Simplifying SaaS Security: Deploying Microsoft Defender for Cloud Apps in 4 steps

The Software as a Service (SaaS) landscape has evolved dramatically. The proliferation of cloud-based applications has brought significant benefits in terms of scalability, accessibility, and cost-effectiveness. However, it has also led to an increased need for organizations to secure these applications and protect their data. We understand it can be challenging to know where to begin and ensure you have protection across your entire digital estate.
Microsoft Defender for Cloud Apps makes it simple to secure organization’s SaaS applications. It can be deployed quickly and easily, with no other dependencies or installations required. We’ll walk through 4 steps that demonstrate how easy it is to deploy Defender for Cloud Apps and protect your organization from app-based threats.
Step 1: Protecting Microsoft 365
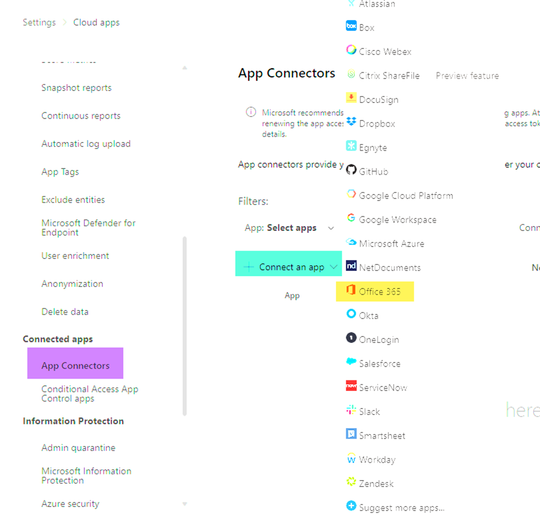
Defender for Cloud Apps integrates seamlessly with Microsoft 365 Defender, lighting up a suite of security services to protect your organization's data. To connect Defender for Cloud Apps to Microsoft 365, from the Microsoft 365 Defender Portal navigate to Settings > Cloud Apps > App Connectors then click “Connect an app > Office 365.”
Figure 1. How to connect to Office 365 via the Settings pane in Microsoft 365 Defender
Check the box for the relevant Microsoft 365 components and then click Connect Office 365.
Figure 2. View into Office 365 components and initiating the connection to Office 365
Some of the specific Office 365 services that will be activated upon connecting include:
- Built-in threat protection alerts, such as suspicious inbox manipulation to detect business email compromises. Along with alerts on activity from a password-spray associated IP address enhanced analyzed across trillions of signals from Microsoft Threat Intelligence to name a few.
- Activity log data, which provides valuable insights into user actions within your organization. In a standard schema across all your organizations connected apps
- Advanced hunting, which enables you to proactively search for threats in your environment with the powerful capabilities of KQL across all your Defender workloads.
Step 2: Protecting non-Microsoft Apps
Defender for Cloud Apps can also connect to non-Microsoft apps like ServiceNow and Salesforce. By connecting your apps, you can extend threat protection to additional SaaS applications. In addition, you will also benefit from advanced posture capabilities like SaaS security posture management (SSPM). This enables you to proactively protect your organization by identifying misconfigurations, how to remediate them and as a result, reduce the potential attack surface.
Figure 3. Salesforce app misconfigurations surfaced in Microsoft Secure Score
These recommendations based on vendor practices and CIS benchmarks are surfaced in Microsoft Secure Score and provide direct links to vendor documentation.
Figure 4. Recommended action plan on how to remediate a specific misconfiguration
Step 3: Discovery Capabilities and Shadow IT
Shadow IT to the unauthorized use of cloud applications and services within an organization. This can create significant security risks, as these applications are often not subject to the same security controls as approved apps. Defender for Cloud Apps addresses this challenge with its robust discovery capabilities.
Discovering SaaS apps from Defender for Endpoint
Integrating Microsoft Defender for Endpoint is as easy as ticking a few checkboxes. This integration allows you to enforce app access policies and block access to unapproved applications.
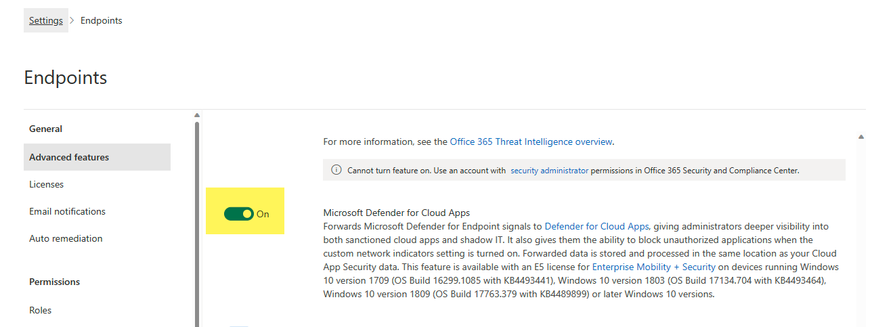
To connect Defender for Endpoint to Defender for Cloud Apps, in Microsoft 365 Defender navigate to Settings > Endpoint > Advanced Features and toggle the radio button to “on” for Microsoft Defender for Cloud Apps.
Figure 5. How to enable Defender for Cloud Apps in the Defender for Endpoint settings
Discovering SaaS apps from 3rd party Appliances
Microsoft Defender for Cloud Apps also offers direct integrations with 3rd parties such as ZScaler, iboss, Corrata, Menlo, Open Systems, further enhancing your organization's security posture and leveraging our shadow IT capabilities.
Step 4: Easy Protection for Non-Microsoft SaaS apps
By creating a discovery policy, you can identify and manage shadow IT within your organization. This will allow you to review those apps from the discovery dashboard to determine which actions to take such as sanctioning or unsanctioning an application.
Start by creating a tag that will flag newly discovered applications for review and an app discovery policy that will automatically apply the tag.
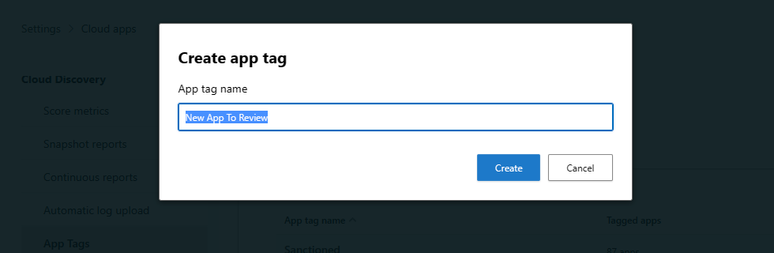
To create a custom tag open Microsoft 365 Defender and navigate to Settings > Cloud Apps > Cloud Discovery > App Tags then click Add app tag and provide a name such as “New App To Review”
Figure 6. How to create an app tag in Cloud Discovery
Once an app tag has been created from Microsoft 365 Defender navigate to Cloud Apps > Policies > Policy management and then select Create policy > App discovery policy.
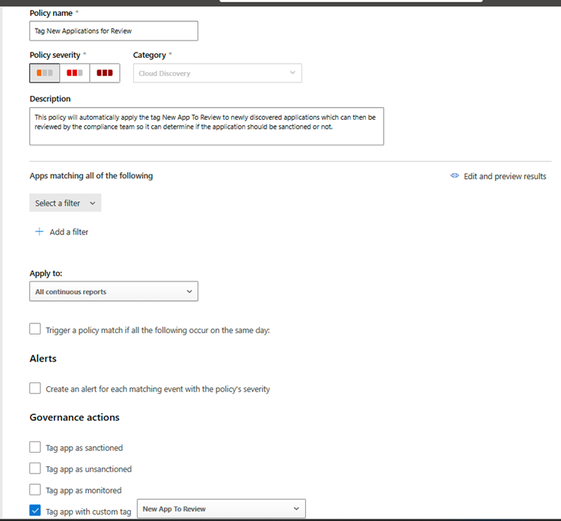
From this menu you can configure the policy by providing an applicable name and a description of what the policy is for (show in Figure 7) Under governance actions, you can see the app tag created in the previous step “New App To Review” has been selected.
Figure 7. Policy configuration using the new app tag shown in Figure 6
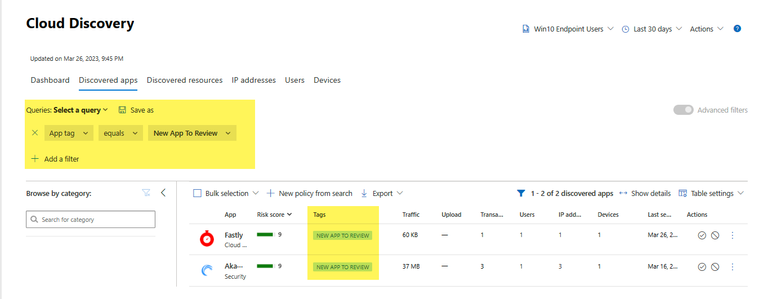
Once the policy has been configured and tags are applied automatically you can review by navigating to Cloud Apps > Cloud discovery > Discovered Apps and applying an advanced filter to look for apps with the “New Apps To Review” tag and you can also save the query for easy access for performing this in the future.
Figure 8. A view into tags that have the “new app to review,” tag applied
Review the list and decide which applications you want to sanction and authorize for use in your organization or choose to unsanction.
You can block unsanctioned apps by navigating to the Microsoft 365 Defender Portal > Settings > Cloud Apps > Cloud Discovery > Microsoft Defender for Endpoint and toggle the checkbox for “Enforce app access” to “on.” This will synchronize custom indicators to Defender for Endpoint automatically.
Figure 9. Enabling the Defender for Endpoint enforce app access setting
Conclusion
As the SaaS landscape continues to evolve, securing your organization's cloud applications is more important than ever. With Microsoft Defender for Cloud Apps, you can easily deploy comprehensive protection for your environment. As you embark on your journey to secure your organization's cloud applications, remember that Microsoft Defender for Cloud Apps is designed to make the process simple, efficient, and effective. By following these 5 steps, you can ensure your organization is well-equipped to face the ever-changing world of SaaS security.
Resources
To learn more about Microsoft Defender for Cloud Apps, check out our additional resources:
- Defender for Cloud Apps documentation
- What is SaaS Security?
- Defender for Cloud Apps website
Published on:
Learn more