Get email notifications for any actions in Defender XDR
Effective cybersecurity operations are a team effort. When there is an important incident, it is crucial to ensure that key stakeholders on the team are promptly informed. Providing immediate notifications for critical activities to relevant team members not only raises awareness but reduces response times and improves alignment among stakeholders. These critical notifications can often involve remediation or response actions that take place on entities such as identities or devices in am organization’s environment.
To ensure visibility across the right stakeholders, whether actions are initiated automatically by the system or manually by members of the SOC, it's key that it reaches the right people on the team, fast.
Today we are excited to announce the public preview of email notifications for actions taken within Microsoft Defender XDR. This feature enables the SOC and relevant stakeholders (e.g., security admins, IT) to receive notifications whenever an automated or manual action is taken. It allows them to:
- Improve stakeholder alignment – stakeholders can be notified on certain actions and assets, according to relevance.
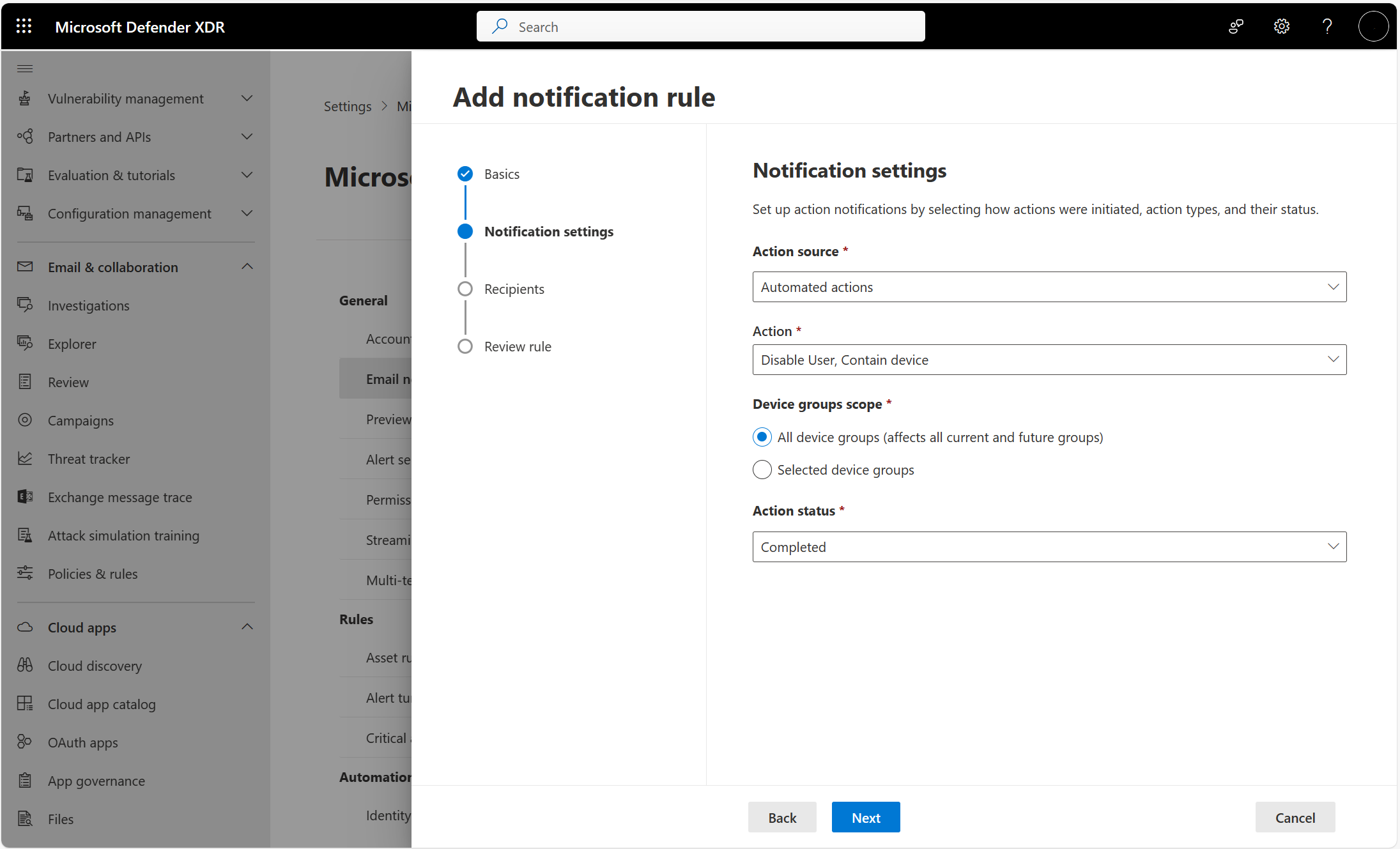
- Gain visibility into remediation actions that take place in real time – rules can be set to receive emails on automated (e.g., contain device, disable user) or manual actions (e.g., live response, isolate device, delete email)
- Get notified about actions according to their state – notifications can be set to be sent when an action fails, succeeds, or both.
Key scenarios for automatic email notifications
Below are two examples where the SOC can benefit from creating email-based notifications for both a system-automated, as well as manual action taken in Microsoft Defender XDR:
Automatic attack disruption contains a device or disables a user account – Automatic attack disruption in Microsoft Defender XDR disrupts in-progress attacks such as ransomware and takes action to contain them such as disabling compromised user accounts and isolating devices. It does so only when high confidence is established, however to ensure that relevant teams are aware that a containment action took place automatically, a relevant rule can be set. The IT, SOC, and helpdesk teams can be notified by email whenever a compromised user or device is affected. This helps raise awareness quickly and will allow the respective teams to investigate and remediate faster to bring any affected user back online fast and restore productivity.
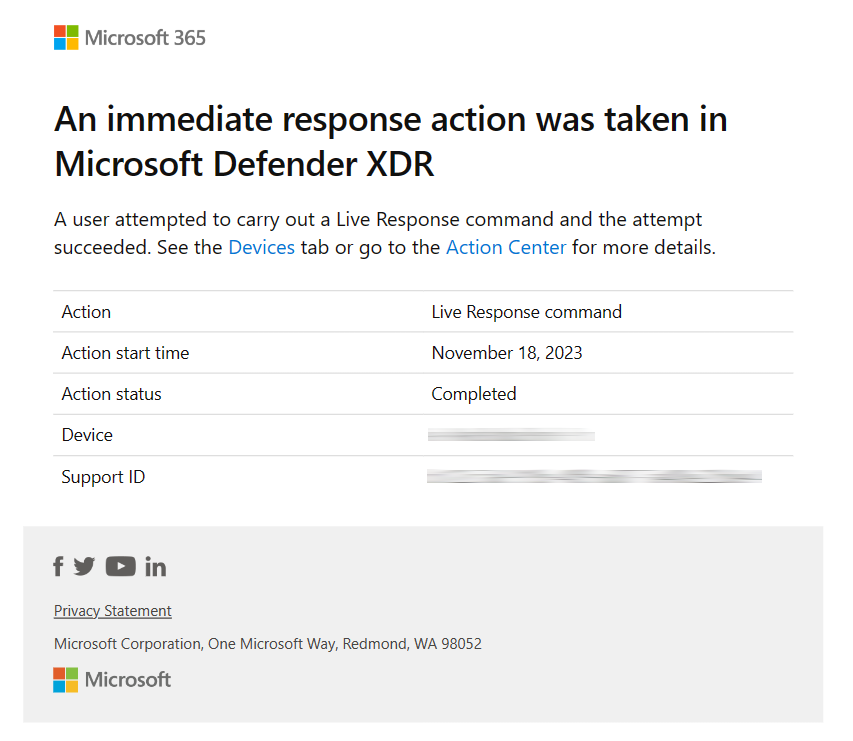
Sensitive action is carried out on critical assets – certain sensitive assets such as domain controllers (DCs) are often monitored closely by the SOC. To raise visibility when a sensitive action such as a ‘live response’ session is established on one or more DCs, now the SOC team can set up a rule to get notified whenever a successful or even failed attempt to establish a ‘live response’ session takes place.
Get started
Image 1 shows the easy configuration to setup email notification in Microsoft Defender XDR, while image 2 shows you what a notification will look like when delivered to your inbox.

At Microsoft we understand the critical role that incident awareness and transparency plays in effective security operations. That's why we're constantly working to improve our platform and release new features such as the above to help customers stay on top of important events so that they can respond to cyberattacks quickly and efficiently.
Learn more
- To get started, read our action email notification documentation.
- To learn more about Microsoft Defender XDR, visit our website.
Published on:
Learn more