What’s new in XDR at Microsoft Ignite

Security Operations (SOC) teams are on the front lines keeping organizations safe from cyber threats. With the continuously evolving threat landscape, they are faced with detecting and remediating cyberattacks that are increasing in sophistication, frequency, and speed.
Microsoft Defender 365, a leading Extended Detection and Response (XDR) solution, correlates millions of signals from endpoints, identities, email, cloud apps, and more into full incidents that help defenders cut through the noise of individual alerts to see entire attack kill chain. This gives defenders end-to-end context on cross-domain attacks like ransomware and makes it easier to quickly mitigate threats.
But there is more to be done. Our data shows a tremendous increase in velocity as attackers utilize powerful toolkits, cloud infrastructure, and proven expertise in their attacks. Most recently, we've observed that it can take less than two hours from a user clicking on a phishing link, to an attacker having full access to the inbox and moving laterally. At this speed, many organizations won’t even know they’ve been breached until it’s too late. Defenders need a solution that helps them stay on top of in-progress attacks and match machine speed with machine speed.
Today, we are announcing a series of new capabilities in Microsoft 365 Defender to empower defenders to stay ahead of attackers:
- Automatic Attack disruption to contain in-progress attacks and isolate affected assets
- Prevent repeat-attacks with a new way to prioritize security recommendations
- Further unification and optimization of the admin, investigation, and remediation experience
Lastly, we are excited to announce a limited time offer to save 50% on Microsoft Defender for Endpoint P1 and P2 licenses for new and renewing customers. For more details on this offer, read the Defender for Endpoint Ignite news blog.
Automatic Attack Disruption at machine speed
We’re excited to announce the public preview of automatic attack disruption in Microsoft 365 Defender to help protect organizations at machine speed.
Using the power of XDR, Microsoft 365 Defender correlates millions of individual signals to identify active ransomware campaigns or other sophisticated attacks in the environment with a high level of confidence. While still in progress, Microsoft 365 Defender will automatically take action to disrupt the attack by automatically isolating infected devices from the network and suspending compromised accounts that are being used by the attacker.
This game-changing capability limits lateral movement early on and reduces the overall impact of an attack from associated costs to loss of productivity. At the same time, it leaves the SOC team in full control of investigating, remediating, and bringing assets back online.
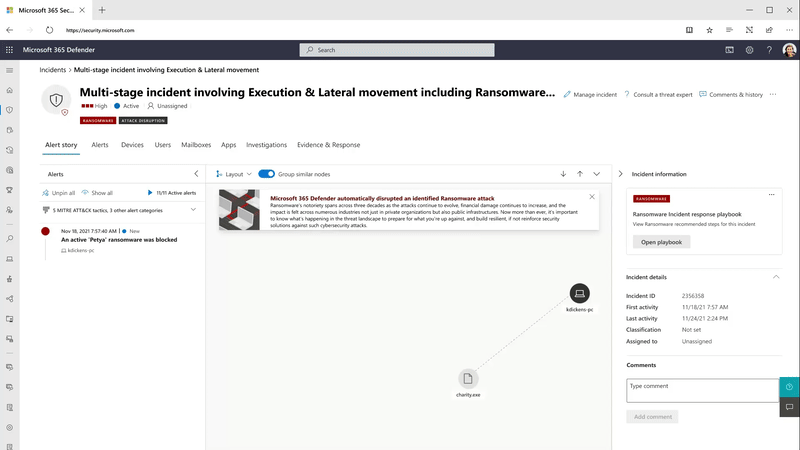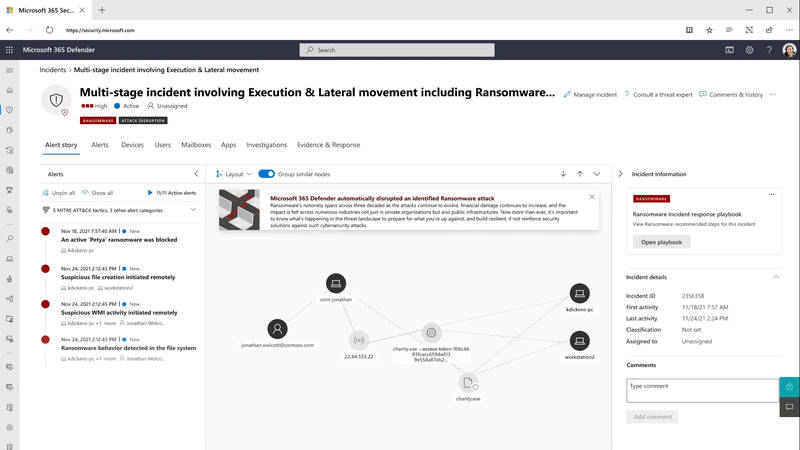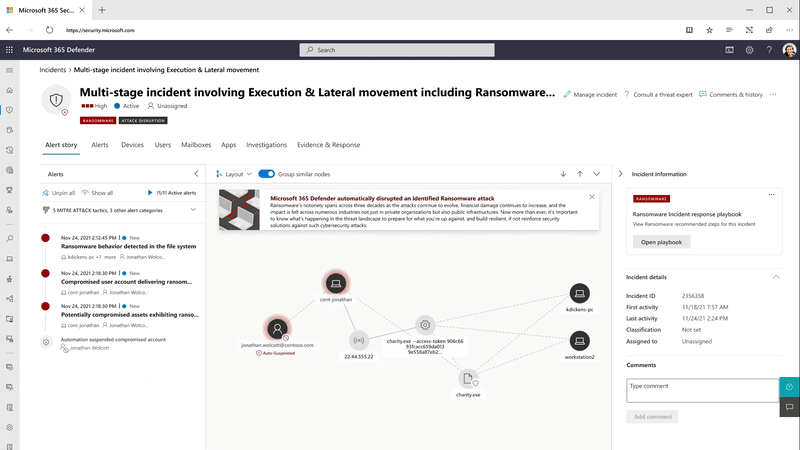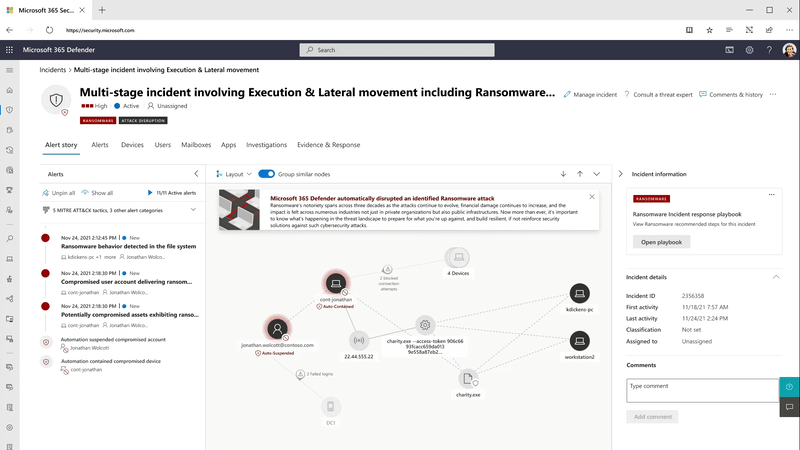
Automation is critical to scaling SOC teams’ capabilities across today’s complex, distributed, and diverse ecosystems and showcases the true power of an XDR solution that correlates signals across endpoints, identities, email, documents, cloud apps, and more. Disrupting in-progress attacks at machine speed will significantly shorten the time to respond for many organizations and make SOC teams even more effective.
Improve your security posture with attack insights
Our goal is to enable customers to put their environment in the best possible position to prevent attacks from happening in the first place. No one wants to see the same attack or exploited vulnerability in their environment twice. Using the power of XDR, Microsoft 365 Defender analyzes the techniques used by an attacker from real-world attacks and maps them to security posture controls that we provide across workloads.
These recommendations are provided in a new, prioritized view of security settings recommendations that show which settings will helpto prevent similar attacks in the future. This view puts security recommendations in direct context of an attack and creates a completely new way to effectively prioritize security posture improvements.

As part of your investigation view in Microsoft 365 Defender, you will now see a new tab called “Exposures and mitigations” as shown in Figure 2. It shows a list of recommended security settings and at the top shows which attacks that recently affected your environment could have been prevented if these settings had been in place.
Using this new, prioritized view will enable the SOC and security admin teams to more easily prioritize the most impactful security settings to improve the organization’s security posture and create a stronghold against adversaries.
Streamline your investigation with Microsoft 365 Defender
In addition to automatic attack disruption and prioritized security recommendations, we’re going even further to help SOC teams be more efficient.
We continuously work with organizations to better understand SOC workflows and how they can be optimized to make investigations more effective. We learn from live case study sessions, and leverage findings to design our experiences around these workflows - making sure the right information, insights and tooling is optimized so analysts can do their best work.
Integrating cloud app security into Microsoft 365 Defender
SaaS security is a critical component of any XDR – that’s why we are fully integrating the cloud app security experience into Microsoft 365 Defender. While we released the Microsoft Defender for Cloud Apps SecOps experience in public preview back in June, today we are excited to announce that later this month all capabilities in Defender for Cloud Apps will be available in Microsoft 365 Defender in public preview.
Organizations will benefit from a centralized experience for discovery, investigation, mitigation, and handling incidents all from a single portal. All familiar capabilities from Shadow IT Discovery to investigation are now integrated into Microsoft 365 Defender and enable your SOC to hunt across app, endpoint, identity datapoints, and more as shown in Figure 3.
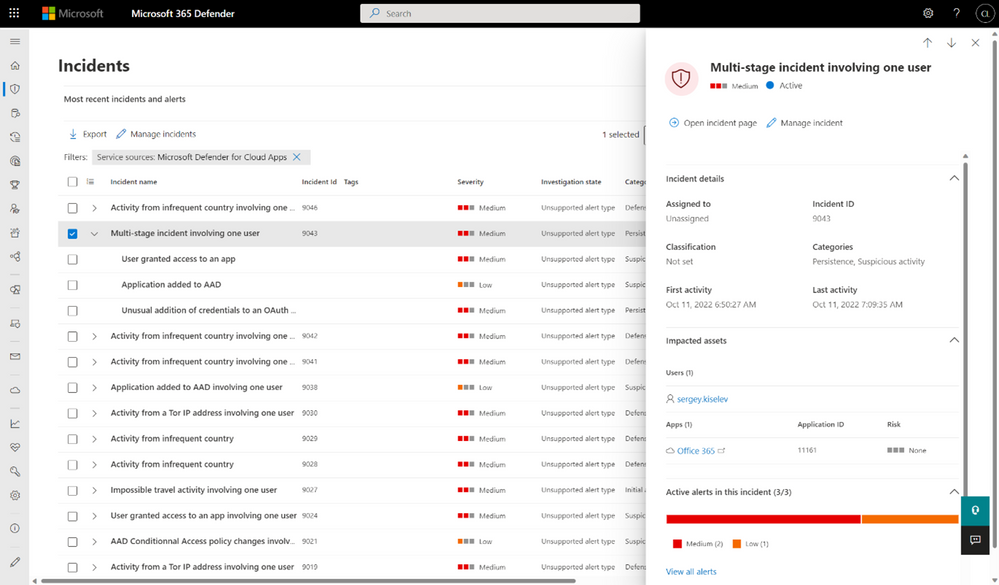
As part of the public preview, we also merged the information protection capabilities into Microsoft 365 Defender. This includes the ability to connect apps, visibility into files, and configuring policies for both data at rest and in motion so you can continue to protect sensitive data and enforce governance across your most critical assets. Figure 4 shows the new home for the settings and app connectors.

Lastly, we integrated OAuth and app governance capabilities as part of the public preview – these provide visibility into the API activity associated with OAuth apps and apps that leverage the Graph API to access Microsoft 365 data.
Optimize your SOC workflows with Microsoft 365 Defender
While incident views in Microsoft 365 Defender already correlate billions of signals and provide a unified investigation and remediation experience, we’ve further improved the investigation views to ensure analysts can easily drill deep into an incident and stop breaches faster.
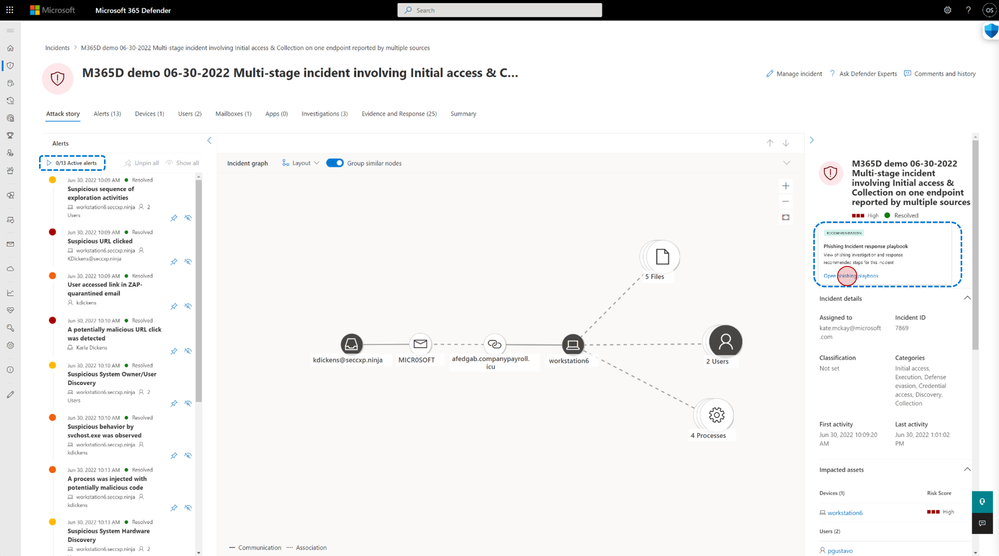
In the initial phase of investigation, it’s about determining what happened and which assets are affected. The incident graph provides a visual representation of the attack story, showing all involved objects and how they were impacted in the attack.
Beyond the visual graph, it’s key for analysts to be confident in which steps to take to start remediation. Microsoft 365 Defender now includes incident-level SOC playbooks that are provided within the incident experience to start remediation. The playbooks include a step-by-step guide with best practice recommendations for how to investigate and respond to the incident at hand. Figure 3 shows the example of a Phishing campaign. These guides are designed to be interactive and link to additional materials such as documentation, blogs, and videos.
From customer feedback, we know that a big efficiency drain is continuous context-switching during an investigation. SOC teams that use tooling across numerous, disconnected solutions often lose valuable time manually piecing together related signals.
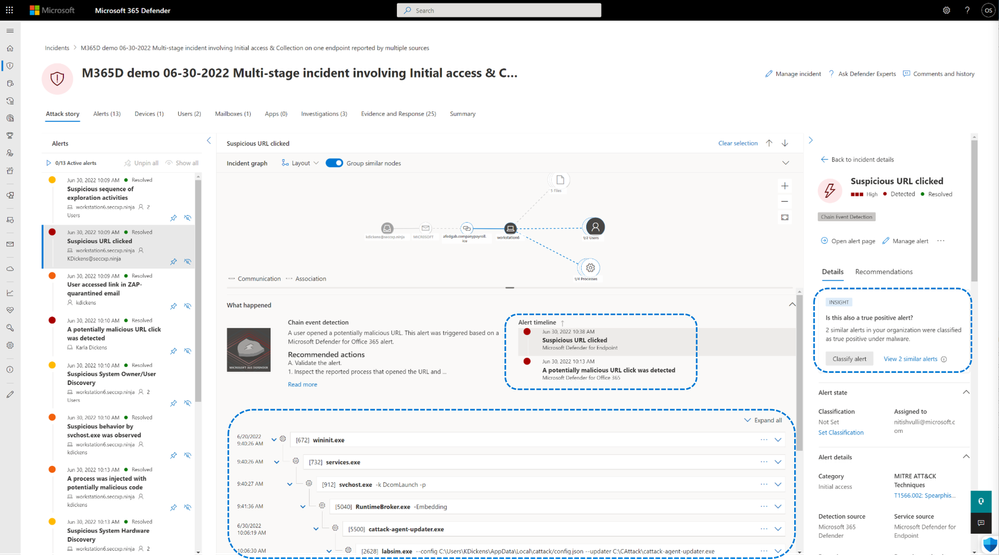
To address this, we redesigned the investigation experience in Microsoft 365 Defender, so analysts always retain the full context of an incident, even when drilling deep into individual alerts.
Figure 6 shows that the alert story now opens within the same page to keep the entire context of the incident within the same view and enables analysts to immediately take action. Lastly, the new view allows analysts to review similar alerts that recently occurred in their environment and understand how those were classified, so they can more quickly understand the potential impact and take relevant action against the alert at hand.
The capabilities we announced today will enable defenders to match the powerful techniques of adversaries and limit the impact to their organization by using automatic attack disruption at machine speed, help SOC teams and security admins improve the security posture of their organization more effectively, and most importantly respond to attacks faster with an investigation experience designed for efficiency.
More at Microsoft Ignite 2022
Make the most out of Microsoft Ignite and join some of the sessions where we’ll dive into each of these announcements.
- Watch the Microsoft Ignite session “What’s new in SIEM and XDR: Attack disruption and SOC empowerment” for more announcements across SIEM + XDR.
- Interested in helping our teams design the future of our products? Join one of the roundtable discussions during Microsoft Ignite with our product teams!
- Want to know what other news we announced today? Read Vasu Jakkal’s blog “5 cybersecurity capabilities announced at Microsoft Ignite 2022 to help you secure more with less”
- Learn more about the latest SIEM innovations in Microsoft Sentinel in this blog.
Published on:
Learn more