Operations Task Management for Azure Alerts

Background
A few weeks back, a customer asked us for a way to effectively track the alerts that they get from Microsoft Sentinel and Defender for Cloud and ensure resolution. For organisations with an ITIL practice, this work is tracked by logging an Incident or a Problem ticket in an ITSM tool. But some organisations are a lot leaner (no ITIL practice and no ITSM tooling) and simply need something that works.
Solution Idea
And so the idea is to use Azure Boards as a simple Kanban board for the operations team to track work status. The tasks are created automatically as alerts/incidents are raised using Azure Logic Apps.
Workflow
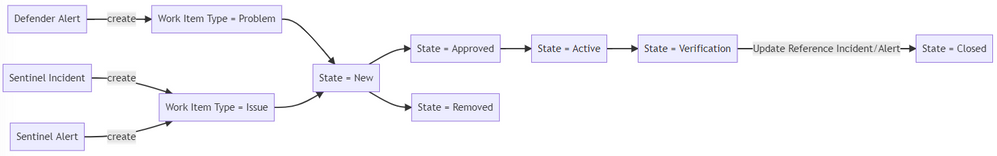
But before that, let's design the workflow:
This workflow is implemented using a custom inherited process in Azure Boards. In our implementation, we used
Work Item Type=Issue for Incident-type items, typically coming from Microsoft Sentinel, and
Work Item Type=Problem for Problem-type items, typically coming from Defender for Cloud recommendations
Since items are created automatically in Azure Boards, there is a need to clean up the alerts and reduce false positives. The work items are also first triaged and approved/removed before work is done. An extra verification stage is added for review before resolution.
The Logic Apps
Creating the logic apps was easy. Microsoft already provided templates to deploy these logic apps in our Azure Subscription.
- Create DevOps Tasks from Microsoft Defender - then duplicate this task and create separate triggers for Defender Alerts, Recommendations and Regulatory Compliance.
- Create DevOps Tasks from Microsoft Sentinel
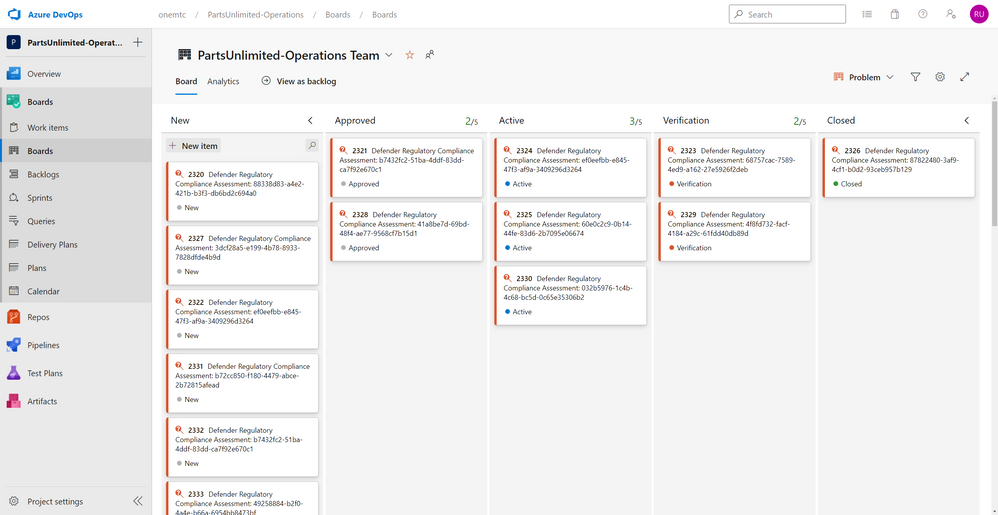
Here are some screenshots
Result
Future Work
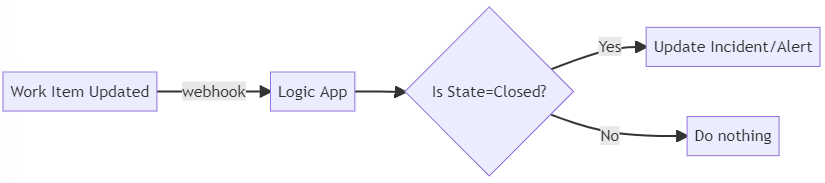
At the moment, we expect the work item owner to update/resolve the alert in Microsoft Defender/Sentinel manually as they complete the work. This can be optimised further by creating a webhook upon work item update, which in turn calls a logic app that resolves the linked Sentinel or Defender alert.
The Logic App can be implemented using the following connector actions:
- Close Defender Alert as benign/false-positive/true-positive
Update: This is implemented, see here.
To see the code, check out the GitHub Repo.
Published on:
Learn moreRelated posts
Automating Business PDFs Using Azure Document Intelligence and Power Automate
In today’s data-driven enterprises, critical business information often arrives in the form of PDFs—bank statements, invoices, policy document...
Azure Developer CLI (azd) Dec 2025 – Extensions Enhancements, Foundry Rebranding, and Azure Pipelines Improvements
This post announces the December release of the Azure Developer CLI (`azd`). The post Azure Developer CLI (azd) Dec 2025 – Extensions En...
Unlock the power of distributed graph databases with JanusGraph and Azure Apache Cassandra
Connecting the Dots: How Graph Databases Drive Innovation In today’s data-rich world, organizations face challenges that go beyond simple tabl...
Azure Boards integration with GitHub Copilot
A few months ago we introduced the Azure Boards integration with GitHub Copilot in private preview. The goal was simple: allow teams to take a...
Microsoft Dataverse – Monitor batch workloads with Azure Monitor Application Insights
We are announcing the ability to monitor batch workload telemetry in Azure Monitor Application Insights for finance and operations apps in Mic...
Copilot Studio: Connect An Azure SQL Database As Knowledge
Copilot Studio can connect to an Azure SQL database and use its structured data as ... The post Copilot Studio: Connect An Azure SQL Database ...
Retirement of Global Personal Access Tokens in Azure DevOps
In the new year, we’ll be retiring the Global Personal Access Token (PAT) type in Azure DevOps. Global PATs allow users to authenticate across...
Azure Cosmos DB vNext Emulator: Query and Observability Enhancements
The Azure Cosmos DB Linux-based vNext emulator (preview) is a local version of the Azure Cosmos DB service that runs as a Docker container on ...