New milestones at Ignite 2022 for Azure confidential computing
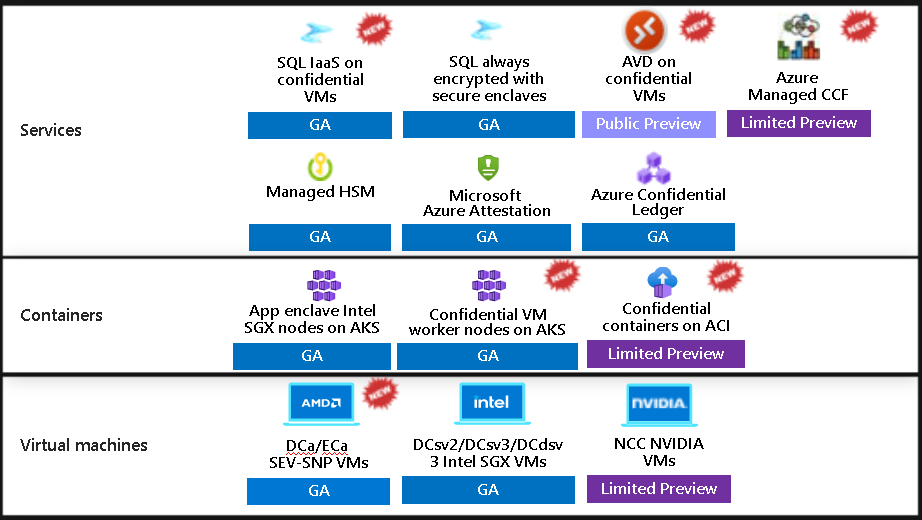
Today we are pleased to announce six major milestones in the Azure confidential computing portfolio:
- General availability of guest attestation for AMD EPYC™ SEV-SNP based confidential VMs
- General availability of Azure Kubernetes Service (AKS) node pools using AMD EPYC™ SEV-SNP based confidential VMs
- General availability of AMD EPYC™ SEV-SNP based confidential VMs for SQL Server on Azure Virtual Machines
- Public preview of the Windows 11 desktop option running on AMD EPYC™ SEV-SNP based confidential VMs for Azure Virtual Desktop
- Preview of the Azure Managed Confidential Consortium Framework
- Preview of customizable firmware for AMD EPYC™ SEV-SNP based confidential VMs
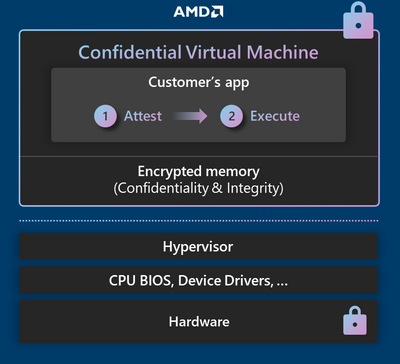
Confidential VMs and guest attestation
The AMD Azure EPYC™ SEV-SNP DCasv5 and ECasv5-series confidential VM series provides a hardware-based Trusted Execution Environment (TEE) that features AMD SEV-SNP security capabilities. These capabilities harden guest protections to deny the hypervisor and other host management code access to VM memory. This helps prevent operator access to data residing in the confidential VM. Customers can easily migrate their legacy workloads from on-premises environments to the cloud with minimal performance impact and without code changes by leveraging the new AMD-based confidential VMs. These confidential VMs also support added protections such as confidential OS disk encryption with a customer managed key, and integrations with Azure Managed HSM (Hardware Security Module) and Azure Key Vault. Customers can also use the free Microsoft Azure Attestation (MAA) service to verify the operating environment, and the root of trust based on the AMD CPU and the hardware Trusted Processor Module.
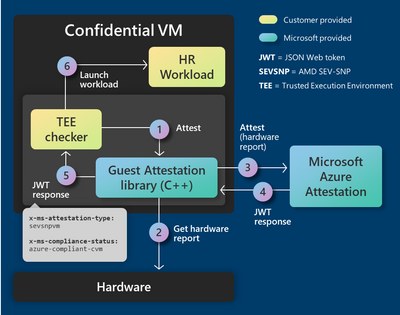
Guest attestation is a new feature enabled for confidential VMs. Guest attestation allows for verifying the identity, trustworthiness and known secure configuration of the Trusted Execution Environment on which the guest VM is executing. Remote attestation artifacts (token and claims) received from another system (on a Confidential VM) can enable relying parties to gain trust to make transactions with the remote system. And with its interface with Microsoft Defender for Cloud, users can receive recommendations and alerts of unhealthy CVMs. To learn more about guest attestation, see the documentation and the blog post.
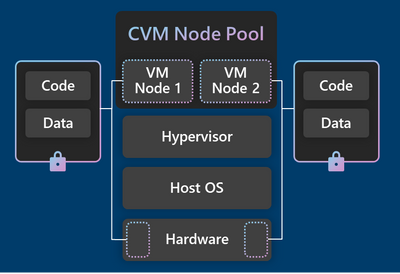
Confidential VM node pools on AKS
Azure Kubernetes Service (AKS) node pools using confidential VMs has been in public preview since August 2022. This service allows users to run sensitive Kubernetes managed workloads on confidential VMs without the need to modify their applications. Today this service becomes generally available. To learn more, read the documentation and the blog post.
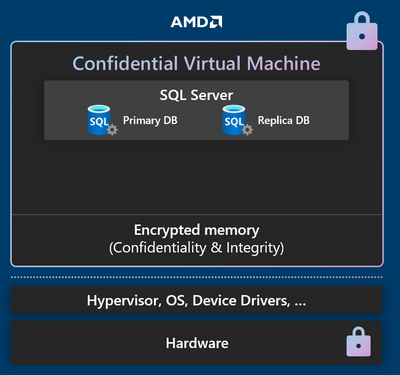
Confidential VM option for SQL Server on Azure VMs
SQL Server on Azure Virtual Machines lets users migrate their SQL Server instances to Azure and run them on the VM type of their choice. Running SQL Server on confidential VMs allows SQL Server users to migrate their most sensitive SQL database application to Azure without changes to their application or database schema, while protecting data when in use in memory. With Azure confidential VMs, you can also reinforce the protection of your data at rest (in database files) by enabling confidential OS disk encryption and encrypting data disks using BitLocker with keys stored on the OS disk. This makes the protected disk content accessible only to the VM. To learn more, read the documentation and the blog.
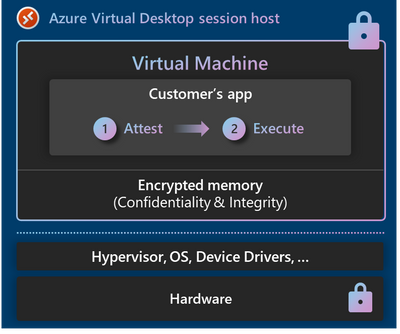
Azure Virtual Desktop (AVD) on confidential VMs
Azure Virtual Desktop (AVD) lets users run Windows desktop on Azure and access it securely from any device running the AVD client. With the public preview of the Windows 11 desktop option running on confidential VMs, users can now run their sensitive desktop applications on Azure, with data always cryptographically protected. Read the documentation to learn more.
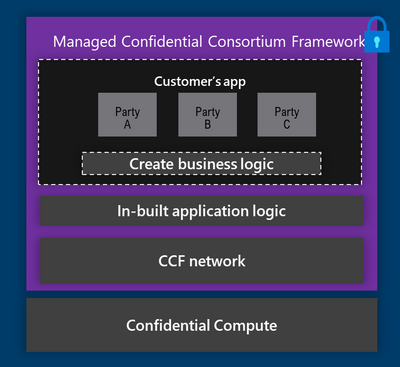
Azure Managed Confidential Consortium Framework
Finally, with the preview of Azure Managed Confidential Consortium Framework, we are offering a new Azure service that hosts the infrastructure for the open source Confidential Consortium Framework (CCF), simplifying the experience for developing and hosting CCF applications. CCF lets users create decentralized trust services on a confidential governed network. The framework decouples network and application governance from node provisioning and operation, making it possible for limited-access operators to maintain the infrastructure and ability to execute transactions without having access to their contents. Network governance on the other hand, for example deciding what code to execute, is entirely driven by consortium members, is rules-based, programmable, and auditable to all participants through an immutable verifiable history ledger. Examples of decentralized trust stateful services that can be built on Azure Managed Confidential Consortium Framework include: banking consortium to share reference data about securities, payment provider run fraud detection algorithms to flag without revealing information, and many more. To learn more about the CCF, visit the new website, read the documentation. To learn more about Azure Managed Confidential Consortium Framework read the blog post. And sign up for the preview to try it for yourself.
Confidential VMs with customizable firmware
For organizations seeking more control over the confidential trust boundary, we have a preview of customizable firmware for confidential VMs. This reference implementation enables sophisticated customers to further minimize dependency on Azure services and UEFI-based firmware, by replacing it with a Linux kernel and runtime. Applications are reviewed on an ongoing basis, to help us shape future implementations of this program.
Get started with Azure confidential computing now
Customers of all sizes, across all industries, want to innovate, build, and securely operate their applications across multi-cloud, on-premises, and edge. Just as HTTPS has become pervasive for protecting data during internet web browsing, we believe that confidential computing will be a necessary ingredient for all computing infrastructure.
Get started here:
Published on:
Learn moreRelated posts
What runs ChatGPT, Sora, DeepSeek & Llama on Azure? (feat. Mark Russinovich)
Build and run your AI apps and agents at scale with Azure. Orchestrate multi-agent apps and high-scale inference solutions using open-source a...
Azure Cosmos DB TV – Everything New in Azure Cosmos DB from Microsoft Build 2025
Microsoft Build 2025 brought major innovations to Azure Cosmos DB, and in Episode 105 of Azure Cosmos DB TV, Principal Program Manager Mark Br...
Azure DevOps with GitHub Repositories – Your path to Agentic AI
GitHub Copilot has evolved beyond a coding assistant in the IDE into an agentic teammate – providing actionable feedback on pull requests, fix...
Power Platform Data Export: Track Cloud Flow Usage with Azure Application Insights
In my previous article Power Platform Data Export: Track Power Apps Usage with Azure Data Lake, I explained how to use the Data Export feature...
Announcing General Availability of JavaScript SDK v4 for Azure Cosmos DB
We’re excited to launch version 4 of the Azure Cosmos DB JavaScript SDK! This update delivers major improvements that make it easier and faste...
Confluent Cloud Releases Managed V2 Kafka Connector for Azure Cosmos DB
This article was co-authored by Sudhindra Sheshadrivasan, Staff Product Manager at Confluent. We’re excited to announce the General Availabili...
Now in Public Preview: Azure Functions Trigger for Azure Cosmos DB for MongoDB vCore
The Azure Cosmos DB trigger for Azure Functions is now in public preview—available for C# Azure Functions using Azure Cosmos DB for MongoDB vC...
Now Available: Migrate from RU to vCore for Azure Cosmos DB for MongoDB via Azure Portal
We are thrilled to introduce a cost-effective, simple, and efficient solution for migrating from RU-based Azure Cosmos DB for MongoDB to vCore...
Generally Available: Seamless Migration from Serverless to Provisioned Throughput in Azure Cosmos DB
We are excited to announce the general availability (GA) of a highly requested capability in Azure Cosmos DB: the ability to migrate from serv...