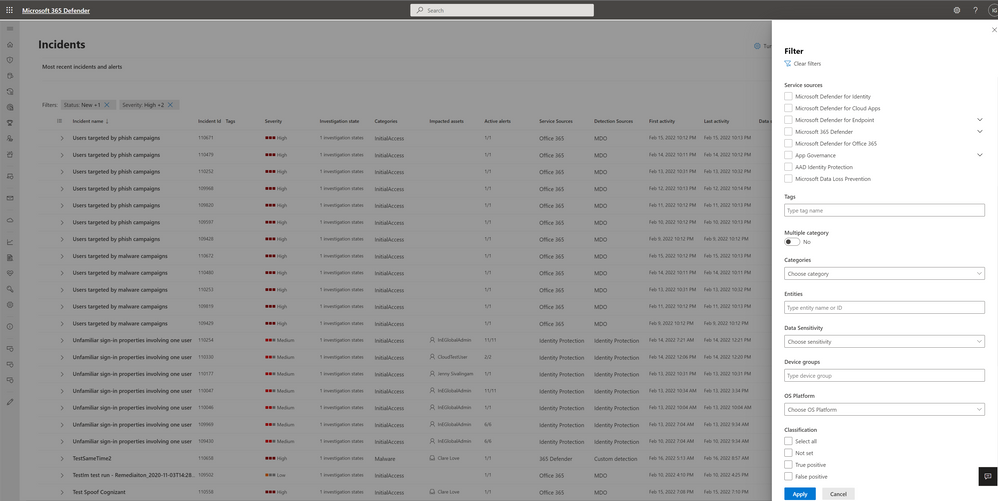
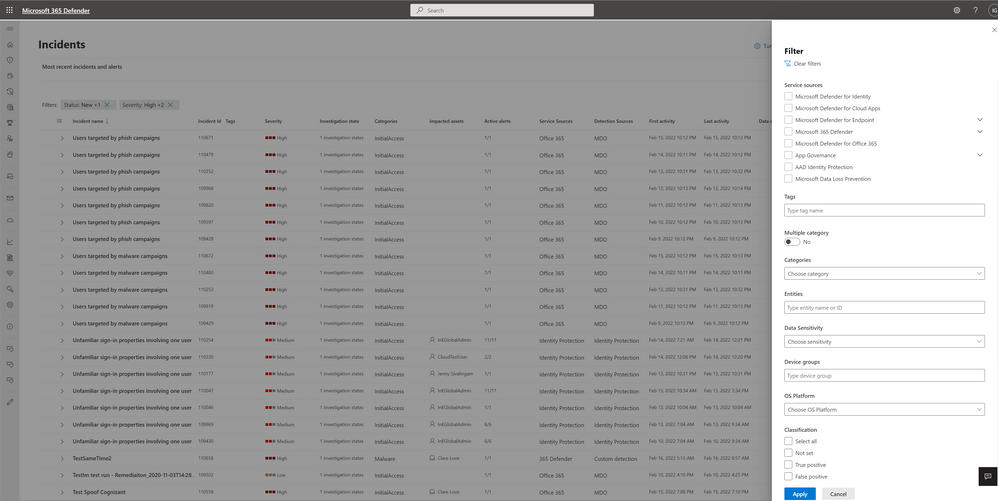
For an even more effective exploration of the incidents queue, we recently added new features that will further streamline your investigations:
- Use the summary to quickly understand how the queue is being filtered
- Search incidents by ID, name and impacted assets such as user, device, mailbox, or application name.
- Specify a custom time range that includes both dates and times
New filters in incident queue
Once you identify an incident to research, you can investigate an attack across stages - from
Some of the powerful incident investigation capabilities include:
- Understand the progress of an attack against the MITRE attack kill-chain
- Identify the attack scope and review all involved entities and assets, enriched with all relevant Microsoft 365 Defender data
- Investigate using a visual graph to
- Take action and respond to the attack
- Easily assign the incident to other analysts in the SOC
Play the attack over the incident graph
Learn how Microsoft 365 Defender can help your organization stop attacks with coordinated defenses. Read these blog posts in the Inside Microsoft 365 Defender series:
Published on:
Learn more