Enhance your privacy posture without code changes with Azure confidential computing
As regulated industries embrace the cloud, they seek higher levels of protection for their most sensitive workloads. Microsoft spends billions of dollars per year on cybersecurity, much of that goes to make Microsoft Azure a trusted cloud platform. With our investments in Azure confidential computing – we’re extending data protections from “at-rest” and “in-transit”, to now while its “in-use”.
In our first episode, we showcased new default memory protections and demonstrated confidential computing with Application-Level Enclaves. Join us for the second episode in the series – as Jeremy Chapman and Michael McReynolds discuss new options to achieve confidentiality without code changes.
Here are the highlights from our second episode.
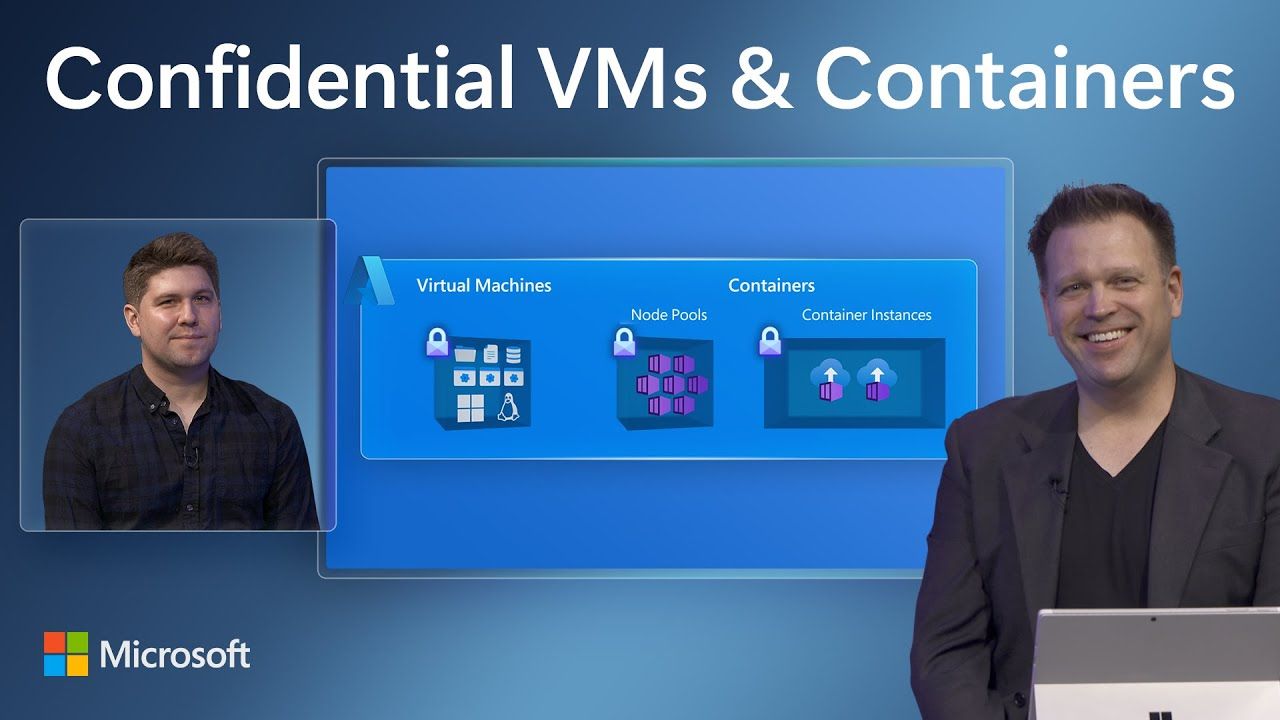
Broadening the Spectrum of Offerings. Azure continues to grow its comprehensive set of confidential computing offerings. This year, we took major steps to broaden the technologies we offer to meet the needs of customers. We see these technologies on a spectrum, each suited to the uniqueness of the workload. Whether you want to “lift and shift” on-prem virtual machines into confidential computing, or you want to build a confidential cloud-native solution with containers, or you want to achieve the using application-enclaves - we have solutions for all.
Secure Encrypted Virtualization – Secure Nested Paging. SEV-SNP is new functionality from AMD, first introduced with the 3rd Generation EPYC processors. SEV-SNP adds new hardware-based protections such as memory encryption with integrity protection to help prevent malicious hypervisor-based attacks. It offers stronger protection around interrupt behavior, as well as helping protect against memory and data corruption attacks.
Confidential Virtual Machines. Earlier this year, we reached the general availability on confidential VMs. They are designed to provide organizations with an easy button to confidentiality, enabling more sensitive workloads to migrate with no code changes and minimal performance overheads. For organizations seeking control over VM firmware, check out the preview of this functionality. By leveraging AMD SEV-SNP, these VMs have hardened guest protections from the hypervisor and other host management codes, enabling organizations to minimize the attack surface and further reduce trust in the cloud provider.
Confidential Computing Attestation. A core tenet of confidential computing is attestation. This process enables organizations to remotely “attest” the validity of the infrastructure they are deploying applications and secrets into. Today, we reached a major milestone with confidential VMs by enabling guest attestation functionality which we’ve open sourced. By using this, organizations can cryptographically verify the authenticity of the platform is what they expect it to be.
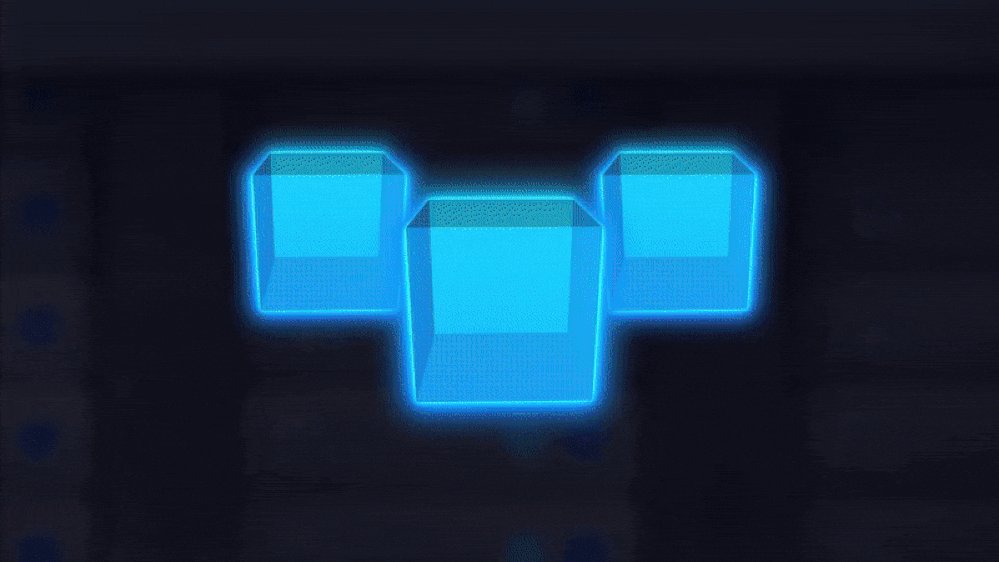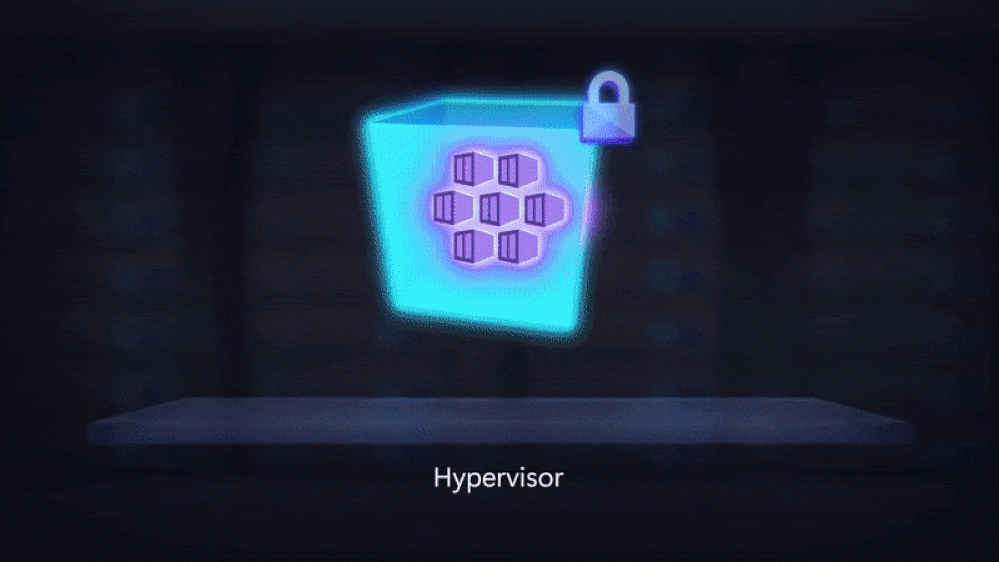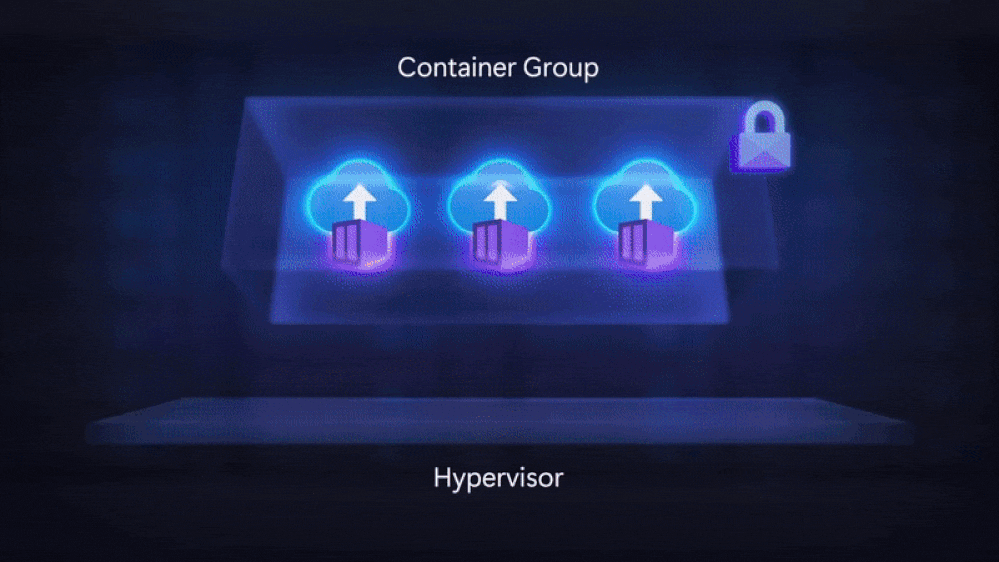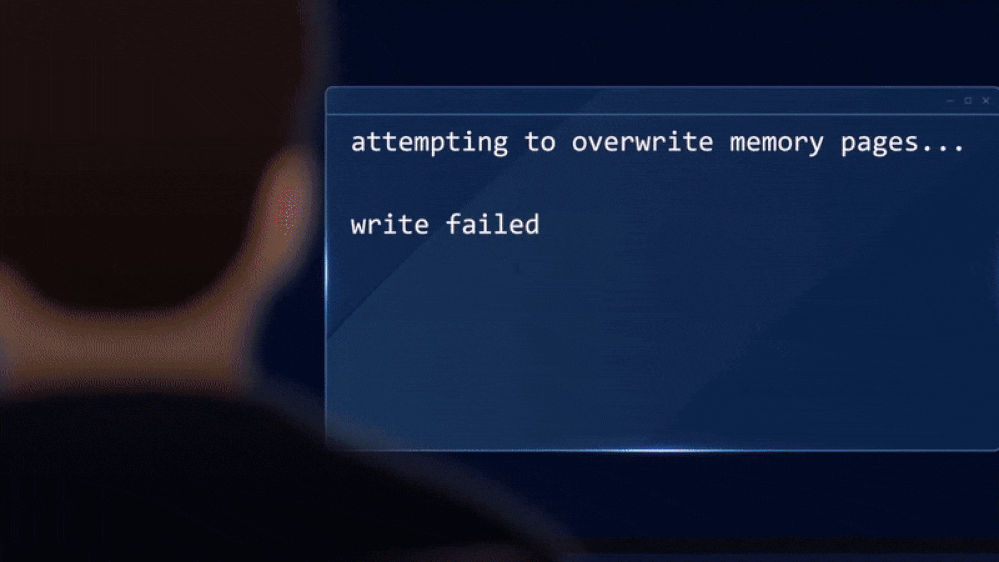
Confidential VM Node Pools. Building on top of the innovation in VMs, we released confidential VM node pools on Azure Kubernetes Service (AKS), and today we are announcing it is now generally available. AKS inherits the memory encryption from the AMD SEV-SNP hardware and extends it directly to the containers. This helps protect sensitive containerized applications from memory attacks and cross-tenant lateral attacks.
Confidential Containers on Azure Container Instances (ACI). Finally, we released an industry first serverless offering in limited preview. This offering enables you to bring your existing Linux containers, running them within an AMD SEV-SNP environment. ACI works by extending the memory encryption protections directly to your container group level, providing an even tighter trust boundary and with less code.
Please enjoy the show, and as always - we want to hear from you! If you have any questions, suggestions, or product improvements you’d like us to make, please comment and we will address them.
Learn More
- Learn about Azure confidential computing
- DCasv5 and ECasv5 are now generally available
- Documentation for General Purpose Confidential Virtual Machines
- Documentation for Memory Optimized Confidential Virtual Machines
Additional Resources
- To learn about the threat model visit aka.ms/cvmthreatmodel
Published on:
Learn moreRelated posts
Microsoft Entra ID Governance: Azure subscription required to continue using guest governance features
Starting January 30, 2026, Microsoft Entra ID Governance requires tenants to link an Azure subscription to use guest governance features. With...
Azure Developer CLI (azd) – January 2026: Configuration & Performance
This post announces the January 2026 release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) – January 2026: Conf...
Azure SDK Release (January 2026)
Azure SDK releases every month. In this post, you'll find this month's highlights and release notes. The post Azure SDK Release (January 2026)...
Azure Cosmos DB TV Recap – From Burger to Bots – Agentic Apps with Cosmos DB and LangChain.js | Ep. 111
In Episode 111 of Azure Cosmos DB TV, host Mark Brown is joined by Yohan Lasorsa to explore how developers can build agent-powered application...
Accelerate Your Cosmos DB Infrastructure with GitHub Copilot CLI and Azure Cosmos DB Agent Kit
Modern infrastructure work is increasingly agent driven, but only if your AI actually understands the platform you’re deploying. This guide sh...
Accelerate Your Cosmos DB Infrastructure with GitHub Copilot CLI and Azure Cosmos DB Agent Kit
Modern infrastructure work is increasingly agent driven, but only if your AI actually understands the platform you’re deploying. This guide sh...
SharePoint: Migrate the Maps web part to Azure Maps
The SharePoint Maps web part will migrate from Bing Maps to Azure Maps starting March 2026, completing by mid-April. Key changes include renam...
Microsoft Azure Maia 200: Scott Guthrie EVP
Azure Cosmos DB TV Recap: Supercharging AI Agents with the Azure Cosmos DB MCP Toolkit (Ep. 110)
In Episode 110 of Azure Cosmos DB TV, host Mark Brown is joined by Sajeetharan Sinnathurai to explore how the Azure Cosmos DB MCP Toolkit is c...